monkeyDluffy6017 commented on code in PR #9322: URL: https://github.com/apache/apisix/pull/9322#discussion_r1185855271
########## docs/en/latest/tutorials/client-to-apisix-mtls.md: ########## @@ -193,6 +193,127 @@ curl --resolve "test.com:9443:127.0.0.1" https://test.com:9443/anything -k --cer Since we configured the [proxy-rewrite](../plugins/proxy-rewrite.md) plugin in the example, we can see that the response body contains the request body received upstream, containing the correct data. +## MTLS bypass based on regular expression matching against URI + +APISIX allows configuring an URI whitelist to bypass MTLS. +If the URI of a request is in the whitelist, then the client certificate will not be checked. +Note that other URIs of the associated SNI will get HTTP 400 response +instead of alert error in the SSL handshake phase, if the client certificate is missing or invalid. + +### Timing diagram + +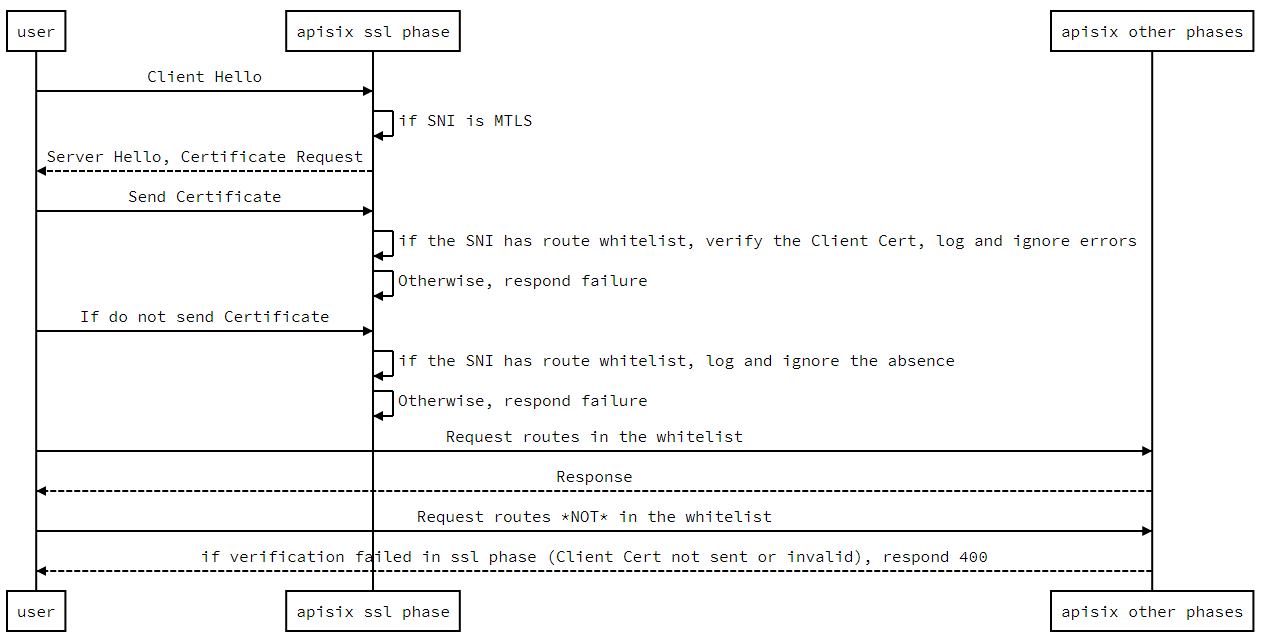 + +### Example + +```bash +curl http://127.0.0.1:9180/apisix/admin/routes/1 \ Review Comment: Maybe we should use three blocks, don't wrap them into one code block 1. config the route and ssl 2. if the client certificate is missing and the URI is not in the whitelis 3. the client certificate is missing, but the URI is in the whitelist -- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. To unsubscribe, e-mail: [email protected] For queries about this service, please contact Infrastructure at: [email protected]
