brandonlockhart opened a new issue #18957:
URL: https://github.com/apache/superset/issues/18957
When setting the Content Security Policy HTTP header, the script-src
directive causes an error when 'unsafe-eval' is not given as a value.
#### How to reproduce the bug
1. In superset_config.py include Content-Security-Policy in
DEFAULT_HTTP_HEADERS like
``` python
DEFAULT_HTTP_HEADERS = {
"Content-Security-Policy": "default-src 'none'; script-src 'self';
style-src 'self' 'unsafe-inline'; connect-src 'self'; img-src 'self'; font-src
'self';"
}
```
2. Deploy superset
### Expected results
The Superset webpage loads correctly
### Actual results
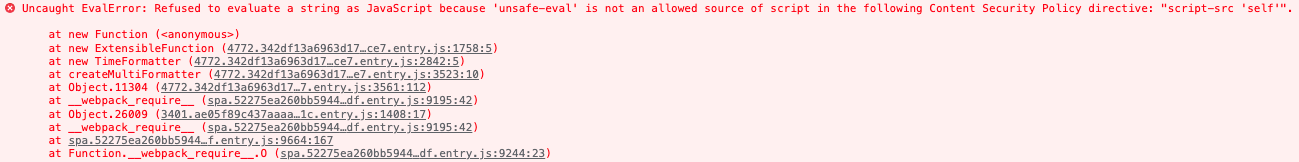
I get the error: `Uncaught EvalError: Refused to evaluate a string as
JavaScript because 'unsafe-eval' is not an allowed source of script in the
following Content Security Policy directive: "script-src 'self'".`
#### Screenshots
### Environment
(please complete the following information):
- browser type and version: Chrome, Version 98.0.4758.102
- superset version: 1.4.1
- python version: 3.8
- node.js version:
- any feature flags active: ROW_LEVEL_SECURITY, DASHBOARD_RBAC,
DASHBOARD_NATIVE_FILTERS, VERSIONED_EXPORT, ENABLE_TEMPLATE_PROCESSING
### Checklist
Make sure to follow these steps before submitting your issue - thank you!
- [x] I have checked the superset logs for python stacktraces and included
it here as text if there are any.
- [x] I have reproduced the issue with at least the latest released version
of superset.
- [x] I have checked the issue tracker for the same issue and I haven't
found one similar.
### Additional context
Add any other context about the problem here.
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: [email protected]
For queries about this service, please contact Infrastructure at:
[email protected]
---------------------------------------------------------------------
To unsubscribe, e-mail: [email protected]
For additional commands, e-mail: [email protected]
