This is an automated email from the ASF dual-hosted git repository.
monkeydluffy pushed a commit to branch master
in repository https://gitbox.apache.org/repos/asf/apisix.git
The following commit(s) were added to refs/heads/master by this push:
new c757bafeb fix: remove conf server (#10012)
c757bafeb is described below
commit c757bafeb94315e03d3cc1ba4c88a0a94c081fd1
Author: jinhua luo <[email protected]>
AuthorDate: Fri Sep 1 19:39:33 2023 +0800
fix: remove conf server (#10012)
---
.github/workflows/build.yml | 2 +-
.github/workflows/centos7-ci.yml | 2 +-
.github/workflows/fips.yml | 2 +-
.github/workflows/gm-cron.yaml | 2 +-
.github/workflows/redhat-ci.yaml | 2 +-
apisix/cli/file.lua | 14 +-
apisix/cli/ngx_tpl.lua | 8 -
apisix/cli/ops.lua | 16 --
apisix/cli/schema.lua | 43 +--
apisix/cli/snippet.lua | 199 --------------
apisix/core/etcd.lua | 68 +----
conf/config-default.yaml | 28 +-
docs/en/latest/deployment-modes.md | 59 +----
t/APISIX.pm | 7 -
t/bin/gen_snippet.lua | 72 -----
t/chaos/killetcd/killetcd.go | 5 -
t/cli/test_access_log.sh | 6 -
t/cli/test_cmd.sh | 28 --
t/cli/test_deployment_control_plane.sh | 92 -------
t/cli/test_deployment_data_plane.sh | 28 +-
t/cli/test_deployment_mtls.sh | 88 -------
t/cli/test_deployment_traditional.sh | 51 ----
t/cli/test_etcd_mtls.sh | 2 +-
t/core/config_etcd.t | 57 +---
t/deployment/conf_server.t | 467 ---------------------------------
t/deployment/conf_server2.t | 161 ------------
t/deployment/mtls.t | 115 --------
27 files changed, 43 insertions(+), 1581 deletions(-)
diff --git a/.github/workflows/build.yml b/.github/workflows/build.yml
index c90a8e900..3f8f8ef48 100644
--- a/.github/workflows/build.yml
+++ b/.github/workflows/build.yml
@@ -31,7 +31,7 @@ jobs:
test_dir:
- t/plugin/[a-k]*
- t/plugin/[l-z]*
- - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/deployment t/discovery t/error_page t/misc
+ - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/discovery t/error_page t/misc
- t/node t/pubsub t/router t/script t/secret t/stream-node t/utils
t/wasm t/xds-library t/xrpc
runs-on: ${{ matrix.platform }}
diff --git a/.github/workflows/centos7-ci.yml b/.github/workflows/centos7-ci.yml
index dc08b0fd3..6428af72e 100644
--- a/.github/workflows/centos7-ci.yml
+++ b/.github/workflows/centos7-ci.yml
@@ -30,7 +30,7 @@ jobs:
test_dir:
- t/plugin/[a-k]*
- t/plugin/[l-z]*
- - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/deployment t/discovery t/error_page t/misc
+ - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/discovery t/error_page t/misc
- t/node t/pubsub t/router t/script t/secret t/stream-node t/utils
t/wasm t/xds-library
steps:
diff --git a/.github/workflows/fips.yml b/.github/workflows/fips.yml
index aeaf121f1..affa754bb 100644
--- a/.github/workflows/fips.yml
+++ b/.github/workflows/fips.yml
@@ -30,7 +30,7 @@ jobs:
# The RSA and SHA tests are fully covered by jwt-auth and hmac-auth
plugin tests, while other plugins only repeat such tests.
- t/plugin/jwt-auth2.t t/plugin/jwt-auth.t t/plugin/hmac-auth.t
# all SSL related core tests are covered by below two lists.
- - t/admin/ssl* t/admin/schema.t t/admin/upstream.t
t/config-center-yaml/ssl.t t/core/etcd-mtls.t t/core/config_etcd.t
t/deployment/conf_server.t t/misc/patch.t
+ - t/admin/ssl* t/admin/schema.t t/admin/upstream.t
t/config-center-yaml/ssl.t t/core/etcd-mtls.t t/core/config_etcd.t
t/misc/patch.t
- t/node/grpc-proxy-unary.t t/node/upstream-keepalive-pool.t
t/node/upstream-websocket.t t/node/client-mtls.t t/node/upstream-mtls.t
t/pubsub/kafka.t t/router/radixtree-sni2.t t/router/multi-ssl-certs.t
t/router/radixtree-sni.t t/stream-node/mtls.t t/stream-node/tls.t
t/stream-node/upstream-tls.t t/stream-node/sni.t
- t/fips
diff --git a/.github/workflows/gm-cron.yaml b/.github/workflows/gm-cron.yaml
index 669a21798..e0500ecd6 100644
--- a/.github/workflows/gm-cron.yaml
+++ b/.github/workflows/gm-cron.yaml
@@ -20,7 +20,7 @@ jobs:
test_dir:
- t/plugin/[a-k]*
- t/plugin/[l-z]*
- - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/deployment t/discovery t/error_page t/misc
+ - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/discovery t/error_page t/misc
- t/node t/pubsub t/router t/script t/stream-node t/utils t/wasm
t/xds-library t/xrpc
runs-on: ${{ matrix.platform }}
diff --git a/.github/workflows/redhat-ci.yaml b/.github/workflows/redhat-ci.yaml
index cf03ae002..ee40d0d64 100644
--- a/.github/workflows/redhat-ci.yaml
+++ b/.github/workflows/redhat-ci.yaml
@@ -26,7 +26,7 @@ jobs:
test_dir:
- t/plugin/[a-k]*
- t/plugin/[l-z]*
- - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/deployment t/discovery t/error_page t/misc
+ - t/admin t/cli t/config-center-yaml t/control t/core t/debug
t/discovery t/error_page t/misc
- t/node t/pubsub t/router t/script t/secret t/stream-node t/utils
t/wasm t/xds-library
steps:
diff --git a/apisix/cli/file.lua b/apisix/cli/file.lua
index 149c4e913..94e790db6 100644
--- a/apisix/cli/file.lua
+++ b/apisix/cli/file.lua
@@ -292,26 +292,14 @@ function _M.read_yaml_conf(apisix_home)
default_conf.apisix.enable_admin = true
elseif default_conf.deployment.role == "data_plane" then
+ default_conf.etcd = default_conf.deployment.etcd
if default_conf.deployment.role_data_plane.config_provider ==
"yaml" then
default_conf.deployment.config_provider = "yaml"
elseif default_conf.deployment.role_data_plane.config_provider ==
"xds" then
default_conf.deployment.config_provider = "xds"
- else
- default_conf.etcd =
default_conf.deployment.role_data_plane.control_plane
end
default_conf.apisix.enable_admin = false
end
-
- if default_conf.etcd and default_conf.deployment.certs then
- -- copy certs configuration to keep backward compatible
- local certs = default_conf.deployment.certs
- local etcd = default_conf.etcd
- if not etcd.tls then
- etcd.tls = {}
- end
- etcd.tls.cert = certs.cert
- etcd.tls.key = certs.cert_key
- end
end
if default_conf.deployment.config_provider == "yaml" then
diff --git a/apisix/cli/ngx_tpl.lua b/apisix/cli/ngx_tpl.lua
index ab8407b57..4b4d94681 100644
--- a/apisix/cli/ngx_tpl.lua
+++ b/apisix/cli/ngx_tpl.lua
@@ -115,10 +115,6 @@ http {
}
}
{% end %}
-
- {% if conf_server then %}
- {* conf_server *}
- {% end %}
}
{% end %}
@@ -576,10 +572,6 @@ http {
}
{% end %}
- {% if conf_server then %}
- {* conf_server *}
- {% end %}
-
{% if deployment_role ~= "control_plane" then %}
{% if enabled_plugins["proxy-cache"] then %}
diff --git a/apisix/cli/ops.lua b/apisix/cli/ops.lua
index 8ba08c7fa..de82276f8 100644
--- a/apisix/cli/ops.lua
+++ b/apisix/cli/ops.lua
@@ -21,7 +21,6 @@ local file = require("apisix.cli.file")
local schema = require("apisix.cli.schema")
local ngx_tpl = require("apisix.cli.ngx_tpl")
local cli_ip = require("apisix.cli.ip")
-local snippet = require("apisix.cli.snippet")
local profile = require("apisix.core.profile")
local template = require("resty.template")
local argparse = require("argparse")
@@ -533,11 +532,6 @@ Please modify "admin_key" in conf/config.yaml .
proxy_mirror_timeouts = yaml_conf.plugin_attr["proxy-mirror"].timeout
end
- local conf_server, err = snippet.generate_conf_server(env, yaml_conf)
- if err then
- util.die(err, "\n")
- end
-
if yaml_conf.deployment and yaml_conf.deployment.role then
local role = yaml_conf.deployment.role
env.deployment_role = role
@@ -568,7 +562,6 @@ Please modify "admin_key" in conf/config.yaml .
control_server_addr = control_server_addr,
prometheus_server_addr = prometheus_server_addr,
proxy_mirror_timeouts = proxy_mirror_timeouts,
- conf_server = conf_server,
}
if not yaml_conf.apisix then
@@ -814,15 +807,6 @@ local function start(env, ...)
-- start a new APISIX instance
- local conf_server_sock_path = env.apisix_home .. "/conf/config_listen.sock"
- if pl_path.exists(conf_server_sock_path) then
- -- remove stale sock (if exists) so that APISIX can start
- local ok, err = os_remove(conf_server_sock_path)
- if not ok then
- util.die("failed to remove stale conf server sock file, error: ",
err)
- end
- end
-
local parser = argparse()
parser:argument("_", "Placeholder")
parser:option("-c --config", "location of customized config.yaml")
diff --git a/apisix/cli/schema.lua b/apisix/cli/schema.lua
index 59bb9acc7..6f6450b46 100644
--- a/apisix/cli/schema.lua
+++ b/apisix/cli/schema.lua
@@ -383,60 +383,23 @@ local deployment_schema = {
config_provider = {
enum = {"etcd"}
},
- conf_server = {
- properties = {
- listen = {
- type = "string",
- default = "0.0.0.0:9280",
- },
- cert = { type = "string" },
- cert_key = { type = "string" },
- client_ca_cert = { type = "string" },
- },
- required = {"cert", "cert_key"}
- },
- },
- required = {"config_provider", "conf_server"}
- },
- certs = {
- properties = {
- cert = { type = "string" },
- cert_key = { type = "string" },
- trusted_ca_cert = { type = "string" },
- },
- dependencies = {
- cert = {
- required = {"cert_key"},
- },
},
- default = {},
+ required = {"config_provider"}
},
},
required = {"etcd", "role_control_plane"}
},
data_plane = {
properties = {
+ etcd = etcd_schema,
role_data_plane = {
properties = {
config_provider = {
- enum = {"control_plane", "yaml", "xds"}
+ enum = {"etcd", "yaml", "xds"}
},
},
required = {"config_provider"}
},
- certs = {
- properties = {
- cert = { type = "string" },
- cert_key = { type = "string" },
- trusted_ca_cert = { type = "string" },
- },
- dependencies = {
- cert = {
- required = {"cert_key"},
- },
- },
- default = {},
- },
},
required = {"role_data_plane"}
}
diff --git a/apisix/cli/snippet.lua b/apisix/cli/snippet.lua
deleted file mode 100644
index 16515b77e..000000000
--- a/apisix/cli/snippet.lua
+++ /dev/null
@@ -1,199 +0,0 @@
---
--- Licensed to the Apache Software Foundation (ASF) under one or more
--- contributor license agreements. See the NOTICE file distributed with
--- this work for additional information regarding copyright ownership.
--- The ASF licenses this file to You under the Apache License, Version 2.0
--- (the "License"); you may not use this file except in compliance with
--- the License. You may obtain a copy of the License at
---
--- http://www.apache.org/licenses/LICENSE-2.0
---
--- Unless required by applicable law or agreed to in writing, software
--- distributed under the License is distributed on an "AS IS" BASIS,
--- WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
--- See the License for the specific language governing permissions and
--- limitations under the License.
---
-local template = require("resty.template")
-local pl_path = require("pl.path")
-local ipairs = ipairs
-
-
--- this module provide methods to generate snippets which will be used in the
nginx.conf template
-local _M = {}
-local conf_server_tpl = [[
-upstream apisix_conf_backend {
- server 0.0.0.0:80;
- balancer_by_lua_block {
- local conf_server = require("apisix.conf_server")
- conf_server.balancer()
- }
- keepalive 320;
- keepalive_requests 1000;
- keepalive_timeout 60s;
-}
-
-{% if trusted_ca_cert then %}
-lua_ssl_trusted_certificate {* trusted_ca_cert *};
-{% end %}
-
-server {
- {% if control_plane then %}
- {% if directive_prefix == "grpc" then %}
- listen {* control_plane.listen *} ssl http2;
- {% else %}
- listen {* control_plane.listen *} ssl;
- {% end %}
- ssl_certificate {* control_plane.cert *};
- ssl_certificate_key {* control_plane.cert_key *};
-
- {% if control_plane.client_ca_cert then %}
- ssl_verify_client on;
- ssl_client_certificate {* control_plane.client_ca_cert *};
- {% end %}
-
- {% else %}
- {% if directive_prefix == "grpc" then %}
- listen unix:{* home *}/conf/config_listen.sock http2;
- {% else %}
- listen unix:{* home *}/conf/config_listen.sock;
- {% end %}
- {% end %}
-
- access_log off;
-
- set $upstream_host '';
-
- access_by_lua_block {
- local conf_server = require("apisix.conf_server")
- conf_server.access()
- }
-
- location / {
- {% if enable_https then %}
- {* directive_prefix *}_pass {* scheme_name *}s://apisix_conf_backend;
- {* directive_prefix *}_ssl_protocols TLSv1.2 TLSv1.3;
- {* directive_prefix *}_ssl_server_name on;
-
- {% if etcd_tls_verify then %}
- {* directive_prefix *}_ssl_verify on;
- {* directive_prefix *}_ssl_trusted_certificate {*
ssl_trusted_certificate *};
- {% end %}
-
- {% if sni then %}
- {* directive_prefix *}_ssl_name {* sni *};
- {% else %}
- {* directive_prefix *}_ssl_name $upstream_host;
- {% end %}
-
- {% if client_cert then %}
- {* directive_prefix *}_ssl_certificate {* client_cert *};
- {* directive_prefix *}_ssl_certificate_key {* client_cert_key *};
- {% end %}
-
- {% else %}
- {* directive_prefix *}_pass {* scheme_name *}://apisix_conf_backend;
- {% end %}
-
- {% if scheme_name == "http" then %}
- proxy_http_version 1.1;
- proxy_set_header Connection "";
- {% end %}
-
- {* directive_prefix *}_set_header Host $upstream_host;
- {* directive_prefix *}_next_upstream error timeout non_idempotent
- http_500 http_502 http_503 http_504;
- }
-
- log_by_lua_block {
- local conf_server = require("apisix.conf_server")
- conf_server.log()
- }
-}
-]]
-
-
-function _M.generate_conf_server(env, conf)
- if not (conf.deployment and (
- conf.deployment.role == "traditional" or
- conf.deployment.role == "control_plane"))
- then
- return nil, nil
- end
-
- -- we use proxy even the role is traditional so that we can test the proxy
in daily dev
- local etcd = conf.deployment.etcd
- local servers = etcd.host
- local enable_https = false
- local prefix = "https://";
- if servers[1]:find(prefix, 1, true) then
- enable_https = true
- end
-
- for i, s in ipairs(servers) do
- if (s:find(prefix, 1, true) ~= nil) ~= enable_https then
- return nil, "all nodes in the etcd cluster should enable/disable
TLS together"
- end
-
- local _, to = s:find("://", 1, true)
- if not to then
- return nil, "bad etcd endpoint format"
- end
- end
-
- local control_plane
- if conf.deployment.role == "control_plane" then
- control_plane = conf.deployment.role_control_plane.conf_server
- control_plane.cert = pl_path.abspath(control_plane.cert)
- control_plane.cert_key = pl_path.abspath(control_plane.cert_key)
-
- if control_plane.client_ca_cert then
- control_plane.client_ca_cert =
pl_path.abspath(control_plane.client_ca_cert)
- end
- end
-
- local trusted_ca_cert
- if conf.deployment.certs then
- if conf.deployment.certs.trusted_ca_cert then
- trusted_ca_cert =
pl_path.abspath(conf.deployment.certs.trusted_ca_cert)
- end
- end
-
- local conf_render = template.compile(conf_server_tpl)
- local tls = etcd.tls
- local client_cert
- local client_cert_key
- local ssl_trusted_certificate
- local etcd_tls_verify
- if tls then
- if tls.cert then
- client_cert = pl_path.abspath(tls.cert)
- client_cert_key = pl_path.abspath(tls.key)
- end
-
- etcd_tls_verify = tls.verify
- if enable_https and etcd_tls_verify then
- if not conf.apisix.ssl.ssl_trusted_certificate then
- return nil, "should set ssl_trusted_certificate if etcd tls
verify is enabled"
- end
- ssl_trusted_certificate =
pl_path.abspath(conf.apisix.ssl.ssl_trusted_certificate)
- end
- end
-
- return conf_render({
- sni = tls and tls.sni,
- home = env.apisix_home or ".",
- control_plane = control_plane,
- enable_https = enable_https,
- client_cert = client_cert,
- client_cert_key = client_cert_key,
- trusted_ca_cert = trusted_ca_cert,
- etcd_tls_verify = etcd_tls_verify,
- ssl_trusted_certificate = ssl_trusted_certificate,
- scheme_name = "http",
- directive_prefix = "proxy",
- })
-end
-
-
-return _M
diff --git a/apisix/core/etcd.lua b/apisix/core/etcd.lua
index 6d041016e..5cd103858 100644
--- a/apisix/core/etcd.lua
+++ b/apisix/core/etcd.lua
@@ -31,21 +31,12 @@ local ipairs = ipairs
local setmetatable = setmetatable
local string = string
local tonumber = tonumber
-local ngx_config_prefix = ngx.config.prefix()
-local ngx_socket_tcp = ngx.socket.tcp
local ngx_get_phase = ngx.get_phase
-local is_http = ngx.config.subsystem == "http"
local _M = {}
-local function has_mtls_support()
- local s = ngx_socket_tcp()
- return s.tlshandshake ~= nil
-end
-
-
local function _new(etcd_conf)
local prefix = etcd_conf.prefix
etcd_conf.http_host = etcd_conf.host
@@ -117,64 +108,7 @@ local function new()
etcd_conf.trusted_ca = local_conf.apisix.ssl.ssl_trusted_certificate
end
- local proxy_by_conf_server = false
-
- if local_conf.deployment then
- if local_conf.deployment.role == "traditional"
- -- we proxy the etcd requests in traditional mode so we can test
the CP's behavior in
- -- daily development. However, a stream proxy can't be the CP.
- -- Hence, generate a HTTP conf server to proxy etcd requests in
stream proxy is
- -- unnecessary and inefficient.
- and is_http
- then
- local sock_prefix = ngx_config_prefix
- etcd_conf.unix_socket_proxy =
- "unix:" .. sock_prefix .. "/conf/config_listen.sock"
- etcd_conf.host = {"http://127.0.0.1:2379"}
- proxy_by_conf_server = true
-
- elseif local_conf.deployment.role == "control_plane" then
- local addr =
local_conf.deployment.role_control_plane.conf_server.listen
- etcd_conf.host = {"https://"; .. addr}
- etcd_conf.tls = {
- verify = false,
- }
-
- if has_mtls_support() and local_conf.deployment.certs.cert then
- local cert = local_conf.deployment.certs.cert
- local cert_key = local_conf.deployment.certs.cert_key
- etcd_conf.tls.cert = cert
- etcd_conf.tls.key = cert_key
- end
-
- proxy_by_conf_server = true
-
- elseif local_conf.deployment.role == "data_plane" then
- if has_mtls_support() and local_conf.deployment.certs.cert then
- local cert = local_conf.deployment.certs.cert
- local cert_key = local_conf.deployment.certs.cert_key
-
- if not etcd_conf.tls then
- etcd_conf.tls = {}
- end
-
- etcd_conf.tls.cert = cert
- etcd_conf.tls.key = cert_key
- end
- end
-
- if local_conf.deployment.certs and
local_conf.deployment.certs.trusted_ca_cert then
- etcd_conf.trusted_ca = local_conf.deployment.certs.trusted_ca_cert
- end
- end
-
- -- if an unhealthy etcd node is selected in a single admin read/write etcd
operation,
- -- the retry mechanism for health check can select another healthy etcd
node
- -- to complete the read/write etcd operation.
- if proxy_by_conf_server then
- -- health check is done in conf server
- health_check.disable()
- elseif not health_check.conf then
+ if not health_check.conf then
health_check.init({
max_fails = 1,
retry = true,
diff --git a/conf/config-default.yaml b/conf/config-default.yaml
index dd114558b..06640900c 100755
--- a/conf/config-default.yaml
+++ b/conf/config-default.yaml
@@ -618,29 +618,11 @@ deployment: # Deployment configurations
role_traditional:
config_provider: etcd # Set the configuration center.
- # role_data_plane: # Set data plane details if role is data_plane.
- # config_provider: control_plane # Set the configuration
center: control_plane, or yaml.
- # control_plane: # Set control plane details if
config_provider is control_plane.
- # host: # Set the address of control
plane.
- # - https://${control_plane_IP}:9280
- # prefix: /apisix # Set etcd prefix.
- # timeout: 30 # Set timeout in seconds.
- # certs:
- # cert: /path/to/client.crt # Set path to the client
certificate.
- # cert_key: /path/to/client.key # Set path to the client key.
- # trusted_ca_cert: /path/to/ca.crt # Set path to the trusted CA
certificate.
-
- # role_control_plane: # Set control plane details if role is
control_plane.
- # config_provider: etcd # Set the configuration center.
- # conf_server:
- # listen: 0.0.0.0:9280 # Set the address of the conf
server.
- # cert: /path/to/server.crt # Set path to the server
certificate.
- # cert_key: /path/to/server.key # Set path to the server key.
- # client_ca_cert: /path/to/ca.crt # Set path to the trusted CA
certificate.
- # certs:
- # cert: /path/to/client.crt # Set path to the client
certificate.
- # cert_key: /path/to/client.key # Set path to the client key.
- # trusted_ca_cert: /path/to/ca.crt # Set path to the trusted CA
certificate.
+ #role_data_plane: # Set data plane details if role is data_plane.
+ # config_provider: etcd # Set the configuration center: etcd, xds, or
yaml.
+
+ #role_control_plane: # Set control plane details if role is
control_plane.
+ # config_provider: etcd # Set the configuration center.
admin: # Admin API
admin_key_required: true # Enable Admin API authentication by default
for security.
diff --git a/docs/en/latest/deployment-modes.md
b/docs/en/latest/deployment-modes.md
index 9f75a1d99..bc195121c 100644
--- a/docs/en/latest/deployment-modes.md
+++ b/docs/en/latest/deployment-modes.md
@@ -39,10 +39,6 @@ Each of these deployment modes are explained in detail below.
In the traditional deployment mode, one instance of APISIX will be both the
`data_plane` and the `control_plane`.
-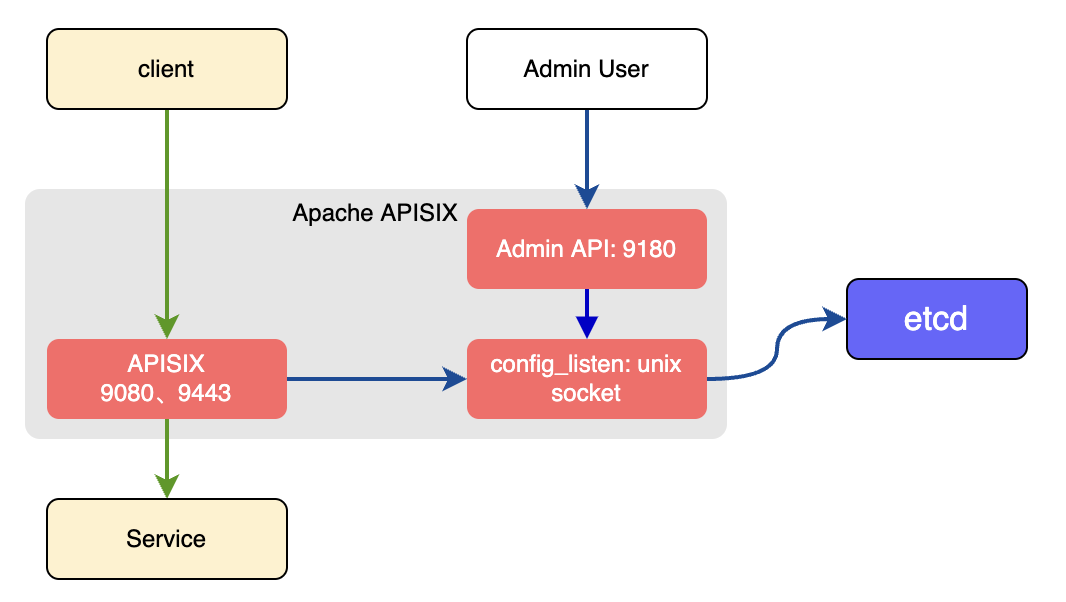
-
-There will be a conf server that listens on the UNIX socket and acts as a
proxy between APISIX and etcd. Both the data and the control planes connect to
this conf server via HTTP.
-
An example configuration of the traditional deployment mode is shown below:
```yaml title="conf/config.yaml"
@@ -73,16 +69,9 @@ The instance of APISIX deployed as the traditional role will:
In the decoupled deployment mode the `data_plane` and `control_plane`
instances of APISIX are deployed separately, i.e., one instance of APISIX is
configured to be a *data plane* and the other to be a *control plane*.
-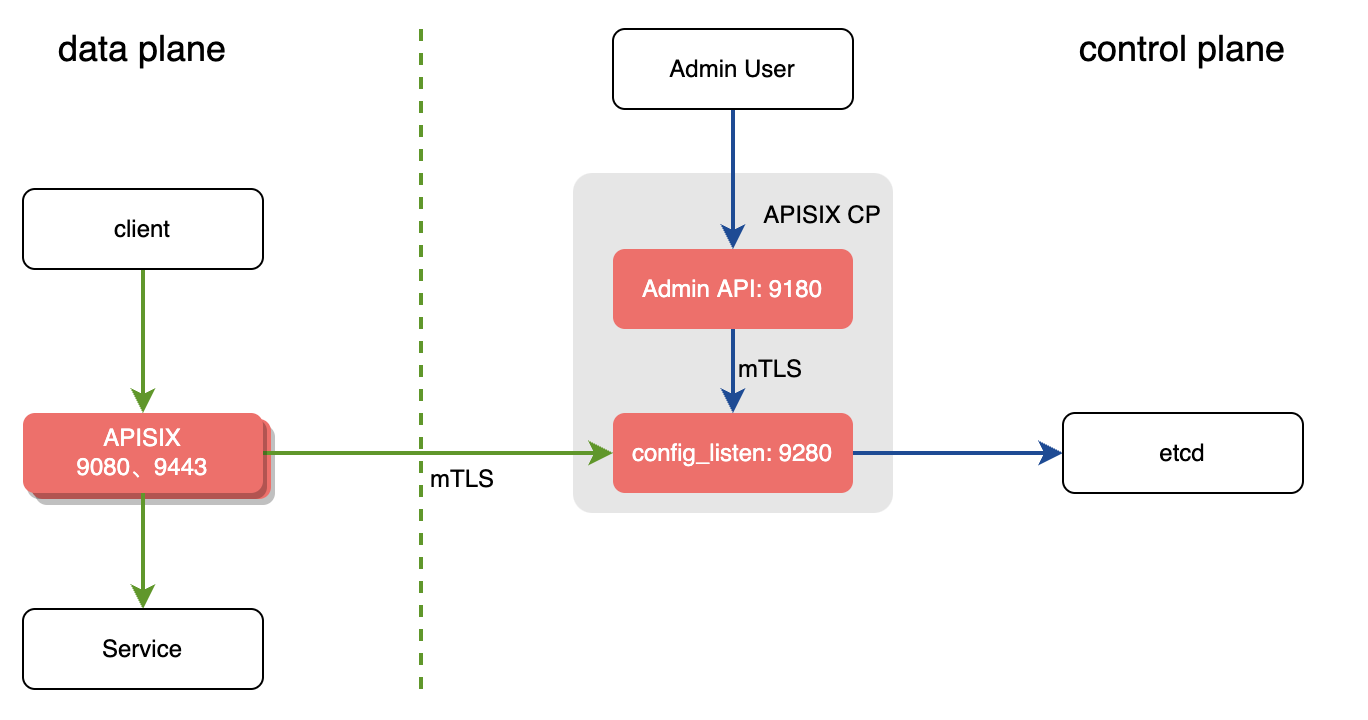
-
The instance of APISIX deployed as the data plane will:
-1. Fetch the configuration from the *control plane*. The default port is
`9280`.
-2. Performs a health check on all configured control plane addresses before
starting the service.
- 1. If the control plane addresses are unavailable, the startup fails and an
exception is thrown.
- 2. If at least one control plane address is available, it prints the
unhealthy control planes logs, and starts the APISIX service.
- 3. If all control planes are normal, APISIX service is started normally.
-3. Once the service is started, it will handle the user requests.
+Once the service is started, it will handle the user requests.
The example below shows the configuration of an APISIX instance as *data
plane* in the decoupled mode:
@@ -90,23 +79,13 @@ The example below shows the configuration of an APISIX
instance as *data plane*
deployment:
role: data_plane
role_data_plane:
- config_provider: control_plane
- control_plane:
- host:
- - https://${Control_Plane_IP}:9280
- prefix: /apisix
- timeout: 30
- certs:
- cert: /path/to/client.crt
- cert_key: /path/to/client.key
- trusted_ca_cert: /path/to/ca.crt
+ config_provider: etcd
#END
```
The instance of APISIX deployed as the control plane will:
1. Listen on port `9180` and handle Admin API requests.
-2. Provide the conf server which will listen on port `9280`. Both the control
plane and the data plane will connect to this via HTTPS enforced by mTLS.
The example below shows the configuration of an APISIX instance as *control
plane* in the decoupled mode:
@@ -115,48 +94,14 @@ deployment:
role: control_plane
role_control_plane:
config_provider: etcd
- conf_server:
- listen: 0.0.0.0:9280
- cert: /path/to/server.crt
- cert_key: /path/to/server.key
- client_ca_cert: /path/to/ca.crt
etcd:
host:
- https://${etcd_IP}:${etcd_Port}
prefix: /apisix
timeout: 30
- certs:
- cert: /path/to/client.crt
- cert_key: /path/to/client.key
- trusted_ca_cert: /path/to/ca.crt
#END
```
-:::tip
-
-As OpenResty <= 1.21.4 does not support sending mTLS requests, to accept
connections from APISIX running on these OpenResty versions, you need to
disable the client certificate verification in the control plane instance as
shown below:
-
-```yaml title="conf/config.yaml"
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- listen: 0.0.0.0:9280
- cert: /path/to/server.crt
- cert_key: /path/to/server.key
- etcd:
- host:
- - https://${etcd_IP}:${etcd_Port}
- prefix: /apisix
- timeout: 30
- certs:
- trusted_ca_cert: /path/to/ca.crt
-#END
-```
-
-:::
-
## Standalone
Turning on the APISIX node in Standalone mode will no longer use the default
etcd as the configuration center.
diff --git a/t/APISIX.pm b/t/APISIX.pm
index a2749f041..b8e288abc 100644
--- a/t/APISIX.pm
+++ b/t/APISIX.pm
@@ -33,13 +33,6 @@ my $nginx_binary = $ENV{'TEST_NGINX_BINARY'} || 'nginx';
$ENV{TEST_NGINX_HTML_DIR} ||= html_dir();
$ENV{TEST_NGINX_FAST_SHUTDOWN} ||= 1;
-Test::Nginx::Socket::set_http_config_filter(sub {
- my $config = shift;
- my $snippet = `$apisix_home/t/bin/gen_snippet.lua conf_server`;
- $config .= $snippet;
- return $config;
-});
-
sub read_file($) {
my $infile = shift;
open my $in, "$apisix_home/$infile"
diff --git a/t/bin/gen_snippet.lua b/t/bin/gen_snippet.lua
deleted file mode 100755
index b2ab349be..000000000
--- a/t/bin/gen_snippet.lua
+++ /dev/null
@@ -1,72 +0,0 @@
-#!/usr/bin/env luajit
---
--- Licensed to the Apache Software Foundation (ASF) under one or more
--- contributor license agreements. See the NOTICE file distributed with
--- this work for additional information regarding copyright ownership.
--- The ASF licenses this file to You under the Apache License, Version 2.0
--- (the "License"); you may not use this file except in compliance with
--- the License. You may obtain a copy of the License at
---
--- http://www.apache.org/licenses/LICENSE-2.0
---
--- Unless required by applicable law or agreed to in writing, software
--- distributed under the License is distributed on an "AS IS" BASIS,
--- WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
--- See the License for the specific language governing permissions and
--- limitations under the License.
---
--- this script generates Nginx configuration in the test
--- so we can test some features with test-nginx
-local pkg_cpath_org = package.cpath
-local pkg_path_org = package.path
-local pkg_cpath = "deps/lib64/lua/5.1/?.so;deps/lib/lua/5.1/?.so;"
-local pkg_path = "deps/share/lua/5.1/?.lua;"
--- modify the load path to load our dependencies
-package.cpath = pkg_cpath .. pkg_cpath_org
-package.path = pkg_path .. pkg_path_org
-
-
-local file = require("apisix.cli.file")
-local schema = require("apisix.cli.schema")
-local snippet = require("apisix.cli.snippet")
-local util = require("apisix.cli.util")
-local yaml_conf, err = file.read_yaml_conf("t/servroot")
-if not yaml_conf then
- error(err)
-end
-
-if yaml_conf.deployment.role == "data_plane" and
- yaml_conf.deployment.config_provider == "yaml"
- or yaml_conf.deployment.config_provider == "xds" then
- return
-end
-
-local ok, err = schema.validate(yaml_conf)
-if not ok then
- error(err)
-end
-
-local or_info, err = util.execute_cmd("openresty -V 2>&1")
-if not or_info then
- error("failed to exec cmd \'openresty -V 2>&1\', err: " .. err)
-end
-
-local use_apisix_base = true
-if not or_info:find("apisix-nginx-module", 1, true) then
- use_apisix_base = false
-end
-
-local res, err
-if arg[1] == "conf_server" then
- res, err = snippet.generate_conf_server(
- {
- apisix_home = "t/servroot/",
- use_apisix_base = use_apisix_base,
- },
- yaml_conf)
-end
-
-if not res then
- error(err or "none")
-end
-print(res)
diff --git a/t/chaos/killetcd/killetcd.go b/t/chaos/killetcd/killetcd.go
index 4f92cd9cc..069b66581 100644
--- a/t/chaos/killetcd/killetcd.go
+++ b/t/chaos/killetcd/killetcd.go
@@ -140,17 +140,12 @@ var _ = ginkgo.Describe("Test Get Success When Etcd Got
Killed", func() {
// fail to set route since etcd is all killed
// while get route could still succeed
ginkgo.It("get stats after kill etcd", func() {
- timeStart := time.Now()
utils.SetRoute(e, httpexpect.Status5xx)
utils.GetRoute(eDataPanel, http.StatusOK)
utils.TestPrometheusEtcdMetric(ePrometheus, 0)
bandwidthAfter, durationAfter =
utils.GetEgressBandwidthPerSecond(ePrometheus)
bpsAfter = bandwidthAfter / durationAfter
-
- errorLog, err := utils.Log(apisixPod, cliSet.KubeCli, timeStart)
- gomega.Expect(err).To(gomega.BeNil())
- gomega.Ω(errorLog).Should(gomega.ContainSubstring("invalid
response code: 502"))
})
ginkgo.It("ingress bandwidth per second not change much", func() {
diff --git a/t/cli/test_access_log.sh b/t/cli/test_access_log.sh
index 58faba74e..01dda603a 100755
--- a/t/cli/test_access_log.sh
+++ b/t/cli/test_access_log.sh
@@ -91,12 +91,6 @@ if [ $count_test_access_log -eq 1 ]; then
exit 1
fi
-count_access_log_off=`grep -c "access_log off;" conf/nginx.conf || true`
-if [ $count_access_log_off -ne 5 ]; then
- echo "failed: nginx.conf file doesn't find access_log off; when disable
access log"
- exit 1
-fi
-
make run
sleep 0.1
curl http://127.0.0.1:9080/hi
diff --git a/t/cli/test_cmd.sh b/t/cli/test_cmd.sh
index c02b4dbee..953b6dc4a 100755
--- a/t/cli/test_cmd.sh
+++ b/t/cli/test_cmd.sh
@@ -21,34 +21,6 @@
git checkout conf/config.yaml
-# remove stale conf server sock
-touch conf/config_listen.sock
-./bin/apisix start
-sleep 0.5
-./bin/apisix stop
-sleep 0.5
-
-if [ -e conf/config_listen.sock ]; then
- echo "failed: should remove stale conf server sock"
- exit 1
-fi
-
-# don't remove stale conf server sock when APISIX is running
-./bin/apisix start
-sleep 0.5
-./bin/apisix start
-sleep 0.5
-
-if [ ! -e conf/config_listen.sock ]; then
- echo "failed: should not remove stale conf server sock"
- exit 1
-fi
-
-./bin/apisix stop
-sleep 0.5
-
-echo "passed: stale conf server sock removed"
-
# check restart with old nginx.pid exist
echo "-1" > logs/nginx.pid
out=$(./bin/apisix start 2>&1 || true)
diff --git a/t/cli/test_deployment_control_plane.sh
b/t/cli/test_deployment_control_plane.sh
index 58858f41f..ed3a062a8 100755
--- a/t/cli/test_deployment_control_plane.sh
+++ b/t/cli/test_deployment_control_plane.sh
@@ -19,57 +19,6 @@
. ./t/cli/common.sh
-echo '
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- cert: t/certs/mtls_server.crt
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
-' > conf/config.yaml
-
-out=$(make init 2>&1 || true)
-if ! echo "$out" | grep 'property "cert_key" is required'; then
- echo "failed: should check deployment schema during init"
- exit 1
-fi
-
-echo "passed: should check deployment schema during init"
-
-# The 'admin.apisix.dev' is injected by ci/common.sh@set_coredns
-echo '
-apisix:
- enable_admin: false
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- listen: admin.apisix.dev:12345
- cert: t/certs/mtls_server.crt
- cert_key: t/certs/mtls_server.key
- admin:
- https_admin: "abc"
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- certs:
- trusted_ca_cert: t/certs/mtls_ca.crt
-' > conf/config.yaml
-
-out=$(make init 2>&1 || true)
-if ! echo "$out" | grep 'property "https_admin" validation failed: wrong type:
expected boolean, got string'; then
- echo "failed: should check deployment schema during init"
- exit 1
-fi
-
-echo "passed: should check deployment schema during init"
-
# The 'admin.apisix.dev' is injected by ci/common.sh@set_coredns
echo '
apisix:
@@ -78,23 +27,16 @@ deployment:
role: control_plane
role_control_plane:
config_provider: etcd
- conf_server:
- listen: admin.apisix.dev:12345
- cert: t/certs/mtls_server.crt
- cert_key: t/certs/mtls_server.key
etcd:
prefix: "/apisix"
host:
- http://127.0.0.1:2379
- certs:
- trusted_ca_cert: t/certs/mtls_ca.crt
' > conf/config.yaml
make run
sleep 1
code=$(curl -o /dev/null -s -w %{http_code}
http://127.0.0.1:9180/apisix/admin/routes -H 'X-API-KEY:
edd1c9f034335f136f87ad84b625c8f1')
-make stop
if [ ! $code -eq 200 ]; then
echo "failed: control_plane should enable Admin API"
@@ -103,40 +45,6 @@ fi
echo "passed: control_plane should enable Admin API"
-# use https
-# The 'admin.apisix.dev' is injected by ci/common.sh@set_coredns
-echo '
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- listen: admin.apisix.dev:12345
- cert: t/certs/mtls_server.crt
- cert_key: t/certs/mtls_server.key
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- certs:
- cert: t/certs/mtls_client.crt
- cert_key: t/certs/mtls_client.key
- trusted_ca_cert: t/certs/mtls_ca.crt
-' > conf/config.yaml
-
-make run
-sleep 1
-
-code=$(curl -o /dev/null -s -w %{http_code}
http://127.0.0.1:9180/apisix/admin/routes -H 'X-API-KEY:
edd1c9f034335f136f87ad84b625c8f1')
-
-if [ ! $code -eq 200 ]; then
- make stop
- echo "failed: could not work with etcd"
- exit 1
-fi
-
-echo "passed: work well with etcd in control plane"
-
curl -i http://127.0.0.1:9180/apisix/admin/routes/1 -H 'X-API-KEY:
edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '
{
"upstream": {
diff --git a/t/cli/test_deployment_data_plane.sh
b/t/cli/test_deployment_data_plane.sh
index ef5ef61e3..b7edb0e24 100755
--- a/t/cli/test_deployment_data_plane.sh
+++ b/t/cli/test_deployment_data_plane.sh
@@ -27,14 +27,14 @@ echo '
deployment:
role: data_plane
role_data_plane:
- config_provider: control_plane
- control_plane:
- host:
- - https://127.0.0.1:12379
- prefix: "/apisix"
- timeout: 30
- tls:
- verify: false
+ config_provider: etcd
+ etcd:
+ host:
+ - https://127.0.0.1:12379
+ prefix: "/apisix"
+ timeout: 30
+ tls:
+ verify: false
' > conf/config.yaml
make run
@@ -64,12 +64,12 @@ echo '
deployment:
role: data_plane
role_data_plane:
- config_provider: control_plane
- control_plane:
- host:
- - https://127.0.0.1:12379
- prefix: "/apisix"
- timeout: 30
+ config_provider: etcd
+ etcd:
+ host:
+ - https://127.0.0.1:12379
+ prefix: "/apisix"
+ timeout: 30
' > conf/config.yaml
out=$(make run 2>&1 || true)
diff --git a/t/cli/test_deployment_mtls.sh b/t/cli/test_deployment_mtls.sh
deleted file mode 100755
index 5fa4c6984..000000000
--- a/t/cli/test_deployment_mtls.sh
+++ /dev/null
@@ -1,88 +0,0 @@
-#!/usr/bin/env bash
-
-#
-# Licensed to the Apache Software Foundation (ASF) under one or more
-# contributor license agreements. See the NOTICE file distributed with
-# this work for additional information regarding copyright ownership.
-# The ASF licenses this file to You under the Apache License, Version 2.0
-# (the "License"); you may not use this file except in compliance with
-# the License. You may obtain a copy of the License at
-#
-# http://www.apache.org/licenses/LICENSE-2.0
-#
-# Unless required by applicable law or agreed to in writing, software
-# distributed under the License is distributed on an "AS IS" BASIS,
-# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
-# See the License for the specific language governing permissions and
-# limitations under the License.
-#
-
-. ./t/cli/common.sh
-
-exit_if_not_customed_nginx
-
-# use mTLS
-# The 'admin.apisix.dev' is injected by ci/common.sh@set_coredns
-echo '
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- listen: admin.apisix.dev:12345
- cert: t/certs/mtls_server.crt
- cert_key: t/certs/mtls_server.key
- client_ca_cert: t/certs/mtls_ca.crt
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- certs:
- cert: t/certs/mtls_client.crt
- cert_key: t/certs/mtls_client.key
- trusted_ca_cert: t/certs/mtls_ca.crt
-' > conf/config.yaml
-
-make run
-sleep 1
-
-code=$(curl -o /dev/null -s -w %{http_code}
http://127.0.0.1:9180/apisix/admin/routes -H 'X-API-KEY:
edd1c9f034335f136f87ad84b625c8f1')
-make stop
-
-if [ ! $code -eq 200 ]; then
- echo "failed: could not work with etcd"
- exit 1
-fi
-
-echo "passed: work well with etcd in control plane"
-
-echo '
-deployment:
- role: data_plane
- role_data_plane:
- config_provider: control_plane
- control_plane:
- host:
- - "https://admin.apisix.dev:22379";
- prefix: "/apisix"
- timeout: 30
- tls:
- verify: false
- certs:
- cert: t/certs/mtls_client.crt
- cert_key: t/certs/mtls_client.key
- trusted_ca_cert: t/certs/mtls_ca.crt
-' > conf/config.yaml
-
-rm logs/error.log
-make run
-sleep 1
-
-make stop
-
-if grep '\[error\] .\+ https://admin.apisix.dev:22379' logs/error.log; then
- echo "failed: work well with control plane in data plane"
- exit 1
-fi
-
-echo "passed: work well with control plane in data plane"
diff --git a/t/cli/test_deployment_traditional.sh
b/t/cli/test_deployment_traditional.sh
index 2699c3d2a..24996eb3b 100755
--- a/t/cli/test_deployment_traditional.sh
+++ b/t/cli/test_deployment_traditional.sh
@@ -100,57 +100,6 @@ fi
echo "passed: could connect to etcd"
-echo '
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- - https://127.0.0.1:2379
-' > conf/config.yaml
-
-out=$(make init 2>&1 || true)
-if ! echo "$out" | grep 'all nodes in the etcd cluster should enable/disable
TLS together'; then
- echo "failed: should validate etcd host"
- exit 1
-fi
-
-echo "passed: validate etcd host"
-
-# The 'admin.apisix.dev' is injected by ci/common.sh@set_coredns
-
-# etcd mTLS verify
-echo '
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- host:
- - "https://admin.apisix.dev:22379";
- prefix: "/apisix"
- tls:
- cert: t/certs/mtls_client.crt
- key: t/certs/mtls_client.key
- verify: false
- ' > conf/config.yaml
-
-make run
-sleep 1
-
-code=$(curl -o /dev/null -s -w %{http_code}
http://127.0.0.1:9180/apisix/admin/routes -H 'X-API-KEY:
edd1c9f034335f136f87ad84b625c8f1')
-make stop
-
-if [ ! $code -eq 200 ]; then
- echo "failed: could not work when mTLS is enabled"
- exit 1
-fi
-
-echo "passed: etcd enables mTLS successfully"
-
echo '
deployment:
role: traditional
diff --git a/t/cli/test_etcd_mtls.sh b/t/cli/test_etcd_mtls.sh
index 5d0152ff6..a05dcdb78 100755
--- a/t/cli/test_etcd_mtls.sh
+++ b/t/cli/test_etcd_mtls.sh
@@ -168,7 +168,7 @@ make run
sleep 1
make stop
-if ! grep -E 'upstream SSL certificate does not match \"127.0.0.1\" while SSL
handshaking to upstream' logs/error.log; then
+if ! grep -F 'certificate host mismatch' logs/error.log; then
echo "failed: should got certificate host mismatch when use host in
etcd.host as sni"
exit 1
fi
diff --git a/t/core/config_etcd.t b/t/core/config_etcd.t
index 2bdddcdbd..d81cf5615 100644
--- a/t/core/config_etcd.t
+++ b/t/core/config_etcd.t
@@ -84,9 +84,9 @@ end
--- request
GET /t
--- grep_error_log chop
-peer closed connection in SSL handshake while SSL handshaking to upstream
+peer closed connection in SSL handshake
--- grep_error_log_out eval
-qr/(peer closed connection in SSL handshake while SSL handshaking to
upstream){1,}/
+qr/(peer closed connection in SSL handshake){1,}/
@@ -118,42 +118,7 @@ qr/(closed){1,}/
-=== TEST 4: originate TLS connection to etcd cluster and verify TLS
certificate (default behavior)
---- yaml_config
-apisix:
- node_listen: 1984
- ssl:
- ssl_trusted_certificate: t/servroot/conf/cert/etcd.pem
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- host:
- - "https://127.0.0.1:12379";
---- extra_init_by_lua
-local health_check = require("resty.etcd.health_check")
-health_check.get_target_status = function()
- return true
-end
---- config
- location /t {
- content_by_lua_block {
- ngx.sleep(4)
- ngx.say("ok")
- }
- }
---- timeout: 5
---- request
-GET /t
---- grep_error_log chop
-10:certificate has expired
---- grep_error_log_out eval
-qr/(10:certificate has expired){1,}/
-
-
-
-=== TEST 5: set route(id: 1) to etcd cluster with TLS
+=== TEST 4: set route(id: 1) to etcd cluster with TLS
--- yaml_config
apisix:
node_listen: 1984
@@ -197,7 +162,7 @@ passed
-=== TEST 6: get route(id: 1) from etcd cluster with TLS
+=== TEST 5: get route(id: 1) from etcd cluster with TLS
--- yaml_config
apisix:
node_listen: 1984
@@ -233,7 +198,7 @@ passed
-=== TEST 7: ensure only one auth request per subsystem for all the etcd sync
+=== TEST 6: ensure only one auth request per subsystem for all the etcd sync
--- yaml_config
apisix:
node_listen: 1984
@@ -269,7 +234,7 @@ etcd auth failed
-=== TEST 8: ensure add prefix automatically for _M.getkey
+=== TEST 7: ensure add prefix automatically for _M.getkey
--- config
location /t {
content_by_lua_block {
@@ -300,7 +265,7 @@ passed
-=== TEST 9: Test ETCD health check mode switch during APISIX startup
+=== TEST 8: Test ETCD health check mode switch during APISIX startup
--- config
location /t {
content_by_lua_block {
@@ -319,7 +284,7 @@ qr/healthy check use round robin
-=== TEST 10: last_err can be nil when the reconnection is successful
+=== TEST 9: last_err can be nil when the reconnection is successful
--- config
location /t {
content_by_lua_block {
@@ -349,7 +314,7 @@ passed
-=== TEST 11: reloaded data may be in res.body.node (special kvs structure)
+=== TEST 10: reloaded data may be in res.body.node (special kvs structure)
--- yaml_config
deployment:
role: traditional
@@ -396,7 +361,7 @@ qr/readdir key: fake res:
\{("value":"bar","key":"foo"|"key":"foo","value":"bar"
-=== TEST 12: reloaded data may be in res.body.node (admin_api_version is v2)
+=== TEST 11: reloaded data may be in res.body.node (admin_api_version is v2)
--- yaml_config
deployment:
role: traditional
@@ -446,7 +411,7 @@ qr/readdir key: fake res:
\{.*"nodes":\[\{.*"value":\["bar"\].*\}\].*\}/
-=== TEST 13: test route with special character "-"
+=== TEST 12: test route with special character "-"
--- yaml_config
deployment:
role: traditional
diff --git a/t/deployment/conf_server.t b/t/deployment/conf_server.t
deleted file mode 100644
index 2e15ed8bd..000000000
--- a/t/deployment/conf_server.t
+++ /dev/null
@@ -1,467 +0,0 @@
-#
-# Licensed to the Apache Software Foundation (ASF) under one or more
-# contributor license agreements. See the NOTICE file distributed with
-# this work for additional information regarding copyright ownership.
-# The ASF licenses this file to You under the Apache License, Version 2.0
-# (the "License"); you may not use this file except in compliance with
-# the License. You may obtain a copy of the License at
-#
-# http://www.apache.org/licenses/LICENSE-2.0
-#
-# Unless required by applicable law or agreed to in writing, software
-# distributed under the License is distributed on an "AS IS" BASIS,
-# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
-# See the License for the specific language governing permissions and
-# limitations under the License.
-#
-use t::APISIX 'no_plan';
-
-worker_connections(256);
-
-add_block_preprocessor(sub {
- my ($block) = @_;
-
- if (!$block->request) {
- $block->set_value("request", "GET /t");
- }
-
-});
-
-run_tests();
-
-__DATA__
-
-=== TEST 1: sync in https
---- config
- location /t {
- content_by_lua_block {
- local core = require("apisix.core")
- local t = require("lib.test_admin").test
-
- local consumers, _ = core.config.new("/consumers", {
- automatic = true,
- item_schema = core.schema.consumer,
- })
-
- ngx.sleep(0.6)
- local idx = consumers.prev_index
-
- local code, body = t('/apisix/admin/consumers',
- ngx.HTTP_PUT,
- [[{
- "username": "jobs",
- "plugins": {
- "basic-auth": {
- "username": "jobs",
- "password": "678901"
- }
- }
- }]])
-
- ngx.sleep(2)
- local new_idx = consumers.prev_index
- if new_idx > idx then
- ngx.say("prev_index updated")
- else
- ngx.say("prev_index not update")
- end
- }
- }
---- response_body
-prev_index updated
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- admin:
- admin_key: ~
- etcd:
- prefix: "/apisix"
- host:
- - https://127.0.0.1:12379
- tls:
- verify: false
-
-
-
-=== TEST 2: mix ip & domain
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.2:2379
- - http://localhost:2379
- - http://[::1]:2379
---- error_log
-dns resolve localhost, result:
---- response_body
-foo
-
-
-
-=== TEST 3: resolve domain, result changed
---- extra_init_by_lua
- local resolver = require("apisix.core.resolver")
- local old_f = resolver.parse_domain
- local counter = 0
- resolver.parse_domain = function (domain)
- if domain == "localhost" then
- counter = counter + 1
- if counter % 2 == 0 then
- return "127.0.0.2"
- else
- return "127.0.0.3"
- end
- else
- return old_f(domain)
- end
- end
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- # use localhost so the connection is OK in the situation that the
DNS
- # resolve is not done in APISIX
- - http://localhost:2379
---- response_body
-foo
---- error_log
-localhost is resolved to: 127.0.0.3
-localhost is resolved to: 127.0.0.2
-
-
-
-=== TEST 4: update balancer if the DNS result changed
---- extra_init_by_lua
- local etcd = require("apisix.core.etcd")
- etcd.get_etcd_syncer = function ()
- return etcd.new()
- end
-
- local resolver = require("apisix.core.resolver")
- local old_f = resolver.parse_domain
- package.loaded.counter = 0
- resolver.parse_domain = function (domain)
- if domain == "x.com" then
- local counter = package.loaded.counter
- package.loaded.counter = counter + 1
- if counter % 2 == 0 then
- return "127.0.0.2"
- else
- return "127.0.0.3"
- end
- else
- return old_f(domain)
- end
- end
-
- local picker = require("apisix.balancer.least_conn")
- package.loaded.n_picker = 0
- local old_f = picker.new
- picker.new = function (nodes, upstream)
- package.loaded.n_picker = package.loaded.n_picker + 1
- return old_f(nodes, upstream)
- end
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- local counter = package.loaded.counter
- local n_picker = package.loaded.n_picker
- if counter == n_picker then
- ngx.say("OK")
- else
- ngx.say(counter, " ", n_picker)
- end
- }
- }
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- - http://x.com:2379
---- response_body
-foo
-OK
---- error_log
-x.com is resolved to: 127.0.0.3
-x.com is resolved to: 127.0.0.2
-
-
-
-=== TEST 5: retry
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:1979
- - http://[::1]:1979
- - http://localhost:2379
---- error_log
-connect() failed
---- response_body
-foo
-
-
-
-=== TEST 6: check default SNI
---- http_config
-server {
- listen 12345 ssl;
- ssl_certificate cert/apisix.crt;
- ssl_certificate_key cert/apisix.key;
-
- ssl_certificate_by_lua_block {
- local ngx_ssl = require "ngx.ssl"
- ngx.log(ngx.WARN, "Receive SNI: ", ngx_ssl.server_name())
- }
-
- location / {
- proxy_pass http://127.0.0.1:2379;
- }
-}
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- response_body
-foo
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - https://127.0.0.1:12379
- - https://localhost:12345
- tls:
- verify: false
---- error_log
-Receive SNI: localhost
-
-
-
-=== TEST 7: check configured SNI
---- http_config
-server {
- listen 12345 ssl;
- ssl_certificate cert/apisix.crt;
- ssl_certificate_key cert/apisix.key;
-
- ssl_certificate_by_lua_block {
- local ngx_ssl = require "ngx.ssl"
- ngx.log(ngx.WARN, "Receive SNI: ", ngx_ssl.server_name())
- }
-
- location / {
- proxy_pass http://127.0.0.1:2379;
- }
-}
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- response_body
-foo
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - https://127.0.0.1:12379
- - https://127.0.0.1:12345
- tls:
- verify: false
- sni: "x.com"
---- error_log
-Receive SNI: x.com
-
-
-
-=== TEST 8: check Host header
---- http_config
-server {
- listen 12345;
- location / {
- access_by_lua_block {
- ngx.log(ngx.WARN, "Receive Host: ", ngx.var.http_host)
- }
- proxy_pass http://127.0.0.1:2379;
- }
-}
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- response_body
-foo
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:12345
- - http://localhost:12345
---- error_log
-Receive Host: localhost
-Receive Host: 127.0.0.1
-
-
-
-=== TEST 9: check Host header after retry
---- http_config
-server {
- listen 12345;
- location / {
- access_by_lua_block {
- ngx.log(ngx.WARN, "Receive Host: ", ngx.var.http_host)
- }
- proxy_pass http://127.0.0.1:2379;
- }
-}
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- response_body
-foo
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:1979
- - http://localhost:12345
---- error_log
-Receive Host: localhost
-
-
-
-=== TEST 10: default timeout
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- local etcd_cli = require("resty.etcd")
- local f = etcd_cli.new
- local timeout
- etcd_cli.new = function(conf)
- timeout = conf.timeout
- return f(conf)
- end
- etcd.new()
- ngx.say(timeout)
- }
- }
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
---- response_body
-30
-
-
-
-=== TEST 11: ipv6
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- assert(etcd.set("/apisix/test", "foo"))
- local res = assert(etcd.get("/apisix/test"))
- ngx.say(res.body.node.value)
- }
- }
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://[::1]:2379
diff --git a/t/deployment/conf_server2.t b/t/deployment/conf_server2.t
deleted file mode 100644
index 886b0cb42..000000000
--- a/t/deployment/conf_server2.t
+++ /dev/null
@@ -1,161 +0,0 @@
-#
-# Licensed to the Apache Software Foundation (ASF) under one or more
-# contributor license agreements. See the NOTICE file distributed with
-# this work for additional information regarding copyright ownership.
-# The ASF licenses this file to You under the Apache License, Version 2.0
-# (the "License"); you may not use this file except in compliance with
-# the License. You may obtain a copy of the License at
-#
-# http://www.apache.org/licenses/LICENSE-2.0
-#
-# Unless required by applicable law or agreed to in writing, software
-# distributed under the License is distributed on an "AS IS" BASIS,
-# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
-# See the License for the specific language governing permissions and
-# limitations under the License.
-#
-use t::APISIX 'no_plan';
-
-add_block_preprocessor(sub {
- my ($block) = @_;
-
- if (!$block->request) {
- $block->set_value("request", "GET /t");
- }
-
-});
-
-run_tests();
-
-__DATA__
-
-=== TEST 1: health check, ensure unhealthy endpoint is skipped
---- http_config
-server {
- listen 12345;
- location / {
- access_by_lua_block {
- if package.loaded.start_to_fail then
- ngx.exit(502)
- end
- }
- proxy_pass http://127.0.0.1:2379;
- }
-}
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- - http://localhost:12345
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- package.loaded.start_to_fail = true
- for i = 1, 7 do
- assert(etcd.set("/apisix/test", "foo"))
- end
- package.loaded.start_to_fail = nil
- ngx.say('OK')
- }
- }
---- response_body
-OK
---- error_log
-report failure, endpoint: localhost:12345
-endpoint localhost:12345 is unhealthy, skipped
-
-
-
-=== TEST 2: health check, all endpoints are unhealthy
---- http_config
-server {
- listen 12345;
- location / {
- access_by_lua_block {
- if package.loaded.start_to_fail then
- ngx.exit(502)
- end
- }
- proxy_pass http://127.0.0.1:2379;
- }
-}
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- prefix: "/apisix"
- host:
- - http://localhost:12345
- - http://127.0.0.1:12345
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- package.loaded.start_to_fail = true
- for i = 1, 6 do
- etcd.set("/apisix/test", "foo")
- end
- package.loaded.start_to_fail = nil
- local _, err = etcd.set("/apisix/test", "foo")
- ngx.say(err)
- }
- }
---- response_body
-invalid response code: 503
---- error_log
-endpoint localhost:12345 is unhealthy, skipped
-endpoint 127.0.0.1:12345 is unhealthy, skipped
-
-
-
-=== TEST 3: health check, all endpoints recover from unhealthy
---- http_config
-server {
- listen 12345;
- location / {
- access_by_lua_block {
- if package.loaded.start_to_fail then
- ngx.exit(502)
- end
- }
- proxy_pass http://127.0.0.1:2379;
- }
-}
---- yaml_config
-deployment:
- role: traditional
- role_traditional:
- config_provider: etcd
- etcd:
- health_check_timeout: 1
- prefix: "/apisix"
- host:
- - http://localhost:12345
- - http://127.0.0.1:12345
---- config
- location /t {
- content_by_lua_block {
- local etcd = require("apisix.core.etcd")
- package.loaded.start_to_fail = true
- for i = 1, 6 do
- etcd.set("/apisix/test", "foo")
- end
- package.loaded.start_to_fail = nil
- ngx.sleep(1.2)
- local res, err = etcd.set("/apisix/test", "foo")
- ngx.say(err or res.body.node.value)
- }
- }
---- response_body
-foo
---- error_log
-endpoint localhost:12345 is unhealthy, skipped
-endpoint 127.0.0.1:12345 is unhealthy, skipped
diff --git a/t/deployment/mtls.t b/t/deployment/mtls.t
deleted file mode 100644
index 2d8ecb7e6..000000000
--- a/t/deployment/mtls.t
+++ /dev/null
@@ -1,115 +0,0 @@
-#
-# Licensed to the Apache Software Foundation (ASF) under one or more
-# contributor license agreements. See the NOTICE file distributed with
-# this work for additional information regarding copyright ownership.
-# The ASF licenses this file to You under the Apache License, Version 2.0
-# (the "License"); you may not use this file except in compliance with
-# the License. You may obtain a copy of the License at
-#
-# http://www.apache.org/licenses/LICENSE-2.0
-#
-# Unless required by applicable law or agreed to in writing, software
-# distributed under the License is distributed on an "AS IS" BASIS,
-# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
-# See the License for the specific language governing permissions and
-# limitations under the License.
-#
-use t::APISIX;
-
-my $nginx_binary = $ENV{'TEST_NGINX_BINARY'} || 'nginx';
-my $version = eval { `$nginx_binary -V 2>&1` };
-
-if ($version !~ m/\/apisix-nginx-module/) {
- plan(skip_all => "apisix-nginx-module not installed");
-} else {
- plan('no_plan');
-}
-
-add_block_preprocessor(sub {
- my ($block) = @_;
-
- if (!$block->request) {
- $block->set_value("request", "GET /t");
- }
-
-});
-
-run_tests();
-
-__DATA__
-
-=== TEST 1: mTLS for control plane
---- exec
-curl --cert t/certs/mtls_client.crt --key t/certs/mtls_client.key -k
https://localhost:12345/version
---- response_body eval
-qr/"etcdserver":/
---- yaml_config
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- listen: 0.0.0.0:12345
- cert: t/certs/mtls_server.crt
- cert_key: t/certs/mtls_server.key
- client_ca_cert: t/certs/mtls_ca.crt
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- certs:
- cert: t/certs/mtls_client.crt
- cert_key: t/certs/mtls_client.key
- trusted_ca_cert: t/certs/mtls_ca.crt
-
-
-
-=== TEST 2: no client certificate
---- exec
-curl -k https://localhost:12345/version
---- response_body eval
-qr/No required SSL certificate was sent/
---- yaml_config
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- listen: 0.0.0.0:12345
- cert: t/certs/mtls_server.crt
- cert_key: t/certs/mtls_server.key
- client_ca_cert: t/certs/mtls_ca.crt
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- certs:
- cert: t/certs/mtls_client.crt
- cert_key: t/certs/mtls_client.key
- trusted_ca_cert: t/certs/mtls_ca.crt
-
-
-
-=== TEST 3: wrong client certificate
---- exec
-curl --cert t/certs/apisix.crt --key t/certs/apisix.key -k
https://localhost:12345/version
---- response_body eval
-qr/The SSL certificate error/
---- yaml_config
-deployment:
- role: control_plane
- role_control_plane:
- config_provider: etcd
- conf_server:
- listen: 0.0.0.0:12345
- cert: t/certs/mtls_server.crt
- cert_key: t/certs/mtls_server.key
- client_ca_cert: t/certs/mtls_ca.crt
- etcd:
- prefix: "/apisix"
- host:
- - http://127.0.0.1:2379
- certs:
- cert: t/certs/mtls_client.crt
- cert_key: t/certs/mtls_client.key
- trusted_ca_cert: t/certs/mtls_ca.crt
