Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Dear all,
Congratulations on the 6.2 release. You will find its arm64 port in the usual
MEGA directory. The images are built on my 6.2-{arm64,asahi,raspi} tags
(6.2/{arm64,asahi,raspi} branches). This time around the only big changes
involve the Raspberry images. Let me take a step back first, I'll come back to
RPi in a moment.
Recently, I came across this issue:
https://gitlab.tails.boum.org/tails/tails/-/issues/20347. Starting from v6.6 of
Debian's linux kernel, the kernel modules will be compressed using xz, and as a
result two build-time hooks (plus one initramfs hook) will misbehave. Now, the
failure of one of them, 80-block-network, has security implications: since
80-block-network is unable to find the network drivers' modules anymore (they
are renamed from *.ko to *.ko.xz), it fails (silently!) to populate
/etc/modprobe.d/all-net-blocklist.conf - that is, the blocklist used to disable
networking at Tails's boot. As a result, neither network blocking at boot, nor
e.g. disabling networking using the Welcome screen, work. Patching this is
quite simple, and I've already submitted a MR
(https://gitlab.tails.boum.org/tails/tails/-/merge_requests/1499). To be very
clear, x86_64 Tails uses linux 6.1, so it is not affected by this issue.
On the other hand, it so happens that the Raspberry kernel uses module
compression already in linux 6.1, which is currently in the arm64 images. Thus
the Raspi 6.1 Tails images are affected by this security issue. To fix it in
Tails/RPi 6.2, I've already merged !1499 to all my branches (together with the
uBlock patch which was the subject of previous emails), including those (arm64
and asahi) which do not use module compression (yet).
For the record, the test suite would have detected this issue easily. In fact,
it actually did: I came across it while testing (unreleased, unpublished)
Tails/Asahi builds with linux 6.6 in place of the currently installed 6.5.
However, the Raspberry images use a non-virtualizable kernel, so I can't run
the test suite on them. As I said previously, this is unfortunate since the RPi
images include a decent number of custom Raspberry packages which - as you can
see - makes testing a necessity.
Best,
NC
P.S.: I believe that an earlier version of the Asahi images was also affected
by the same issue: it used a non-Debian kernel with compressed modules which
would trigger the hooks' failure. At that time (before 6.1) I was not using the
test suite yet. Avoiding these kind of things is the main reason why I switched
to my own kernel builds, which are just the regular Debian kernel with the
Asahi patches.
___
Tails-dev mailing list
Tails-dev@boum.org
https://www.autistici.org/mailman/listinfo/tails-dev
To unsubscribe from this list, send an empty email to
tails-dev-unsubscr...@boum.org.
[Tails-dev] problem with downloading tails
Hi goats, Just a FYI that there seems to be issues flashing to the drive with BalenaEtcher from windows. I tried with about 5 different UBS - some of different sizes and make. I tried to use different USB slots. Then I tried using a different computer. Same results always. The flash fails right at the end. The USB installs Tails partially (you can't use the USB anymore) but can't run it. Cheers___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi n9iu7pk, Good to know you were able to build the images! The nvme will surely help, I/O is terrible on RPis (but then, this is expected). So first of all, no, you don't have new images to compare the shasums at the moment. I think from now on, unless there are major new features from my part which merit early sharing, I will only upload pre-built images on new Tails point releases (uploading takes quite some time and a single upload of 2x3 images takes away around half my available space). In general, only images built on tagged commits are reproducible. In case you don't know (if you do I apologize, I have little knowledge of the Tails community), when the commit is not tagged, the /etc/apt/sources.list and /etc/apt/sources.list.d/bullseye.list files contain entries like ``` deb http://time-based.snapshots.deb.tails.boum.org/debian-security/2024041403 bookworm-security main contrib non-free non-free-firmware ``` with last-snapshot timestamps which change multiple times a day (4, I believe). However, I must have been lucky enough to start a new 6.2/arm64 build while the debian-security snapshot was the same as yours so I got the same sha256sums as you! Not so lucky with asahi and raspi, which you had built earlier and I built later. Nonetheless, I compared today's contents with yesterday's and can confirm that the only difference is precisely those timestamps. "tests: on raspi image -> 206 fails, 1460 skipped, 342 passed -> reproduceable." As you can see, most of the tests are skipped: the raspi image never boots (it cannot be virtualized), so it fails early and skips the other steps. arm64 and asahi, on the other hand, should work. Thanks for the estimate. I initially thought that Tails was snapshotting the whole debian archive, but soon realized that they don't need to do so since when booted the images use the actual live debian archive instead of snapshots. Making arm64 snapshots would be far less costly than I initially thought (nonetheless, I have no plans to set up my own: the images already contain far too many binaries provided by myself!) Best, NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Because the issue already has an assignee and I didn't want to be unpolite! :-)
If groente is reading us and needs it, the patch is in attachment.
>From 8928015f4189fc2bb307343619b5d22bfaf7b28d Mon Sep 17 00:00:00 2001
From: NoisyCoil
Date: Fri, 12 Apr 2024 20:03:27 +0200
Subject: [PATCH] Refresh uBlock-disable-autoUpdate.diff
---
.../usr/share/tails/uBlock-disable-autoUpdate.diff | 2 +-
1 file changed, 1 insertion(+), 1 deletion(-)
diff --git a/config/chroot_local-includes/usr/share/tails/uBlock-disable-autoUpdate.diff b/config/chroot_local-includes/usr/share/tails/uBlock-disable-autoUpdate.diff
index 35d1da8229..be244ee7ed 100644
--- a/config/chroot_local-includes/usr/share/tails/uBlock-disable-autoUpdate.diff
+++ b/config/chroot_local-includes/usr/share/tails/uBlock-disable-autoUpdate.diff
@@ -1,6 +1,6 @@
--- /usr/share/mozilla/extensions/{ec8030f7-c20a-464f-9b0e-13a3a9e97384}/ublo...@raymondhill.net/js/background.js 2023-09-27 10:13:51.634749105 +0200
+++ /usr/share/mozilla/extensions/{ec8030f7-c20a-464f-9b0e-13a3a9e97384}/ublo...@raymondhill.net/js/background.js 2023-08-19 01:01:05.0 +0200
-@@ -100,7 +100,7 @@
+@@ -99,7 +99,7 @@
const userSettingsDefault = {
advancedUserEnabled: false,
alwaysDetachLogger: true,
--
2.39.2
___
Tails-dev mailing list
Tails-dev@boum.org
https://www.autistici.org/mailman/listinfo/tails-dev
To unsubscribe from this list, send an empty email to
tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi n9iu7pk, It looks like fixing uBlock is quite trivial, actually, so I did it myself. When an upstream patch becomes available I will revert my changes and apply that instead. The wip/* branches can now build the images. I also uploaded the 6.2/* branches. These have exactly the same content as the corresponding wip/* branches, the difference being that the arm64/asahi/raspi patches are applied directly on top of stable instead of being buried below the newer commits, so they're easily identifiable. As stable gets updated I will keep rebasing them onto it (and merging the changes to wip/*) until the 6.2 release, at which point I will freeze them. Best, NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi n9iu7pk,
I can confirm that everything's still alright with DNS redirection. I can
successfully get the build to the point where it installs the debian packages
on 6.1/raspi. The error you see is typical of when you're trying to install the
packages from the original Tails repo. Since I disabled Tail's APT key
verification, you'll only be able to install packages from the Debian archive
(or, on the 6.1/raspi branch, from Raspberry's own repo, of which I added the
key), and if you're not correctly hijacking the DNS and actually connecting to
the Tails repo the build will fail with that error, it sees the repo is signed
by Tails and rejects it. Since you said you previously built on the 6.1/raspi
branch, I assume you are now correctly redirecting
tagged.snapshots.deb.tails.boum.org as well, like I wrote before. Then I'm not
sure what your issue could be. Perhaps you could try deleting the apt cache
like you did the last time you had similar issues?
Asides from this, unfortunately the 6.1 branches will never build again due to
https://gitlab.tails.boum.org/tails/tails/-/issues/20327. Debian sid's package
webext-ublock-origin-firefox got updated to v1.57 some time after April 6th and
the 10-tbb local hook (config/chroot_local-hooks/10-tbb) does not apply one
patch cleanly anymore. As a result, the 99-zzz_check-for-dot-orig-files local
hook makes the build fail with the error
```
Checking for .orig files
E: Some patches are fuzzy and leave .orig files around:
/usr/sbin/start-stop-daemon.orig
/usr/share/mozilla/extensions/{ec8030f7-c20a-464f-9b0e-13a3a9e97384}/ublo...@raymondhill.net/js/background.js.orig
E: config/chroot_local-hooks/99-zzz_check-for-dot-orig-files failed (exit
non-zero). You should check for errors.
```
Since the arm64 builds don't use snapshots, there's no way for me to prevent
this kind of things. Unfortunately, if packages in Debian get upgraded, old
builds may well fail. Since the 6.1/* branches are essentially frozen in time,
I will not patch them. What I can and will do is keep an eye on the
aforementioned issue and update the wip/* branches so that the fix gets picked
up ASAP (I already have 6.2/* branches locally, but they will fail to build too
until the ublock thing is fixed upstream).
BTW a package upgrade, I believe, is also the reason why you didn't obtain the
same sha256sums when you built 6.1/raspi. Again due to the lack of arm64
snapshots, builds are reproducible only if packages are not subject to upgrades
between an earlier and a later build, unfortunately. I'd bet if you'd compared
your *.packages file with mine you'd have found differences.
If going ahead you have suggestions on how to improve the patchset feel free to
tell me! If you find it useful you may even send me MRs on Gitlab, otherwise
write here or send me a direct email.
En passing, do you happen to know how much space the amd64 Debian snapshots in
use by Tails take up?
Best,
NC
___
Tails-dev mailing list
Tails-dev@boum.org
https://www.autistici.org/mailman/listinfo/tails-dev
To unsubscribe from this list, send an empty email to
tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi n9iu7pk,
Thank you! Happy to hear you were able to build the other images as well.
Talking of reproducibility, I just added two fixup commits to the various
branches to make the images more reproducible (in the sense of reproducible
builds). The first one adds timestamps to the contents of /EFI/debian/efi.img
(efi.img is a FAT image that contains the grub binary and its config file;
these are responsible for UEFI boot on ISO hybrid images). The second one fixes
(or rather removes) the BCJ filter used when building the squashfs with xz
compression. It turns out that the filter which I had selected ("arm") is
specific to 32-bit arm, cannot be used for 64-bit arm64 (I had never actually
used xz compression!), and that the "arm64" BCJ filter is not available yet
neither to mksquashfs nor to the kernel decompression routines (it is in
xz-utils though, AFAICS). Fun fact: adding kernel support for the arm64 filter
seems to be part of a recent patchset whose merge is now frozen due to the
compromise of xz-utils (see https://lkml.org/lkml/2024/3/20/1010).
Thanks to the second commit one can now build tagged arm64 images using the
following nginx configuration for DNS hijacking + URL redirection:
server {
server_name time-based.snapshots.deb.tails.boum.org;
rewrite ^/(debian|debian-security)/[0-9]+(/?.*) http://deb.debian.org/$1$2;
rewrite ^/torproject/[0-9]+(/?.*)
http://deb.torproject.org/torproject.org$1;
rewrite ^/[0-9.]+(/?.*) http://deb.debian.org$1;
location ~
^/(debian|debian-security|tails|torproject)/project/trace/(debian|debian-security|tails|torproject)
{
proxy_pass http://204.13.164.63:80;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
}
location ~ ^/tails {
proxy_pass http://204.13.164.63:80;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
}
listen *:80;
}
server {
server_name tagged.snapshots.deb.tails.boum.org;
rewrite ^/[0-9a-z.-]+/(debian|debian-security)/(.*)
http://deb.debian.org/$1/$2;
rewrite ^/[0-9a-z.-]+/torproject/(.*)
http://deb.torproject.org/torproject.org/$1;
listen *:80;
}
Note the addition of tagged.snapshots.deb.tails.boum.org, which you must
redirect to your webserver too (e.g. via /etc/hosts) to be able to build tagged
images. Also, as I've already told you in a private email, I am now also
redirecting to Tor's debian repository, which does support arm64.
Non-tagged images have snapshot timestamps in their apt sources, which spoils
reproducibility (debian-security's snapshot timestamp, in particular, gets
updated every day AFAICS). Thanks also to the timestamping of efi.img's
contents, tagged arm64 images should on the other hand be reproducible during
the time frame in which the packages downloaded from the Debian archive don't
change: if you're lucky enough to build two arm64 images with the same package
versions, then those images should be identical byte-for-byte. Of course, this
is not actual reproducibility (which would need actual snapshots for the arm64
component of the Debian archive so that the images are forever reproducible),
but still, it's better than nothing.
I created three new branches, 6.1/arm64, 6.1/asahi and 6.1/raspi, which contain
the same source code as their current wip/* analogue, but with the commits
squashed and a tag (6.1-arm64, 6.1-asahi and 6.1-raspi) applied at the end of
them. I do not plan to modify the content of those branches, which you may thus
consider as arm64 6.1 "releases" of my developer preview. The binary images
built on the 6.1-* tags are in the usual MEGA folder. If you happen to build
images on those tags in the near future, and the contents of the *.packages
files are the same (which is essential to reproducibility), please let me know
if you obtain the same sha256sums!
The tagged arm64 and asahi images don't pass one more test scenario, "APT
sources are configured correctly", because of a failure in the very last step,
where it is checked that the deb.tails.boum.org distribution in its
apt.sources.d list file ("6.1", in our case) matches the build's git tag
("6.1-arm64" or "6.1-asahi" or "6.1-raspi"). In theory I could make it so that
the contents of the apt sources file match the git tag (e.g. by actually
defining a new release version), but I believe this would make things works
since deb.tails.boum.org does not provide "6.1-arm64" or "6.1-asahi" or
"6.1-raspi&
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
I forgot to say that you must also build your own Tor Browser for arm64, since the one which you'll find in the images is built by myself as well. These are the 3 Tor Browser for arm64 repos I'm aware of: - Heikki Lindholm's: https://notabug.org/holin/tor-browser-build (he's been building arm64 releases for years now) - my fork of Heikki Lindholm's repository: https://gitlab.com/NoisyCoil/tor-browser-build (very similar to the above except for minor technical differences; this is the one which I use for the 13.0.x series in the Tails images) - another one by me: https://gitlab.torproject.org/NoisyCoil/tor-browser-build (rewritten from scratch, only builds 13.5 alphas and nightlies, so this is not in use in Tails at the moment. There is an ongoing attempt to merge this upstream to provide official arm64 builds, see here: https://gitlab.torproject.org/tpo/applications/tor-browser-build/-/merge_requests/920) Best, NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi there. If I were to speak as if I didn't build the images, I would tell you that you should NOT consider the prebuilt images as secure. Those are developer previews, not (yet) reproducible, uploaded by a random person on the internet. Even if that person is me, it would make no sense to trust me. What you can do to trust the images is building them yourself from source after reviewing the latter. Building the generic arm64 and Raspberry images is fairly easy (although it will take some time and you will need to hack your own DNS resolution to redirect from the Tails debian repository to the Debian archive, in order to obtain the arm64 packages), not quite so for the asahi images, because those use custom-built kernel and mesa drivers which are not available upstream. This means you must 1. build the kernel and mesa drivers 2. create your own debian repository (the image building process uses my own debian repository), upload them there and modify the Tails source code to use your own repository (the last part being the easiest one) 3. most importantly, the toolchain (compilers and the likes) for building the kernel and mesa drivers is NOT available in the Debian archive because both the asahi kernel and mesa drivers use versions of rust and the likes which are not available for bookworm, so you must also build the toolchain first. This means building roughly half of the debian packages hosted at https://gitlab.com/debian-asahi-nc (the other half is for debian testing) and then use those to compile the kernel and mesa drivers. To be clear, the source code for building the arm64 Tails images is 100% publicly available. It is hosted at: - https://gitlab.tails.boum.org/noisycoil/tails (wip/arm64, wip/asahi and wip/raspi branches: the actual arm64 Tails source code) - https://gitlab.tails.boum.org/ <https://gitlab.tails.boum.org/noisycoil/gdm>noisycoil/gdm (a patched version of GNOME's GDM which is needed to make the automated test suite work on arm64 and is installed in all recent images) - https://deb.tails.boum.org/ (contains the debian source packages for various binary packages which have been modified for Tails itself and I rebuild verbatim for arm64. This is from Tails itself) - https://gitlab.com/debian-asahi-nc (asahi kernel, mesa drivers and toolchain to build them) But to set up the build infrastructure (DNS redirection, custom Tails packages, and Asahi packages if you need those) you'll need to work a bit. If you are interested you can write to me either here on the mailing list or in private. At some point I think I will document the build process step-by-step, which I somewhat did on the mailing list, but in a non-systematic way. Best, NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Ah, alright, I was made aware of the retagging by reading on xmpp, where it was also mentioned that there had been a last-minute commit, so I thought the two things were one-off and related. It's the first time I follow a release almost live, the next time I'll know I must wait! No problem by the way. 31 mar 2024, 13:40 da ano...@riseup.net: > On 29/03/2024 20.53, NoisyCoil via Tails-dev wrote: > >> en passing, to whoever caused the 6.1 retagging fuzz, I lost a full day >> of testing work because of that, I hate you. Kidding <3 >> > > Actually this happens every single release, where there is a ~1 hour window > where you can fetch this to-be-overwritten tag. We know this isn't ideal, and > have been lazy about fixing this for years, but I just filed an issue > describing a pretty simple fix that I think we can put in use for Tails 6.2: > https://gitlab.tails.boum.org/tails/tails/-/issues/20314 > > Sorry for the inconvenience! <3 > ___ > Tails-dev mailing list > Tails-dev@boum.org > https://www.autistici.org/mailman/listinfo/tails-dev > To unsubscribe from this list, send an empty email to > tails-dev-unsubscr...@boum.org. > ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi n9iu7pk, I had no issues rebuilding the Tails packages for arm64 from the source packages in the Tails debian repository, at least for the very few packages that are currently there. If I had modified the sources I think I would have remembered (and I would have published the modified sources), so I don't think I did. If you need help with a specific package just ask away. Yes, I don't think hosting arm64 snapshots would be much different from x86_64. Versions would already coincide, as Debian usually builds the same versions for all archs at a given time. I'm not sure I understand what you were saying about base_branch, all I did is I rebased the arm64 patchset onto the stable branch, and more specifically over the 6.1 tag (en passing, to whoever caused the 6.1 retagging fuzz, I lost a full day of testing work because of that, I hate you. Kidding <3). Those have stable as their base_branch. Previously the arm64 patches were applied to "a" devel branch (not even "the" devel branch), namely feature/bookworm, which is not there anymore having long been merged to stable. Best, NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Dear all, I rebased the arm64 patches onto v6.1, marking the first build of the Tails for arm64 developer preview that's aligned with a stable release (you can find the images in the usual MEGA shared folder). In addition to the rebase, there are a number of new additions to the patchset, the most important being that I implemented the changes needed to run the automated test suite on the arm64 proper (wip/arm64 branch) and asahi (wip/asahi branch) builds. So I'm happy to announce that the arm64 and asahi builds pass each and every single test scenario, except (of course) for those which depend on Tails infrastructure. Unfortunately, the Raspberry kernels are not virtualizable in the usual way (for starters, they lack every virtio driver), so I could not get the test suite to run on those. More details and a description of the other changes in what follows. *** Automated test suite *** In order to run the automated test suite on the arm64 images, I had to overcome quite a few obstacles. - First, I had to make the ISO images bootable via UEFI, which I hadn't done yet. For the record, I don't think ISO images are of much use in the arm64 world. - Second, it turns out that systems which boot via UEFI (like virtualized arm64 systems) do not support internal snapshots, so I had to come up with an implementation of external snapshots for the Tails test suite. External snapshots can be activated via the undocumented `--external-snapshots` option to `run_test_suite`, and they completely replace internal snapshots when activated. Be warned that new step definitions that make creative use of snapshots may well break my implementation of external snapshots, as this is only guaranteed to work with the step definitions which are currently defined. - Third, there is an annoying bug in GDM that makes arm64 VMs logout whenever `udevadm settle` or the likes is called. I had already noted this behavior in a previous email, but hadn't identified the cause yet (again, the behavior is specific to arm64 VMs only, although the bug itself exists for every arch and all hardware). Since the logouts heavily interfere with the tests' flow, I had to install a patched version of GDM in the images. The patch was fortunately already available in GDM v45, so I just had to backport it to v43. The source code for the patched GDM is at https://gitlab.tails.boum.org/noisycoil/gdm, and you can find the debian source and binary packages in the usual MEGA shared folder. - Fourth, there is another annoying bug in arm64 qemu that makes it so plymouth doesn't work on arm64 VMs. Again this conflicts with the tests' flow. Fortunately, adding a couple of kernel parameters at boot time (within the testing logic itself, i.e. along with "autotest_never_use_this_option" etc.) fixes this. - Fifth, arm64 VMs apparently cannot be booted via SATA CDROM drives, but only via SCSI CDROM drives, so on the one hand I had to define a domain for SCSI CDROM drives and use that for arm64, and on the other hand I had to include the virtio_scsi kernel module in the image's initramfs. - Sixth, a number of checks, especially those related to syslinux and to installing Tails upgrades, do not apply to arm64. I had to disable those for arm64. Also, Tails tests only use UEFI boot, never MBR. - Seventh, I found a bug and a soon-to-become bug in the test suite which directly impacted the arm64 tests (more precisely the wip/asahi tests). I have filed related bug reports and fixes have already been worked out by segfault. They will be probably released in v6.2 (one of them was already merged into stable), but in the meantime I backported them to the v6.1 arm64 build branches. These are https://gitlab.tails.boum.org/tails/tails/-/issues/20277 and the now closed https://gitlab.tails.boum.org/tails/tails/-/issues/20276. - Finally, I had to rebuild Tails' patched version of virt-viewer for arm64 and install it in my testing machines, which I did, and, again, you can find the source and binary debian packages in the usual MEGA shared folder. You will find further details and references about these issues in the commit messages themselves. The Tails arm64 tests can be run by passing the `--arm64` option to `run_test_suite`, which makes the test suite use the correct default machine (features/domains/default-arm64.xml) and CDROM domains, implicitly enables `--external-snapshots`, disables the syslinux and Tails upgrade checks, enables UEFI unconditionally, passes the correct boot parameters, etc. These are technical changes which are essential to make the test suite run in the first place. Beware that an 8GB RPi5 is already not quite powerful enough to run the tests cleanly (because of slow I/O, I would guess). The tests will indeed run (provided you set the GIC version to 2 in features/domains/default-arm64.xml) and most of them will pass, but for each run you can expect ~ 5-10% scenarios to ran
[Tails-dev] Release schedule for Tails 6.2
Hi, Anonym will be the RM for Tails 6.2 The current plan is: - Monday, April 22nd: build images, start testing - Tuesday, April 23rd: releasing @testers, please let the RM know how much time you'll have for manual QA from Monday 17:00 to Tuesday 11:00 (Europe/Berlin) Cheers, groente ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tails report for February 2024
*Tails report for February 2024* <https://tails.net/news/report_2024_02/>
Highlights
Despite the bonus day this year, February flew by pretty quickly! Here's
what we were up to:
*
We ended February more resilient and collaborative than when we
started. We have new tooling to make it easier to work on shared
documents, and use XMPP more effectively. We also worked to
strengthen our front-end services and set up the back-end
infrastructre to build redundancies into our services.
*
In 2021 and 2022, our usability tests with human rights defenders in
Mexico and Brazil
<https://tails.net/news/improving_in_latam/index.en.html> prompted
several improvements in the installation instructions for Tails.
Fixing 16 of the identified usability issues were remaining, and we
fixed them all this month. These tests, experiences, and
improvements will greatly shape our future trainings.
*
We finished updating our website for Tails 6.0. Check out the
rewritten recommendation on secure deletion
<https://tails.net/doc/encryption_and_privacy/secure_deletion/index.en.html>.
Releases
Tails 6.0 is out <https://tails.net/news/version_6.0/index.en.html>!
Tails 6.0 is the first version of Tails based on Debian 12 ("bookworm"),
and is the sexiest, slickest, and sleekest Tails yet. It brings:
*
several important security updates: more robust error detection for
the Persistent Storage, protections against malicious USB devices,
and Diceware word lists in Catalan, German, Italian, Portuguese, and
Spanish
*
some more usability features: new light modes—dark, night, and a
combination of both; easier screenshoting and screencasting; and
easier Gmail configuration in Thunderbird
*
and, updated version of most of the applications in Tails
To know more, check out the Tails 6.0 release notes
<https://tails.net/news/version_6.0/index.en.html> and the changelog
<https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog>.
Thank you to everyone who helped us out by testing the release candidate
<https://tails.net/news/test_6.0-rc1/>.
Metrics
Tails was started more than 806,714 times this month. That's a daily
average of over 27,817 boots.
_______
Tails-dev mailing list
Tails-dev@boum.org
https://www.autistici.org/mailman/listinfo/tails-dev
To unsubscribe from this list, send an empty email to
tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Release schedule for Tails 6.1
Hey, > We have no yet decided who will be the RM for Tails 6.1. That will be me! > The current plan is: > - Monday, 2024-03-25: build images, start testing > - Tuesday, 2024-03-26: releasing This is still the plan. The code freeze starts on Mon Mar 25 06:00:00 UTC 2024, and will end once the release is public. During the code freeze, please do not merge anything into the `stable` branch unless I have agreed to it! Cheers, groente ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi N9iu7pk! Good to know you managed to build the image, you're the first person to confirm it works! While I finish working on some quite exciting new features (I'm almost there but need to polish some stuff), let me give you some advice and provide some comment. - If you are running the image on a RPi5, then you could as well build it there (unless you have a good reason not to). This is what I am doing right now, as natively building Tails on a 8GB RPi5 is MUCH faster than building it on a 16-core 32-threads 64GB AMD machine. I'm talking 1.5hr tops (often less) on RPi5 vs. even 13 hrs on amd64. - What you're saying about debian-security sounds weird to me. I never had issues accessing the debian-security repo via http, neither in general nor during Tails builds. E.g. a plain `curl http://deb.debian.org:80/debian-security/dists/bookworm-security/Release <http://deb.debian.org/debian-security/dists/bookworm-security/Release>` works. - Yes, you picked the right branch. I am working on rebasing everything on stable (with new features), so a big rebase is coming soon, but the new branch names will still be wip/arm64, wip/asahi and wip/raspi. 'stable' and 'devel' are just (probably non-up-to-date versions of) Tails' regular stable and devel, with no arm64-related changes. - I never had certificate/sources issues, but I've been building on the stable branch (see above) for at least a couple of weeks now, so it may be that something broke in the meantime on the old devel-based branches. - arm64 builds are not supposed to work on x86_64 without any build options. In theory not having build options on x86_64 machines would simply build an x86_64 version of Tails. However, 1. the Asahi and RPi branches need changes that are so relevant (e.g. to the apt sources) that would require a big re-write of auto/config to maintain compatibility with x86_64 builds, and I didn't want to do those re-writes arbitrarily (i.e. without the prospect of actually merging those changes) 2. x86_64 builds on the arm64 branches could be broken in other ways, e.g. by the packages in config/chroot_local-packages, or even because I overlooked something while enabling cross-builds. Before uploading the stable-based branches I'll try and see if something needs to and can be fixed in this respect (in theory the wip/arm64 branch could build regular x86_64 images). In any case, keep in mind that the arm64 changes are nowhere near to be merged (neither from my part nor from the Tails side), so it's fine if they break x86_64 builds for now, so long as they don't do so intentionally, and if the breakage is fixed when possible - systemd-sysctl.service failing: this is a known (by me) issue. It is due to the "CONFIG_ARCH_MMAP_RND_BITS_MAX" kernel configuration variable. For Debian's standard arm64 (and amd64) kernel it equals 32, for Asahi 16k pages kernels it's 31, it's 30 for the 4k pages 64-bit RPi kernel, and it's 24 for the RPi5 16k pages kernel. systemd-sysctl.service tries to set `mmap_rnd_bits` to 32 as specified in /etc/sysctl.d/mmap_aslr.conf, so it fails on every kernel except for vanilla Debian's standard arm64 kernel (i.e. on the wip/arm64 branch). I've already fixed this in the Asahi images (not pushed yet) but not in the RPi ones. Thanks for letting me know so I could look into it! A fix will be coming soon. - I noticed the freezing issue too. It only happens on RPi, never saw that on Apple Silicon nor on arm64 VMs (wip/arm64 branch). Also, it doesn't happen always. This makes me think the freeze may be due to some sort of race condition triggered e.g. by RPi being overload at boot time. Also it looks like this: https://gitlab.tails.boum.org/tails/tails/-/issues/20227. If it was already fixed in mainline Tails, then the fix is probably not merged to my public branches yet (but will soon be). I agree that a double image (two squashfs) is very appealing, but making it would require a full re-write of the image-building process, so I'm not sure I'm willing to waste time on that at this time. I explicitly talk about waste not because it is useless in principle (it is not, of course), but because the changes would be so radical that making them arbitrarily, without the involvement of Tails maintainers and/or without actual plans for merging them, would essentially amount to a waste. Instead, for the time being, I'd like to make sure that everything works properly and that whatever needs to be upstreamed is upstreamed. Do I hear official support for the Tor Browser on arm64 (https://gitlab.torproject.org/tpo/applications/tor-browser-build/-/merge_requests/920)? Do I hear Tails automatic test suite? More to come soon. NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] E-mails from our GitLab are not being delivered correctly
Hello, dear contributors! You may all be affected by this and may not be notified in other ways, so I decided to post here: E-mails from our GitLab are not being delivered correctly https://gitlab.tails.boum.org/tails/sysadmin/-/issues/18071 Big thanks for your time, efforts and patience! <3 -- signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails-dev Digest, Vol 165, Issue 13
Hi Ben, I thought it was understood we're talking about two separate squashfs filesystems - one for each architecture -, hence double the size. I don't see how the binaries for two different architectures could coexist on the same root. Perhaps you could heavily tweak live-boot (again, I think this is the right component but I'm not sure) so as to overlay the content of different squashfs's over the same root? Of course, you should also heavily tweak live-build to build such an image. For the record, I like the idea too, I think it's cool. But perhaps we should first focus on if and how to bring Tails on arm64 :-) NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails-dev Digest, Vol 165, Issue 13
> - It would double the size of the image, uselessly or almost so for most users This is unlikely. The uncompressed `/usr/share` folder in Tails is 1.2 GB this is architecture independent data. https://refspecs.linuxfoundation.org/FHS_3.0/fhs/ch04s11.html The total unsquashed size is 4.1 GB, so possible image size increases 70%, but likely arch-dependent software compresses well with its other arch pair. > Create a lot of issues as soon as, e.g., the system starts to store > arch-dependent files as dotfiles (think of caches or binary config files!), > and good luck to who has to deal with that. Arch-dependent application files and dotfiles could be written to the Persistent Storage with permissions so only the current arch can read them. Applications complying with XDG Base Directory Specification or FHS 3.0 will require no intervention, besides needing to install the software for both arches during separate sessions, although installing both (if both exist) could be automated. https://specifications.freedesktop.org/basedir-spec/basedir-spec-latest.html I quite like the cross-arch medium, it's ambitious but very useful. Sent with Proton Mail secure email. On Tuesday, February 20th, 2024 at 1:10 PM, tails-dev-requ...@boum.org wrote: > Send Tails-dev mailing list submissions to > tails-dev@boum.org > > To subscribe or unsubscribe via the World Wide Web, visit > https://www.autistici.org/mailman/listinfo/tails-dev > or, via email, send a message with subject or body 'help' to > tails-dev-requ...@boum.org > > You can reach the person managing the list at > tails-dev-ow...@boum.org > > When replying, please edit your Subject line so it is more specific > than "Re: Contents of Tails-dev digest..." > > > Today's Topics: > > 1. Re: Tails for arm64 (with support for Apple Silicon) > (noisyc...@tutanota.com) > 2. Tor Browser 13.0.10 (Android, Windows, macOS, Linux) > (Richard Pospesel) > 3. Re: Release schedule for Tails 6.0 (anonym) > > > -- > > Message: 1 > Date: Mon, 19 Feb 2024 20:21:48 +0100 (CET) > From: noisyc...@tutanota.com > To: "David A. Wheeler via Tails-dev" tails-dev@boum.org > > Cc: The Tails public development discussion list tails-dev@boum.org, > > "David A. Wheeler" dwhee...@dwheeler.com > > Subject: Re: [Tails-dev] Tails for arm64 (with support for Apple > Silicon) > Message-ID: nr1oieq--...@tutanota.com > > Content-Type: text/plain; charset=UTF-8 > > Hi David, > > Yes, I thought you'd already mentioned that. The quite long email I sent last > week detailing some of the differences between the Apple Silicon and > Raspberry Pi builds was also in response to you. > > Something which I didn't address there is the possibility of cross-arch (!) > images. Although I believe literally no distribution in human history has > attempted something like this, I think that, paradoxically, building an > arm64+x86_64 live image of Tails might be easier than building an image that > works properly on two arm64 platforms with conflicting software requirements. > If two platforms, one x86_64 and one arm64, boot via grub-efi at?UEFI's > removable path, then the latter is different for the two architectures > (EFI/BOOT/BOOTAA64.EFI for arm64 and EFI/BOOT/BOOTX64.EFI for x86_64), so the > two boot paths wouldn't conflict with each other and could coexist on the > same medium. Each version of grub could then be configured to load the kernel > and initramfs for its architecture, and live-boot (I think this is the right > component) could be configured (or tweaked) to load the squashfs filesystem > from an arch-specific path. > > As for persistence, one could keep the behavior of arch-dependent and > arch-independent files separate. For instance, one could share dotfiles, > network configurations, greeter settings, etc. between architectures and > create two separate "additional software" repositories on persistence > storage, one for each arch. > > > A few downsides to this approach: > > - It would double the size of the image, uselessly or almost so for most users > - It would require an almost-complete rewrite of the image-building process > (live-build is unable to build this kind of arch-hybrid image) > - It still doesn't solve the issue of software incompatibilities between > different arm64 hardware (see one of my previous emails for details on this), > which of course has a higher priority and may not have a solution at all > - Sure as hell it would create a lot of issues as soon as, e.g., the system > starts to store arch-dependent files as dotfiles (think of caches or binary > con
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hi David, Yes, I thought you'd already mentioned that. The quite long email I sent last week detailing some of the differences between the Apple Silicon and Raspberry Pi builds was also in response to you. Something which I didn't address there is the possibility of cross-arch (!) images. Although I believe literally no distribution in human history has attempted something like this, I think that, paradoxically, building an arm64+x86_64 live image of Tails might be easier than building an image that works properly on two arm64 platforms with conflicting software requirements. If two platforms, one x86_64 and one arm64, boot via grub-efi at UEFI's removable path, then the latter is different for the two architectures (EFI/BOOT/BOOTAA64.EFI for arm64 and EFI/BOOT/BOOTX64.EFI for x86_64), so the two boot paths wouldn't conflict with each other and could coexist on the same medium. Each version of grub could then be configured to load the kernel and initramfs for its architecture, and live-boot (I think this is the right component) could be configured (or tweaked) to load the squashfs filesystem from an arch-specific path. As for persistence, one could keep the behavior of arch-dependent and arch-independent files separate. For instance, one could share dotfiles, network configurations, greeter settings, etc. between architectures and create two separate "additional software" repositories on persistence storage, one for each arch. A few downsides to this approach: - It would double the size of the image, uselessly or almost so for most users - It would require an almost-complete rewrite of the image-building process (live-build is unable to build this kind of arch-hybrid image) - It still doesn't solve the issue of software incompatibilities between different arm64 hardware (see one of my previous emails for details on this), which of course has a higher priority and may not have a solution at all - Sure as hell it would create a lot of issues as soon as, e.g., the system starts to store arch-dependent files as dotfiles (think of caches or binary config files!), and good luck to who has to deal with that In the end it would probably be easier to make "Backup Persistent Storage" selective and allow the user to backup arch-independent files to a USB drive hosting a version of Tails for a different arch. Best, NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
> On Feb 18, 2024, at 9:03 AM, NoisyCoil via Tails-dev > wrote: > TLDR; All Tails-specific apps now work on arm64 (with two minor "not-my-bug" > caveats). You can now cross-build Tails for arm64 on an x86_64 machine. I think it'd be nice to have an ARM version of Tails, at least one that ran on Raspberry Pis & ARM Macs. Bonus points if the same image could run on that *or* x86, as then people would be able to use "the machine available to them". Then users could use a wide variety of machines. (You might have to re-download any specialized apps installed on the Persistent Storage for the "not currently loaded architecture.) Whether or not doing that is *worth* the effort is obviously debatable, but I thought I'd raise it. --- David A. Wheeler _______ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Dear all, I have some exciting news. TLDR; All Tails-specific apps now work on arm64 (with two minor "not-my-bug" caveats). You can now cross-build Tails for arm64 on an x86_64 machine. First, as of my last commits, Tails Cloner now works on all my arm64 branches. This means that, with two exceptions (see ahead), all user-facing Tails-specific applications - namely Tails Cloner, Persistent Storage, Back Up Persistent Storage, Tails Documentation, WhisperBack -, plus the Tor Browser (the unofficial build) and OnionShare (factoring out the known bugs) now work on arm64. As for the other applications, I have not spent much time checking them one-by-one yet, so I can't promise anything, but in general they seem in good state. The two exceptions to the above could be classified as "not my bug": 1. WhisperBack crashes at startup on Apple Silicon only. I believe this should be fixed upstream (I mean in the main Tails repos) so I've filed a bug (https://gitlab.tails.boum.org/tails/tails/-/issues/20200) and drafted a quick fix (https://gitlab.tails.boum.org/tails/tails/-/merge_requests/1410). 2. Creation of persistent storage misbehaves when running Tails in an arm64 VM. Hardware platforms (i.e. Apple Silicon and RPi) are not affected by this issue, nor are x86_64 VMs (I tested your Tails 6.0-rc1 build). More precisely, when running in a VM, GDM restarts while creating persistent storage. The Tails greeter thus re-appears, and if you try to get past that the GNOME session doesn't go back to where it was. Persistent storage is still created correctly (the application runs to completion in the background!), but at that point there's not much you can do other than restart the VM. After restarting, everything works fine (including persistence). I have determined that this is due to the "udevadm trigger" command internally run by tails-persistent-storage, and that this is not Tails specific: even on a vanilla Debian Bookworm arm64 installation, a VM will log out of the user session when "udevadm trigger" is called (but there's no Tails greeter workflow in vanilla Debian, so there you can just re-login). Since you already have https://gitlab.tails.boum.org/tails/tails/-/issues/20020, I will not address this issue at this moment. The second and most exciting news is you can now cross-build Tails for arm64 on an x86_64 machine! Keeping in mind that you still need to hijack your DNS to download the arm64 packages, to build an arm64 version of Tails on x86_64: - install the "binfmt-support", "qemu-user-static", "qemu-system-arm" and "qemu-efi-aarch64" Debian packages: sudo apt-get install -y binfmt-support qemu-user-static qemu-system-arm qemu-efi-aarch64 - include "crossarm64" in TAILS_BUILD_OPTIONS Internally, cross-building works as follows. First binfmt-support and qemu-user-static automagically turn vmdb2 into a cross-arm64 image builder, so that an arm64 Vagrant box is built in place of an am64 one. Then the Vagrant box is run in emulation (via qemu proper instead of kvm) and does exactly the same job it would during a native build, only MUCH slower. And when I say "much slower" I mean it: on a last-generation 32-cores, 64GB x86_64 machine, my first build took 13 hours, the second one 6 hours, the third one 3-4 hours (depending on pre-existing caches), vs ~ 15 minutes for a native x86_64 build and ~ 1 hour on a 4-core 8GB Raspberry Pi 5 for a native arm64 build. So cross-builds should only be done when necessary (e.g. in production? ;-) ). Note that I only attempted to cross-build on a single Ubuntu 23.10 machine, so the qemu configuration that's used for emulation may need some tweaks. For example, I'm not sure whether the "gic version='3'" feature, which is needed to emulate more than 8 cores (and up to 512, see https://www.qemu.org/docs/master/system/arm/virt.html) is supported on all x86_64 machines. If anybody attempts the cross build and it doesn't work, please write to me so we can get it fixed. Best, NC _______ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] FWD: Re: Tails for arm64 (with support for Apple Silicon)
I've already rebuilt them all for arm64! They are inside config/chroot_local-packages so they will get installed automatically in the image. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] FWD: Re: Tails for arm64 (with support for Apple Silicon)
Hi there,
I went for a DNS hack precisely so I could keep the patches to a minimum. All
the relevant downloads are done via plain HTTP+signature verification, so in
the end it was enough to disable a couple of points in the code where the
signatures are actually checked.
Note that simply pointing your DNS resolver to Debian's servers is not enough.
Tails's repository (at least for branches based on devel) is also queried to
fetch the timestamp of the most recent snapshot to be used, so you must
redirect both to Debian AND to Tails depending on the URL. To do so, you must:
1. configure your DNS resolver so that the Tails domain resolves to a webserver
you control
2. use that webserver to redirect some URLs to Debian, and some others to Tails
*** DNS hijacking ***
There are many ways to hijack your DNS resolution. The simplest to set up
probably (and the one I'm using) is to use systemd-resolved with the stub
resolver turned on, adding the following line to /etc/hosts in your build
machine:
x.x.x.x time-based.snapshots.deb.tails.boum.org
where x.x.x.x is the IP address of the webserver you control. This can be
running on the build machine itself, but if you decide to go this way make sure
that x.x.x.x is not in 127.0.0.0/8, otherwise the VM that builds the image will
be redirected to its own localhost!
Some of the options you have here are: using an address (not in 127.0.0.0/8)
bound to one of your network interfaces, creating a dummy network interface and
assigning it a new address, or using the address of a remote host you control.
One special case of the first option is using the address of the gateway for
the local network that Vagrant will create for the VM (if you know that in
advance). Personally, I'm using a remote host, because it was simpler to set up
for me. In any case, make sure that the VM is able to connect to that IP
address (and that the webserver is listening on port 80 of that address, of
course).
*** Webserver configuration ***
I'm using an nginx webserver with the following configuration:
server {
server_name time-based.snapshots.deb.tails.boum.org;
listen *:80;
rewrite ^/(debian|debian-security)/[0-9]+(/?.*) http://deb.debian.org/$1$2;
rewrite ^/[0-9.]+(/?.*) http://deb.debian.org$1;
location ~
^/(debian|debian-security|tails)/project/trace/(debian|debian-security|tails) {
proxy_pass http://204.13.164.63:80;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
}
location ~ ^/(tails|torproject) {
proxy_pass http://204.13.164.63:80;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-Protocol $scheme;
proxy_set_header X-Forwarded-Host $http_host;
}
}
204.13.164.63 <http://204.13.164.63:80> is the real IP address of
time-based.snapshots.deb.tails.boum.org. URLs that match the regex
^/(debian|debian-security|tails)/project/trace/(debian|debian-security|tails)
must be redirected back to Tails to get the timestamp of the most recent
snapshot. This timestamp however is never actually used: the redirections
http://time-based.snapshots.deb.tails.boum.org/(debian|debian-security)/[0-9]+(/?.*)
> http://deb.debian.org/$1$2 <http://deb.debian.org/$1$2>
http://time-based.snapshots.deb.tails.boum.org/[0-9.]+(/?.*) >
http://deb.debian.org$1 <http://deb.debian.org$1>
will point the VM to the live Debian archive rather than to a Tails snapshot
(in practice they will remove the timestamp from the URL and replace the Tails
domain with the Debian domain). As for ^/(tails|torproject), I'm not sure these
need to be redirected too, but hey, this way it works so let's keep them. Also,
it's unlikely that anything is reading the X-Headers, but let's keep those
configs too.
A corresponding configuration could be written for Apache, but I don't know how
to do that.
Keep in mind that if you hijack your DNS like above you won't be able to build
Tails on branches other than my own: the hijacked packages are signed with
Debian's keys, but the regular branches expect Tails's! So after you are
finished delete the entry from /etc/hosts and restart systemd-resolved.
If you need more help feel free to write me!
NC
___
Tails-dev mailing list
Tails-dev@boum.org
https://www.autistici.org/mailman/listinfo/tails-dev
To unsubscribe from this list, send an empty email to
tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] FWD: Re: Tails for arm64 (with support for Apple Silicon)
A couple updates on my last email. I figured out that the issue with OnionShare on RPi was due to AppArmor not being enabled by default (it needs an extra kernel command line option). I uploaded a new image with the fix and pushed the changes to Gitlab. In the meantime, I modified the repartitioning script so that it updates the main partition's UUID in the kernel command line at each boot. This way you no longer need manual fixes to boot the RPi image after the first boot. Also, I can confirm that the RPi image boots from SD cards after removing "live-media=removable" from the kernel command line (located at /cmdline.txt). It makes sense for the RPi to interpret SD cards as non-removable media. Best. P.S.: To Adam Burns, who reached out to me in private: I'm getting Undelivered Mail Returned to Sender messages from your mail provider (which is apparently blocking Tutamail). So, if you want an answer, write from a different email please :-) ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] FWD: Re: Tails for arm64 (with support for Apple Silicon)
Hi there!
TLDR; Not much has changed in the last 7 years probably. I think that thanks to
the Asahi project Tails will be able to run on Apple Silicon on stock Debian
packages in the foreseeable future (and with far better support than x86_64
Apple has received until now). Maintaining a unified arm64 image might be more
of a burden than maintaining separate arm64 images, if at all possible. I
merged the 6.0~rc1 changes into my branches and rebuilt and uploaded the
generic arm64, Apple Silicon and Raspberry Pi Tails images.
Let me start by saying that my experience with arm hardware is limited to Apple
Silicon and Raspberry Pis, so I don't really have an overall picture of how
things are done in the arm world. Nonetheless, my impression (and the general
consensus among those who actually develop for arm, AFAIK) is that every vendor
still does their own thing and usually doesn't take the time to build common
standards for interoperability. For sure this is the situation I found when
building those images. Let me give you some examples by going into some
technical detail.
*** Booting + firmware ***
The plain "wip/arm64" image in the folder I shared is a straightforward
translation of Tails from x86_64 to arm64 except for some quirks, e.g. the
directory layout of the initramfs (which is different on arm64 Debian) or the
absence of unneeded software such as syslinux. This image boots with UEFI and
runs on standard Debian packages (except for those which I rebuilt from the
Tails repository). In particular, it can be run as a VM e.g. using native KVM,
and probably by emulating an arm64 VM on x86_64 too. It won't USB-boot on
neither RPi nor Apple Silicon though, first and foremost because those do not
support UEFI out of the box (this is not the only reason, though, more on this
later).
How do the RPis and arm64 Macs boot? The former actually use different
mechanisms for different models (just to keep things simple, you know), see
e.g.
https://www.raspberrypi.com/documentation/computers/raspberry-pi.html#raspberry-pi-boot-modes
and the following sections, but also
https://www.raspberrypi.com/documentation/computers/configuration.html#the-boot-folder
for details on the firmware files. The bottom line is, if not configured
otherwise, each model does its thing and ultimately loads a kernel with a
specific file name from the boot partition (some models load the same kernel,
others don't), together with a similarly-named initramfs. In that partition you
thus need to include some /{kernel*,initrd*} files, plus firmware files. Also,
not all arm64 models can boot from USB (RPi4 and 5 can, I can't remember which
others can or cannot), and I have not attempted booting Tails from an SD card.
As for the arm64 Macs, as I wrote in my first email, they don't support booting
from external media. However, the (internal) bootloader used by Asahi Linux -
which actually is a chain of bootloaders, see e.g.
https://github.com/AsahiLinux/docs/wiki/Distro:Boot-process-guide - is actually
able to boot from USB with UEFI, and can be installed stand-alone. So if your
user is willing to waste ~ 3GB of disk space on a separate partition just to be
able to boot Tails, they are good to go. And if they already have an Asahi
Linux distro installed, they actually already have the bootloader/chain
installed.
Interestingly, the on-disk files (the kernel, initramfs and firmware) needed to
boot a live OS on RPi and Apple Silicon do not conflict with each other: they
can be included side by side. For the record, while you do need to include the
RPi firmware in the image, on Apple Silicon that comes preloaded by the Asahi
bootchain. No proprietary Apple firmware needs to be included in the image.
I will mention here that there's a chance that the RPis <= 4 could also be
booted via GRUB/UEFI, either by first loading U-Boot and then grub (U-Boot
seems to support RPis <= 4, see e.g.
https://hechao.li/2021/12/20/Boot-Raspberry-Pi-4-Using-uboot-and-Initramfs/,
and U-Boot is able to load grub-efi), or by using stuff like that in
https://github.com/pftf. I didn't try any of those mainly because I own a
Raspberry 5, which is not supported (yet?) by those projects.
*** The kernel and initramfs ***
It is likely that most bare-metal arm64 platforms Tails wants to support will
need a dedicated kernel in order for them to work properly (or at all), at
least in the near future. This is certainly true at this very moment in time
for Apple Silicon: these machines will not work with the current stock Debian
kernel, and Linux's support for Apple Silicon - though quite mature at this
stage - hasn't been fully upstreamed yet (the main repo lives at
https://github.com/AsahiLinux/linux), even if this is the ultimate goal of the
Asahi project. I was recently told by the Debian Bananas team that official
support for Apple Silicon will likely only come from Debian after the Asahi
patches
[Tails-dev] [Tails News] Test Tails 6.0~rc1
# [Test Tails 6.0~rc1](https://tails.net/news/test_6.0-rc1/) We are very excited to present you a release candidate of the upcoming Tails 6.0. We plan to release Tails 6.0 officially on February 27. You can help us by testing already a release candidate of Tails 6.0 before February 18. Tails 6.0 will be the first version of Tails based on Debian 12 (Bookworm) and GNOME 43. It will bring new versions of most of the software included in Tails as well as several important security and usability improvements. We will provide security upgrades for Tails 6.0~rc1 like we do for regular versions of Tails. # New features ## Mount external devices automatically When you plug in an external storage device, a USB stick or an external hard disk, Tails 6.0~rc1 mounts it automatically. If the storage device contains an encrypted partition, Tails 6.0~rc1 offers you to unlock the encryption automatically.  ## Protection against malicious USB devices If an attacker manages to plug a [malicious USB device](https://en.wikipedia.org/wiki/BadUSB) in your computer, they could run software that breaks the security built in Tails without your knowledge. To protect from such attacks while you are away from your computer, Tails 6.0~rc1 ignores any USB device that is plugged in while your screen is locked. You can only use new USB devices if they are plugged in while the screen is unlocked.  ## Dark Mode and Night Light >From the system menu of Tails 6.0~rc1, you can now switch between: * The default _light_ mode with colder colors and more brightness  * A _dark_ mode  * A _night light_ mode with warmer colors and less brightness  * A combination of both the _dark_ mode and _night light_ mode  ## Easier screenshots and screencasts GNOME 43 introduces a new  shortcut in the system menu that makes it easier to take a screenshot or record a screencast.  ## Easier Gmail in Thunderbird Thanks to changes in both Thunderbird and Gmail, it's much easier to configure a Gmail account in Thunderbird in Tails 6.0~rc1. * You don't have to configure anything special in your Gmail account, other than the usual 2-Step Verification. * You can sign in to your Gmail account directly when configuring it in _Thunderbird_.  ## Diceware passphrases in 5 more languages When creating a Persistent Storage, suggested passphrases are now also generated in Catalan, German, Italian, Portuguese, and Spanish. Thanks to [jawlensky](https://gitlab.tails.boum.org/jawlensky) who created the word lists for Catalan, Italian, and Spanish for Tails, but also made them available to all users of `diceware`.  # Changes and updates ## Included software Tails 6.0~rc1 updates many of the applications included in Tails, among others: * _Electrum_ from 4.0.9 to 4.3.4 * Improve support for the Lightning protocol and hardware wallets. * _KeePassXC_ from 2.6.2 to 2.7.4 * Add entry tags. * Support dark mode. * Redesign history view. * _Metadata Cleaner_ from 1.0.2 to 2.4.0 * Redesign the whole user interface. * Support dark mode. * Add support for AIFF and HEIC files. * _OnionShare_ from 2.2-3 to 2.6-5 * Redesign the whole user interface. * Allow creating chat rooms. * Allow hosting static websites. * _Text Editor_ from `gedit` to `gnome-text-editor` * Support dark mode. * _Inkscape_ from 1.0.2 to 1.2.2 * _Audacity_ from 2.4.2 to 3.2.4 * _Gimp_ from 2.10.22 to 2.10.34 * _Kleopatra_ from 4:20.08 to 4:22.12 ## Removed features * Remove the item **Remove metadata** from the shortcut menu of the _Files_ browser. The developers of MAT2, the metadata removal library used by _Metadata Cleaner_ are not providing this option anymore. * Remove the item **Wipe** and **Wipe available disk space** from the shortcut menu of the _Files_ browser. Secure deletion is not reliable enough on USB sticks and SSDs for us to keep advertising this feature. We are still discussing which alternatives to explain in our documentation on [secure deletion](https://tails.net/doc/encryption_and_privacy/secure_deletion/index.en.html). ([#19121](ht
[Tails-dev] [Tails News] Tails 5.22
# [Tails 5.22](https://tails.net/news/version_5.22/index.en.html) # New features * In _Tor Browser_ , you can now save files to more folders: Documents, Downloads, Music, Pictures, and Videos. You can also upload files from these folders. * When your Persistent Storage is broken, Tails now tries to repair its file system when you unlock it in the Welcome Screen. # Changes and updates * Report the write speed after cloning a Persistent Storage from _Tails Cloner_. * Do not try to unlock or delete a Persistent Storage on a read-only USB stick. * Update _Tor Browser_ to [13.0.9](https://blog.torproject.org/new-release-tor-browser-1309/). * Update _Thunderbird_ to [115.7](https://www.thunderbird.net/en-US/thunderbird/115.7.0/releasenotes/). # Fixed problems * Stop leaking the first-level domain of visited websites in _WhisperBack_ reports. The problem was first introduced in Tails 5.15.1 (July 2023). ([!1344](https://gitlab.tails.boum.org/tails/tails/-/merge_requests/1344)) * Make installing Tails with _Tails Cloner_ more robust by fixing occasional errors `AttributeError: 'NoneType' object has no attribute 'props'`. Thanks to Ben Westgate! ([!1312](https://gitlab.tails.boum.org/tails/tails/-/merge_requests/1312)) * Fix saving the Additional Software configuration when creating a Persistent Storage. ([!1350](https://gitlab.tails.boum.org/tails/tails/-/merge_requests/1350)) * Fix help link when resizing the system partition fails the first time Tails is started. ([!1341](https://gitlab.tails.boum.org/tails/tails/-/merge_requests/1341)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Get Tails 5.22 ## To upgrade your Tails USB stick and keep your Persistent Storage * Automatic upgrades are available from Tails 5.0 or later to 5.22. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.net/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.net/install/windows/index.en.html) * [Install from macOS](https://tails.net/install/mac/index.en.html) * [Install from Linux](https://tails.net/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.net/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.22 directly: * [For USB sticks (USB image)](https://tails.net/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.net/install/download-iso/index.en.html) URL: <https://tails.net/news/version_5.22/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Tails for arm64 (with support for Apple Silicon)
Hey there, Thank you! I actually maintain my own private fork of Heikki Lindholm's arm64 Tor Browser, but in the arm64 port of Tails I included Lindholm's own builds because those have been around for years now and are definitely more trusted than mine. They work perfectly, are well maintained and are as close as can be to the official x86_64 builds. As for armhf, I'm not going to attempt building neither the Tor Browser nor Tails for that platform for a number of reasons, the first of which being I just don't own the required hardware. However, I'd expect that somebody else could take on if they are interested, as much of the work that goes into porting to arm64 could probably be translated to armhf (not all of it though!). Also, thanks for the support! In the near future, when I find the time, I'm going to answer the other devs with some notes on how I made Tails boot on Apple Silicon and on the Raspberry 5. It was not rocket science, to be fair, but still worth documenting. I expect that - together with platform-specific quirks - to give the devs the bigger headaches if Tails will ever support arm64. Best, NC Jan 28, 2024, 13:18 by n9iu...@posteo.net: > Hi NoisyCoil, > >> ... This makes the Tor Browser >> the single blocker for Tails on arm64 AFAICS (more on this later). >> > that helped me years ago to get Tor Browser running on a rpi -> > https://gitlab.torproject.org/legacy/trac/-/issues/12631 > > Best Regards > n9iu7pk > > Am 20.01.2024 16:43 schrieb NoisyCoil via Tails-dev: > >> *** For the casual reader: please do not use this version of Tails. >> This is just a developer preview, it won't protect you like official >> releases do *** >> >> Hey there, >> >> During the last few weeks I've been working on porting Tails to the >> arm64 architecture, with the aim to ultimately being able to run Tails >> on Apple hardware again. If anyone is interested in a developer >> preview, you will find two USB images at >> https://mega.nz/folder/BrJFGQyR#8rsN06I_pC_YV6spqATeBA. The code is >> hosted at https://gitlab.tails.boum.org/noisycoil/tails in the >> "wip/arm64" and "wip/asahi" branches. The former enables general arm64 >> support, while the latter contains additional, currently >> non-upstreamable patches that make Tails run on Apple Silicon with >> M1/M2 processors (no M3 support yet). In both cases, the builds are >> native (you must build the arm64 version of Tails on arm64 hardware; >> I've been building it on Apple Silicon (Asahi Debian) and on a >> Raspberry Pi (Raspberry Pi OS) interchangeably). >> The wip/asahi patches currently break amd64 builds due to a new entry >> in the APT preferences file, but this can be fixed (I didn't do so >> yet because, as I said, the Asahi patches cannot be upstreamed anyway, >> more on this later). >> >> Both the wip/arm64 and the wip/asahi images use GRUB for arm64 as a >> boot loader. For the former, this is all there is at the moment, >> meaning that the image can run in a VM, but may not run on hardware >> that needs special firmware or arrangements to make it boot. As for >> the latter, GRUB is all that's needed to boot on bare metal Apple >> Silicon (from the Tails side, that is). >> For those unfamiliar with the boot process on arm64 Apple hardware, >> here's a quick recap. Out of the box, Apple Silicon does not support >> booting from external media, nor of course booting Linux. It does, >> however, support booting multiple macOSes from internal storage. The >> smart folks at Asahi Linux (https://asahilinux.org/) came up with a >> process to boot Linux both from internal and external storage (there >> may be issues with booting from large external hard drives, but this >> is not relevant to Tails). What they do is they install a fake macOS >> on the hard drive, which after a couple of intermediate steps runs the >> U-Boot boot loader (https://docs.u-boot.org/en/latest/), which is then >> able to run GRUB both from internal and from external storage. This >> mechanism is currently in use to run, among others, the official remix >> of Fedora for Apple Silicon (https://asahilinux.org/fedora/), and - >> except for the part where you actually have to install the boot loader >> and for a second small exception, see below - is 100% transparent to >> the user. >> >> >> So how do you boot Tails on Apple Silicon? >> >> 1) Install U-Boot on your Apple Silicon Mac. This can be done using >> the official Asahi installer (see https://asahilinux.org/): >> >> curl https://alx.sh | sh >> >> The correct option, which should only require around 3GB of
[Tails-dev] Tails for arm64 (with support for Apple Silicon)
*** For the casual reader: please do not use this version of Tails. This is just a developer preview, it won't protect you like official releases do *** Hey there, During the last few weeks I've been working on porting Tails to the arm64 architecture, with the aim to ultimately being able to run Tails on Apple hardware again. If anyone is interested in a developer preview, you will find two USB images at https://mega.nz/folder/BrJFGQyR#8rsN06I_pC_YV6spqATeBA. The code is hosted at https://gitlab.tails.boum.org/noisycoil/tails in the "wip/arm64" and "wip/asahi" branches. The former enables general arm64 support, while the latter contains additional, currently non-upstreamable patches that make Tails run on Apple Silicon with M1/M2 processors (no M3 support yet). In both cases, the builds are native (you must build the arm64 version of Tails on arm64 hardware; I've been building it on Apple Silicon (Asahi Debian) and on a Raspberry Pi (Raspberry Pi OS) interchangeably). The wip/asahi patches currently break amd64 builds due to a new entry in the APT preferences file, but this can be fixed (I didn't do so yet because, as I said, the Asahi patches cannot be upstreamed anyway, more on this later). Both the wip/arm64 and the wip/asahi images use GRUB for arm64 as a boot loader. For the former, this is all there is at the moment, meaning that the image can run in a VM, but may not run on hardware that needs special firmware or arrangements to make it boot. As for the latter, GRUB is all that's needed to boot on bare metal Apple Silicon (from the Tails side, that is). For those unfamiliar with the boot process on arm64 Apple hardware, here's a quick recap. Out of the box, Apple Silicon does not support booting from external media, nor of course booting Linux. It does, however, support booting multiple macOSes from internal storage. The smart folks at Asahi Linux (https://asahilinux.org/) came up with a process to boot Linux both from internal and external storage (there may be issues with booting from large external hard drives, but this is not relevant to Tails). What they do is they install a fake macOS on the hard drive, which after a couple of intermediate steps runs the U-Boot boot loader (https://docs.u-boot.org/en/latest/), which is then able to run GRUB both from internal and from external storage. This mechanism is currently in use to run, among others, the official remix of Fedora for Apple Silicon (https://asahilinux.org/fedora/), and - except for the part where you actually have to install the boot loader and for a second small exception, see below - is 100% transparent to the user. So how do you boot Tails on Apple Silicon? 1) Install U-Boot on your Apple Silicon Mac. This can be done using the official Asahi installer (see https://asahilinux.org/): curl https://alx.sh | sh The correct option, which should only require around 3GB of storage space on a separate partition, is "EFI environment only (m1n1 + U-Boot + ESP)" and, crucially, does not require you to install a fully-fledged Linux OS like Fedora. Once you do so, the U-Boot partition will be set as the default boot partition. This can be reverted at any time if you want to boot macOS by default instead (as you probably do in the context of Tails). Also, the U-Boot partition can be deleted at any moment if you don't need it anymore 2) Burn the Asahi Tails image onto a USB drive as usual 3) Plug the USB drive into your Mac. If the U-Boot partition is the default boot partition, just turn on your Mac. If it isn't, turn it on by keeping the power button pressed until it says "Entering startup options..." and then releasing it. At that point you can select the U-Boot partition (similarly, if the U-Boot partition is the default and you want to boot macOS, do the same but select the macOS partition) 4) Hit ESC when U-Boot says you can do so in order to interrupt the boot process and get dropped to a command line. Now you must tell U-Boot you want to boot from an external USB (this is the second small exception mentioned above): on the command line, execute env set boot_efi_bootmgr run bootcmd_usb0 This is the officially supported way to boot from an external USB drive. Maybe at some point U-Boot will support doing so without the user entering any command, but that's not possible at the moment AFAIK. 5) That's it. You're in If you happen to already have Asahi Linux installed on your arm64 Mac, you don't need to follow Step 1 as U-Boot comes installed with the OS. Just choose your Asahi Linux boot partition in Step 3. As for the arm64 port itself, i.e. what's in the images. Both wip/arm64 and wip/asahi are forked from feature/bookworm. The arm64 packages that are available from the official Debian repositories are installed from there (more on this later), whereas the Tails-specific packages (notably: live-boot, cryptsetup, fontconfig and n
[Tails-dev] FWD: Re: Tails for arm64 (with support for Apple Silicon)
Resending this so it reaches the whole mailing list. --- *** For the casual reader: please do not use this version of Tails. This is just a developer preview, it won't protect you like official releases do *** Hi David, At https://mega.nz/folder/BrJFGQyR#8rsN06I_pC_YV6spqATeBA you will find a third image, based on the "wip/raspi" branch at https://gitlab.tails.boum.org/noisycoil/tails, that boots and works on a Raspberry Pi 5 via USB (but should also work on other arm64 Raspberrys - I have none to test it at the moment). This image did not undergo much testing: it boots and connects to the internet via Tor, and the Tor Browser works as well; this is most of what I can say. I already see it needs some tweaks. For instance, after the first boot - which changes the main partition's UUID -, you need to manually edit the "cmdline.txt" file and write in the new UUID (you need to do this only once). In production this could be dealt with via an initramfs hook that checks if there's a mismatch and fixes it automatically. Also, Onionshare doesn't work and the initramfs-shutdown service fails due to /usr/local/bin/tails-get-bootinfo knowing nothing about how booting on the Pi works. In principle, making a universal arm64 image could be possible, but asides from the firmware (storing different firmware for different platforms on the same image may be feasible), the software and drivers may need different tweaks for different platforms. Quite a few Debian-based distros are providing different arm images for different platforms. Best, NC ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tails for arm64 (with support for Apple Silicon)
*** For the casual reader: please do not use this version of Tails. This is just a developer preview, it won't protect you like official releases do *** Hey there, During the last few weeks I've been working on porting Tails to the arm64 architecture, with the aim to ultimately being able to run Tails on Apple hardware again. If anyone is interested in a developer preview, you will find two USB images at https://mega.nz/folder/BrJFGQyR#8rsN06I_pC_YV6spqATeBA. The code is hosted at https://gitlab.tails.boum.org/noisycoil/tails in the "wip/arm64" and "wip/asahi" branches. The former enables general arm64 support, while the latter contains additional, currently non-upstreamable patches that make Tails run on Apple Silicon with M1/M2 processors (no M3 support yet). In both cases, the builds are native (you must build the arm64 version of Tails on arm64 hardware; I've been building it on Apple Silicon (Asahi Debian) and on a Raspberry Pi (Raspberry Pi OS) interchangeably). The wip/asahi patches currently break amd64 builds due to a new entry in the APT preferences file, but this can be fixed (I didn't do so yet because, as I said, the Asahi patches cannot be upstreamed anyway, more on this later). Both the wip/arm64 and the wip/asahi images use GRUB for arm64 as a boot loader. For the former, this is all there is at the moment, meaning that the image can run in a VM, but may not run on hardware that needs special firmware or arrangements to make it boot. As for the latter, GRUB is all that's needed to boot on bare metal Apple Silicon (from the Tails side, that is). For those unfamiliar with the boot process on arm64 Apple hardware, here's a quick recap. Out of the box, Apple Silicon does not support booting from external media, nor of course booting Linux. It does, however, support booting multiple macOSes from internal storage. The smart folks at Asahi Linux (https://asahilinux.org/) came up with a process to boot Linux both from internal and external storage (there may be issues with booting from large external hard drives, but this is not relevant to Tails). What they do is they install a fake macOS on the hard drive, which after a couple of intermediate steps runs the U-Boot boot loader (https://docs.u-boot.org/en/latest/), which is then able to run GRUB both from internal and from external storage. This mechanism is currently in use to run, among others, the official remix of Fedora for Apple Silicon (https://asahilinux.org/fedora/), and - except for the part where you actually have to install the boot loader and for a second small exception, see below - is 100% transparent to the user. So how do you boot Tails on Apple Silicon? 1) Install U-Boot on your Apple Silicon Mac. This can be done using the official Asahi installer (see https://asahilinux.org/): curl https://alx.sh | sh The correct option, which should only require around 3GB of storage space on a separate partition, is "EFI environment only (m1n1 + U-Boot + ESP)" and, crucially, does not require you to install a fully-fledged Linux OS like Fedora. Once you do so, the U-Boot partition will be set as the default boot partition. This can be reverted at any time if you want to boot macOS by default instead (as you probably do in the context of Tails). Also, the U-Boot partition can be deleted at any moment if you don't need it anymore 2) Burn the Asahi Tails image onto a USB drive as usual 3) Plug the USB drive into your Mac. If the U-Boot partition is the default boot partition, just turn on your Mac. If it isn't, turn it on by keeping the power button pressed until it says "Entering startup options..." and then releasing it. At that point you can select the U-Boot partition (similarly, if the U-Boot partition is the default and you want to boot macOS, do the same but select the macOS partition) 4) Hit ESC when U-Boot says you can do so in order to interrupt the boot process and get dropped to a command line. Now you must tell U-Boot you want to boot from an external USB (this is the second small exception mentioned above): on the command line, execute env set boot_efi_bootmgr run bootcmd_usb0 This is the officially supported way to boot from an external USB drive. Maybe at some point U-Boot will support doing so without the user entering any command, but that's not possible at the moment AFAIK. 5) That's it. You're in If you happen to already have Asahi Linux installed on your arm64 Mac, you don't need to follow Step 1 as U-Boot comes installed with the OS. Just choose your Asahi Linux boot partition in Step 3. As for the arm64 port itself, i.e. what's in the images. Both wip/arm64 and wip/asahi are forked from feature/bookworm. The arm64 packages that are available from the official Debian repositories are installed from there (more on this later), whereas the Tails-specific packages (notably: live-boot, cryptsetup, fontconfig and n
[Tails-dev] Tails report for December 2023
Tails report for December 2023 <https://tails.net/news/report_2023_12/> Happy 2024, Tails-y folks! We wish you a year full of nourishing energies, forceful resistance, and great health ✊ Highlights * 2023 was an eventful year at Tails. We kicked off the 1st year of our 3-year strategic plan with 16 releases of Tails, significant improvements to core Tails features like the new Persistent Storage, and researched cool, new features we want to bring to you. In parallel, we started moving into a new home <https://tails.net/> and made investments to become a more sustainable project and a healthier workplace. Read more about 2023 at Tails here <https://tails.net/news/achievements_in_2023/index.en.html>. If you'd rather listen, check out our presentation <https://www.youtube.com/watch?v=TtgTwho1wfQ=784s> at State of the Onion 2023! * We are raising funds for our work in 2024 but our annual fundraising campaign has fallen short of our goal. So, we've extended our fundraiser till January 20, 2024. If you find our work useful and can contribute, we'd appreciate your help. Every contribution, no matter the size, makes a big difference. Donate now! <https://tails.net/donate/> * Talking about contributions that make a difference, we remain ever so grateful to our sponsors! Last month, wordsolver.co <https://wordsolver.co/> renewed their sponsorship of Tails. This is the 3rd year of their support for Tails' mission! Thank you Releases We released Tails 5.21 <https://tails.net/news/version_5.21/index.en.html>. In 5.21: * /Tor client/ and /Tor Browser/ are up-to-date * we improved Tails's handling of date and time: you'll find localised dates in the top navigation, and separately, we replaced the unpunctual web servers in our htpdate pool * the backup feature of /Tails Cloner/ is friendlier to use. Thanks @BenWestgate <https://gitlab.tails.boum.org/BenWestgate>! And lots more <https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog>. Metrics Tails was started more than 815,559 times this month. That's a daily average of over 26,300 boots. -- bokonon Fundraising Director Tails —https://tails.boum.org/ OpenPGP_0x91A6C14953C2422C.asc Description: OpenPGP public key OpenPGP_signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] patch to fix #20079
Hi, I guess I don't have write access to the repo, so I can not create a MR... So I will do as stated on your website: " "You can submit small, easy changes as Git patches (prepared with the git format-patch command) over email to [tails-dev@boum.org](https://tails.net/about/contact/index.en.html#tails-dev)." " here is a patch to fix https://gitlab.tails.boum.org/tails/tails/-/issues/20079 Cheers, g4kw Sent with [Proton Mail](https://proton.me/) secure email.From 09f25ab2a64f3bfe488d4c9c02f3e51583b1f9e6 Mon Sep 17 00:00:00 2001 From: g4kw Date: Fri, 12 Jan 2024 17:56:40 +0100 Subject: [PATCH] adding PyQt5 - needed for Electrum --- config/chroot_local-packageslists/tails-common.list | 2 ++ 1 file changed, 2 insertions(+) diff --git a/config/chroot_local-packageslists/tails-common.list b/config/chroot_local-packageslists/tails-common.list index 79d3d5074e..d560e42e4d 100644 --- a/config/chroot_local-packageslists/tails-common.list +++ b/config/chroot_local-packageslists/tails-common.list @@ -47,6 +47,8 @@ eject # Needed by Additional Software python3-apt python3-atomicwrites +# Needed for Electrum +python3-pyqt5 # Needed by the Greeter console-setup gir1.2-accountsservice-1.0 -- 2.39.2 ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.21
# [Tails 5.21](https://tails.net/news/version_5.21/index.en.html) # Changes and updates * Help troubleshoot when resizing the system partition fails the first time Tails is started.  * Translate the date displayed in the top navigation bar.  * Update _Tor Browser_ to [13.0.7](https://blog.torproject.org/new-release-tor-browser-1307). * Update the _Tor_ client to 0.4.8.10. # Fixed problems * Fix _Tor Browser_ crashing when clicking on the _UBlock_ icon. ([#20061](https://gitlab.tails.boum.org/tails/tails/-/issues/20061)) * Make time synchronization more reliable. ([#19923](https://gitlab.tails.boum.org/tails/tails/-/issues/19923)) * [@BenWestgate](https://gitlab.tails.boum.org/@BenWestgate) fixed several issues in the backup feature of _Tails Cloner_ : * Remove message about doing a backup when no USB stick is plugged in. ([#20063](https://gitlab.tails.boum.org/tails/tails/-/issues/20063)) * Update available options when plugging in another USB stick. ([#20042](https://gitlab.tails.boum.org/tails/tails/-/issues/20042)) * Point to backup instructions when choosing to clone the Persistent Storage. ([!1305](https://gitlab.tails.boum.org/tails/tails/-/merge_requests/1305)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Get Tails 5.21 ## To upgrade your Tails USB stick and keep your Persistent Storage * Automatic upgrades are available from Tails 5.0 or later to 5.21. You can [reduce the size of the download](https://tails.net/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.net/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.net/install/windows/index.en.html) * [Install from macOS](https://tails.net/install/mac/index.en.html) * [Install from Linux](https://tails.net/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.net/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.21 directly: * [For USB sticks (USB image)](https://tails.net/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.net/install/download-iso/index.en.html) URL: <https://tails.net/news/version_5.21/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] 2023 at Tails: a new home, small steps, and giant leaps
# [2023 at Tails: a new home, small steps, and giant leaps](https://tails.net/news/achievements_in_2023/index.en.html) **Malicious actors upped the ante in 2023.** So-called artificial intelligence systems soared in popularity, supercharging political [disinformation](https://www.wired.com/story/slovakias-election- deepfakes-show-ai-is-a-danger-to-democracy/) [programs](https://www.theguardian.com/us-news/2023/jul/19/ai-generated- disinformation-us-elections). Internet shutdowns and slowdowns became [firmly entrenched](https://www.accessnow.org/publication/internet-shutdowns- in-2023-mid-year-update/) in authoritarian toolkits to censor progressive speech. And the [continuing revelations](https://securitylab.amnesty.org/latest/2023/11/serbia-civil- society-threatened-by-spyware/) of zero-click attacks drove home the perilous omnipotence of the military-digital complex. **But, we also made plans to call their ante.** We built a state-of-the-art 3-year strategy to make Tails a formidable adversary to these powerful, repressive forces. We made plans to better understand the use of Tails by journalists and activists, and understand and improve the use of Tails in the [majority world](https://www.harvarddesignmagazine.org/articles/shahidul-alam-on-the- majority-world/). All this while introducing new features and improvements to existing features that make Tails even more relevant. Here's the progress we made in the first year of the plan. ## Product development **The Persistent Storage got even better at storing encrypted data.** [Tails 5.8](https://tails.net/news/version_5.8/index.en.html) was one of the most important Tails releases in years. In Tails 5.8, we unveiled a brand new Persistent Storage. The new Persistent Storage doesn't require restarting after creation or any time after you activate a new feature. It also made it easier to persist more settings. The icing on the cake: a dashing makeover for the Persistent Storage! But the new Persistent Storage wasn't all fun and games for Tails users. It was buggy and we worked extra hard to fix the issues our users faced. We didn't stop there. We also continued to add functionality to the Persistent Storage. Now, it is easier to both do [backups of the whole Persistent Storage](https://tails.net/news/version_5.14/index.en.html) and [delete the data of a each feature](https://tails.net/news/version_5.12/index.en.html). New button to delete the data of a Persistent Storage feature[](https://tails.net/news/version_5.12/delete-data.png) --- Option to clone the current Persistent Storage in Tails Installer[](https://tails.net/doc/persistent_storage/backup/clone.png) --- We also introduced better password practices for securing the Persistent Storage. Randomly generated [diceware](https://diceware.dmuth.org/) passphrases and an upgraded encryption format make the Persistent Storage [exponentially more secure](https://tails.net/security/argon2id/index.en.html).  **Improvements to the[Tor Connection](https://tails.net/news/version_4.20/index.en.html) make it easier to circumvent censorship.** The Tor Connection Assistant is slicker. We improved the error messaging when connecting automatically to the Tor network and the handling of captive portals. Connecting to Tor is only part of the story. At times, Tails users may find themselves on slow Tor circuits. And worse, unable to troubleshoot issues. So, we've made it easier to close pesky Tor circuits that we can sometimes land on. Option to close a circuit in Onion Circuits[](https://tails.net/news/version_5.19/close_circuit.png) --- **Tails remains one of the most secure operating systems in the world.** This year, we released 15 versions of Tails, ensuring users had the latest Tor Browser and Thunderbird. Yes, FIFTEEN! We also asked [Radically Open Security](https://www.radicallyopensecurity.com/) to do a security audit of Tails. Their [findings](https://tails.net/news/audit_by_ROS/index.en.html) affirmed our cutting-edge security. PS: Keeping Tails updated is your best defense against online surveillance and censorship! **And we started moving to our new home!** ✨ tails.net ✨ We completed a bunch of home improvement projects. So our new home is even more welcoming to folks speaking different languages, we overhauled the language switcher. We just added Catalan translations too. _Gr acies per ser aqui!_ [](https://tails.net/news/achievements_in_2023/language_switcher.png) High footfall areas of the website got a new carpet too. Check out our new [Contribute](https://tails.net/contribute/index.en.html), [Support](https://tails.net/support/index.en.html), and [Contact us
[Tails-dev] Technical Issue
Hello, I sent a message ten days ago and never got a response. Is this a good email to ask about technical issues?___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tails report for November 2023
Hello :) * Tails report for November 2023 <https://tails.net/news/report_2023_11/>* Highlights * We had asked Radically Open Security <https://www.radicallyopensecurity.com/> to audit Tails. The results of the audit <https://tails.net/news/audit_by_ROS/index.en.html> reinforced Tails credentials as a "solid" operating system for preserving anonymity. We were super proactive with addressing the reported vulnerabilities, fixing them all within 3 weeks of being reported. This is a reminder that as good as Tails is, it needs to be updated regularly! * We undertook a bunch of home improvement projects for our new address <https://tails.net/news/new_domain/index.en.html>. Highlights: o the language switcher on the website is more prominent, and also in the website footer, o warning buttons display warnings better - in a new colour, and with wrapped text, o our redesigned security page <https://tails.net/security/index.en.html> better showcases the history of our security advisories. * We have a new sponsor: igaming.com <https://www.igaming.com/> joined our mission! Our donors also received the quarterly newsletter with early insights into upcoming Tails features. You, too, could subscribe while making your next donation <https://tails.net/donate/index.en.html>. Help make our ongoing fundraiser <https://tails.net/news/gift_of_privacy/index.en.html> a success! Releases November featured 2 new versions of Tails: 5.19.1 and 5.20. 5.19.1 <https://tails.net/news/version_5.19.1/index.en.html> was an emergency release. We updated the Tor client to bring the fix to the TROVE-2023-006 vulnerability <https://gitlab.torproject.org/tpo/core/team/-/wikis/NetworkTeam/TROVE> to Tails users. And in 5.20 <https://tails.net/news/version_5.20/index.en.html>, we: * brought the usual, latest updates to Tor Browser and Thunderbird, * fixed a security vulnerability in uBlock Origin to protect Tails users from advanced browser fingerprinting techniques, and * continued making Persistent Storage more usable, and made it even easier to report issues when it doesn't work through improvements to WhisperBack. Metrics Tails was started more than 825,741 times this month. That's a daily average of over 27,520 boots OpenPGP_0x91A6C14953C2422C.asc Description: OpenPGP public key OpenPGP_signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Randomize full MAC address feature option in welcome screen
>phone oui vendors resources to form oui list: It would make more sense for full mac randomization to copy how android does it wouldn't it? https://source.android.com/docs/core/connect/wifi-mac-randomization-behavior >The MAC randomization feature randomizes the address by setting the locally >administered bit to 1, and the unicast bit to 0. The other 46 bits are >randomized. https://en.wikipedia.org/wiki/File:MAC-48_Address.svg So to implement that like the Android feature does: 0X:00:00:00:00:00 ^ X would have to be 26ae reasoning is XX:00:00:00:00:00 would have to equal an 8 digit binary ending in 10 xx10 ^ determines the locally administered bit which has to be 1 ^ determines the unicast which has to be 0 https://richardatkin.com/post/2022/01/14/MAC-Address-Randomisation.html If you use this calculator u can see that 26ae are the only possible outcomes for this bit to end in 10 0X:00:00:00:00:00 ^ the first part can equal anything between 0-9 and a-f as it doesn’t change the binary ending in 10 X = 2 or 6 or a or e [26ae] https://www.compscilib.com/calculate/mac-address-to-binary? The first part could be anything [0-9a-f] but the the second part would have to be [26ae] then the rest (10) randomized. [0-9a-f][26ae]:00:00:00:00:00 echo $(/usr/bin/tr -dc a-f0-9 https://proton.me/) secure email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Set Tor Browser homepage to offline html of tails.net
Tor Browser pings tails.net every time the browser is launched.
This could lead to fingerprinting tails users more on a circuit.
Tca from my understanding already sends requests to tails.net every time tails
is booted to check for updates and for feedback to understand how many people
are booting/using tails.
Changing the startup homepage to `/usr/share/doc/tails/website/index.en.html`
would make it so users can still see the Tails News and Documentation while
also avoiding pinging tails.net more then needed on a circuit.
The only downside would be that users would only see the latest news regarding
their current version as the offline documentation is only current with the
version users are on.
(Offline documentation is updated every new update.)
What are your thoughts on setting this pref?
user_pref("browser.startup.homepage",
"/usr/share/doc/tails/website/index.en.html");
Sent with [Proton Mail](https://proton.me/) secure email.___
Tails-dev mailing list
Tails-dev@boum.org
https://www.autistici.org/mailman/listinfo/tails-dev
To unsubscribe from this list, send an empty email to
tails-dev-unsubscr...@boum.org.
[Tails-dev] want to stop tails going into sleep mode when I close lid
Hi, I have tried for some time to find a working answer to this issue - to no avail. The issue is that I want to be able to leave tails running various processes when I close the lid of my laptop, or turn off my monitor, or simply leave it untouched for a while. There doesn't seem to be a way of doing this, not that I have been able to find anyway. I would be very grateful if you could please help me with this. Kind regards, J___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.19.1
# [Tails 5.19.1](https://tails.boum.org/news/version_5.19.1/index.en.html) This release is an emergency release to fix an important security vulnerability in Tor. # Changes and updates * Update the _Tor_ client to 0.4.8.9, which fixes the TROVE-2023-006 vulnerability. The details of TROVE-2023-006 haven't been disclosed by the Tor Project to leave time for users to upgrade before revealing more. We only know that the Tor Project describes TROVE-2023-006 as a "[ _remote triggerable assert on onion services_](https://gitlab.torproject.org/tpo/core/team/-/wikis/NetworkTeam/TROVE)". Our team thinks that this vulnerability could affect Tails users who are creating onion services from their Tails, for example when sharing files or publishing a website using _OnionShare_. This vulnerability might allow an attacker who already knows your _OnionShare_ address to make your Tor client crash. A powerful attacker might be able to further exploit this crash to reveal your IP address. This analysis is only a hypothesis because our team doesn't have access to more details about this vulnerability. Still, we are releasing this emergency release as a precaution. _OnionShare_ is the only application included in Tails that creates onion services. You are not affected by this vulnerability if you don't use _OnionShare_ in Tails and only use Tails to connect to onion services and don't create onion services using Additional Software. More details about TROVE-2023-006 will be available on the [Tor issue #40883](https://gitlab.torproject.org/tpo/core/tor/-/issues/40883) sometime after the release. # Fixed problems For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.19.1 ## To upgrade your Tails USB stick and keep your Persistent Storage * Automatic upgrades are available from Tails 5.0 or later to 5.19.1. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.19.1 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) URL: <https://tails.boum.org/news/version_5.19.1/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Security audit of Persistent Storage and Tor integration
# [Security audit of Persistent Storage and Tor integration](https://tails.boum.org/news/audit_by_ROS/index.en.html) In March 2023, [Radically Open Security](https://www.radicallyopensecurity.com/) conducted a security audit on the major improvements that we released in [Tails 5.8](https://tails.boum.org/news/version_5.8/index.en.html) (December 2022) on the Persistent Storage, the Unsafe Browser, and the Wayland integration. To better protect our users, we addressed most of the security vulnerabilities as soon as they were discovered and reported to us, without waiting for the audit to be complete and public. We can now share with your the [final report](https://gitlab.tails.boum.org/tails/tails/uploads/df935595f41faa687805136a6bfa2910/tails- ros-penetration-test-report-1-2.pdf). We are proud of the conclusion of the auditors: > **_Overall, the Tails operating system left a solid impression and addressed > most of the concerns of an average user in need of anonymity._** > > _This is particularly evident in the isolation of various components by the > developers. For example, the configured AppArmor rules often prevented a > significant impact of the found vulnerabilities. Shifting to Wayland was a > good decision, as it provides more security by isolating individual GUI > applications._ > > _All in all, no serious vulnerabilities were found through the integration > into Wayland. Unsafe Browser and Persistent Storage should now be less > vulnerable to attack, as all vulnerabilities have been fixed._ The auditors found 6 _High_ , 1 _Moderate_ , 3 _Low_ -severity issues. Another issue was fixed before the actual impact was assessed and so marked as having _Unknown_ severity. We fixed all these issues as soon as possible and before making them public on our GitLab. The last issue was fixed in 5.14, 3 weeks after it was reported to us. As good as the results of this audit are, they also serve as a reminder that no software is ever 100% secure and that every release of Tails can fix critical security vulnerabilities. Your best protection against all kinds of attack is to keep your Tails up-to-date. Because at Tails we believe that transparency is key to building trust, all the code of our software is public and the results of this audit as well. You can find below a summary of all the issues and their fixes. # Detailed findings ## Tor integration ID| Issue| Description| Impact| Status| Release ---|---|---|---|---|--- TLS-012| [#19585](https://gitlab.tails.boum.org/tails/tails/-/issues/19585)| Leak clear IP as low-privileged user amnesia| High| Fixed| 5.12 TLS-013| [#19594](https://gitlab.tails.boum.org/tails/tails/-/issues/19594)| Local privilege escalation to Tor Connection sandbox| High| Fixed| 5.12 TLS-014| [#19595](https://gitlab.tails.boum.org/tails/tails/-/issues/19595)| Local privilege escalation to Tor Browser sandbox| Moderate| Fixed| 5.13 TLS-017| [#19610](https://gitlab.tails.boum.org/tails/tails/-/issues/19610)| Insecure permissions of chroot overlay| Unknown| Fixed| 5.13 ## Persistent Storage ID| Issue| Description| Impact| Status| Release ---|---|---|---|---|--- TLS-003| [#19546](https://gitlab.tails.boum.org/tails/tails/-/issues/19546)| Local privilege escalation in Persistent folder activation hook| High| Fixed| 5.11 TLS-004| [#19547](https://gitlab.tails.boum.org/tails/tails/-/issues/19547)| Symlink attack in Persistent folder deactivation hook| Low| Fixed| 5.11 TLS-005| [#19548](https://gitlab.tails.boum.org/tails/tails/-/issues/19548)| Local privilege escalation in GnuPG feature activation hook| High| Fixed| 5.11 ## Core ID| Issue| Description| Impact| Status| Release ---|---|---|---|---|--- TLS-001| [#19464](https://gitlab.tails.boum.org/tails/tails/-/issues/19464)| Local privilege escalation in tails-shell-library| High| Fixed| 5.11 TLS-009| [#19599](https://gitlab.tails.boum.org/tails/tails/-/issues/19599)| Man-in-the-middle attack on onion-grater service| Low| Fixed| 5.13 TLS-011| [#19576](https://gitlab.tails.boum.org/tails/tails/-/issues/19576)| Limited path traversal in tails-documentation| Low| Fixed| 5.13 TLS-019| [#19677](https://gitlab.tails.boum.org/tails/tails/-/issues/19677)| Local privilege escalation in tailslib leads to arbitrary file read| High| Fixed| 5.14 URL: <https://tails.boum.org/news/audit_by_ROS/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. _______ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tails default encryption app - Zulucrypt an option?
Hi there, Firstly sincere apologies if this is the wrong way to go about this. I wasn't able to create a Gitlab account anonymously to post a request there. I have a feature request for Tails 6.0 (or roadmap) I hope merits discussion: It would be ideal for Tails to replace the "Unlock Veracrypt Volumes" application with another app already offered in the package manager - Zulucrypt, OR a analagous app that offers similar features. My main reasons are: * Functionality. The "Unlock Veracrypt Volumes" only allows you to unlock volumes first created on other systems. I believe this creates a potential security threat for users who might use an insecure, non-amensiac platform to create this volume and leave traces behind. Zulucrypt allows both the creation AND unlocking of many types of encryption volumes, not just Veracrypt - enhancing the OOTB usefulness of Tails without adding large filesize or a steep learning curve for most features. * Stenanography (and plausible deniability). An popular encryption method of hiding in plain sight, steganography is great (though not a silver bullet) - however in the current versions of Tails, you have to manually install Zulucrypt in order to use it (that is, unless you invest the time into becoming a CLI expert, most users won't). The mere existence of Zulucrypt being installed on a user's Tails today can alert an adversary to the potential existence of a hidden container created via steganography. By having Zulucrypt installed for all users by default (like Parrot OS has) in place of the current app, everyone benefits from the potential to use steganography in addition to other encryption formats, without raising suspicion from the adversary. If they can force you to unlock your persistent storage, that doesn't necessarily have to be the end of your defenses against prying eyes - in fact the appearance of compliance might be useful. It appears the last time I could see this discussed was in 2016-17. Could this be reviewed afresh and considered for a future Tails update? Regards,Charlie___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.19
# [Tails 5.19](https://tails.boum.org/news/version_5.19/index.en.html) # New features ## Closing a Tor circuit from _Onion Circuits_ You can now close a given Tor circuit from the _Onion Circuits_ interface. This can help replace a particularly slow Tor circuit or troubleshoot issues on the Tor network. 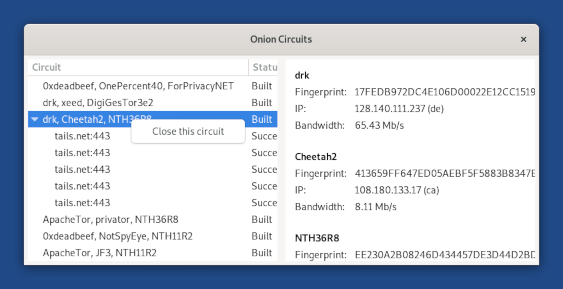 To close a Tor circuit: 1. [Connect to the Tor network.](https://tails.boum.org/doc/anonymous_internet/tor/index.en.html) 2. Choose  ▸ **Open Onion Circuits** in the top navigation bar. 3. Right-click (on Mac, click with two fingers) on the circuit that you want to close. 4. Choose **Close this circuit** in the shortcut menu. When you close a circuit that is being used by an application, your application gets disconnected from this destination service. For example, when you close a circuit while _Tor Browser_ is downloading a file, the download fails. 5. If you connect to the same destination server again, Tor uses a different circuit to replace the circuit that you closed. For example, if you download the same file again, Tor uses a new circuit. ## Addition of sq-keyring-linter At the request of people who use [SecureDrop](https://securedrop.org/) to provide secure whistleblowing platforms across the world, we added the [`sq- keyring-linter`](https://tracker.debian.org/pkg/rust-sequoia-keyring-linter) package. `sq-keyring-linter` improves the cryptographic parameters of PGP keys stored in their airgapped machines. # Changes and updates * Update _Tor Browser_ to [13.0.1](https://blog.torproject.org/new-release-tor-browser-1301). * Update the _Tor_ client to 0.4.8.7. * Update _Thunderbird_ to [115.4.1](https://www.thunderbird.net/en-US/thunderbird/115.4.1/releasenotes/). * Update the _Linux_ kernel to 6.1.55. # Fixed problems For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.19 ## To upgrade your Tails USB stick and keep your Persistent Storage * Automatic upgrades are available from Tails 5.0 or later to 5.19. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.19 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) URL: <https://tails.boum.org/news/version_5.19/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Make the gift of privacy!
# [Make the gift of privacy!](https://tails.boum.org/news/gift_of_privacy/index.en.html) With malicious actors' intrusions into human rights growing in sophistication and scale, Tails offers hope for those seeking refuge in a more secure digital environment. We stand on the precipice of a future where digital privacy should be a fundamental right, not a luxury.  Since we started in 2008, millions of people around the world have used Tails to be more secure, autonomous, and anonymous in their digital lives. We have come so far thanks to you, and need your support to continue to do what we do best: deliver the world's most privacy-preserving operating system! Your donations a lion's share [of our income](https://tails.boum.org/donate/index.en.html#income). But, this share has reduced in the last couple of years. Globally, philanthropic giving has fallen, in what is yet another symptom of the challenging political and economic conditions we find ourselves in. But this hasn't tempered our ambitions. Despite these challenges, Tails has gotten bigger and better over the past year. We have spent more time improving Tails this year than any previous year. But to achieve this, we have relied a bit more on support from large, institutional donors. While we are grateful for the support and generosity of our "large" donors, we want to keep our reliance on them to a minimum. We are betting on having diversified income streams as our insurance from economic volatility and assurance of growing Tails sustainably and with complete decisional autonomy. Although, this means that we rely on you even more. And hence this fundraiser! Our goal is clear: to make Tails even more useful for vulnerable people in high-risk environments. And we want to do this while remaining as autonomous as our users are. The proceeds from this fundraiser will drive initiatives that will make Tails even more usable and secure. We want to add new, big features to Tails, enhance user experience with even more usability tests, and increase Tails' use in more geographies around the world. Every donation, no matter how small, makes a difference. Please donate today and help us keep Tails alive and well in 2024 and beyond! Here are 5 ways you can get involved: 1. **By making a recurring donation.** [Recurring donations](https://tails.boum.org/donate/index.en.html) are the best insurance for Tails' mission. These help us weather economic uncertainties and plan our work sustainably. 2. **With a one-time gift.** If you can't set-up a recurring donation, you can make a [one-time donation](https://tails.boum.org/donate/index.en.html). Donate via PayPal, bank transfers, mail in your checks, or just send us good, old cash. Here's a pro-tip: donations of over $1 000 entitle you to some neat [sponsorship benefits](https://tails.boum.org/sponsors/become/). 3. **Through cryptocurrency.** We accept [crypto donations](https://tails.boum.org/donate/index.en.html) in Bitcoin, Ethereum, and Monero. 4. **Gift matching.** If your employer runs gift-matching programmes, consider looking up **Riseup Labs** and donate to **Tails via Riseup Labs**. Riseup Labs is our fiscal sponsor in the United States of America. 5. **Spread the word.** And finally, please share this fundraiser with your network, friends, and colleagues. Help us amplify our impact by reaching a wider audience! Thank you for being part of this journey and a toast to our future adventures together! Oh, and in case you have somehow managed to skip over all the links to our donations page so far, here it is: <https://tails.net/donate/>. URL: <https://tails.boum.org/news/gift_of_privacy/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Would like to join the Turkish translation team
Hello, I'd like to share my interest on joining the Turkish translation team for the tails project. I've worked on and contributed to many Open source projects, games and have worked under professional settings. publickey - EmailAddress(s=efemertkara06@proton.me) - 0x4255D998.asc Description: application/pgp-keys signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] protection from remote viewing?
Good day, What about protection against remote take over programs that intrude into smartphones and other devices and gain access, such as programs like Peg_ a _sus? Does this prohibit? Gracias. Sent with [Proton Mail](https://proton.me/) secure email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Please add firefox to Tails
Dear developers, I cannot check my email accounts in email.cz, yahoo, gmail.com because they refuse Tor browsers (Robot detected). For this reason, please add a standard Firefox to Tails to check email accounts. Sincerely, Tails user___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.16.1
# [Tails 5.16.1](https://tails.boum.org/news/version_5.16.1/index.en.html) This release is an emergency release to fix a critical vulnerability in the _Linux_ kernel. # Changes and updates * Update the _Linux_ kernel to 6.1.38. This updates fixes: * [Downfall](https://downfall.page/) on Intel processors ([CVE-2022-40982](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-40982)) * [Inception](https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7005.html) on AMD processors ([CVE-2023-20569](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-20569)) These vulnerability could allow a malicious application running in Tails to access and steal data from another application in Tails, for example passwords stored in _KeePassXC_ or private keys stored in _Electrum_. This attack is unlikely, but could be performed by a strong attacker, such as a government or a hacking firm. We are not aware of this attack being used in the wild. # Fixed problems For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.16.1 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.16.1. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.16.1 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) URL: <https://tails.boum.org/news/version_5.16.1/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] thanks for the hard work
dear tails developers, i'm emailing yaw just to let yaw know that yaw did a really great job on devevolping tails, it's nice to have it installed on a USB so i can be able to go online without being harrased by constant ads, i want to thank yaw for the hard work, because tails is the best linux OS that ive used so far. thank you. happy tails user ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.15.1
# [Tails 5.15.1](https://tails.boum.org/news/version_5.15.1/index.en.html) # Changes and updates * Update _Tor Browser_ to [12.5](https://blog.torproject.org/new-release-tor-browser-125). [Tor Browser 12.5](https://blog.torproject.org/new-release-tor-browser-125) has a new circuit view and better information about onion services.  * Support onion service authentication in _Tor Browser_. For example, onion service authentication is used by _OnionShare_ outside of Tails.  * Display the version of Tails in the Boot Loader  # Fixed problems * Fix the search of some languages and keyboard layouts. ([#19200](https://gitlab.tails.boum.org/tails/tails/-/issues/19200))  * Make the upgrade of the Persistent Storage more reliable: * On some systems, the message " _Upgrading the persistent storage_ " was displayed every time in Tails 5.14 when Tails failed to upgrade one of the cryptographic parameters. ([#19734](https://gitlab.tails.boum.org/tails/tails/-/issues/19734)) * On some USB sticks, upgrading the Persistent Storage was too slow and failed with the error message " _Upgrade of persistent storage failed_ ". ([#19728](https://gitlab.tails.boum.org/tails/tails/-/issues/19728)) * Fix opening documentation links from _Tails Installer_. ([#19870](https://gitlab.tails.boum.org/tails/tails/-/issues/19870)) * Prevent _Tor Browser_ to access information about other Tor circuits. ([#19740](https://gitlab.tails.boum.org/tails/tails/-/issues/19740)) * Make the error when scanning the QR code of a bridge more consistent. ([#19737](https://gitlab.tails.boum.org/tails/tails/-/issues/19737)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues [#19728](https://gitlab.tails.boum.org/tails/tails/-/issues/19728) was affecting 5.14, and it might still be present. If you encounter this bug, please [send us a _WhisperBack_ report](https://tails.boum.org/doc/first_steps/bug_reporting/index.en.html#whisperback). See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.15.1 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.15.1. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.15.1 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) URL: <https://tails.boum.org/news/version_5.15.1/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. _______ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Moving to a new domain: tails.net
Hello! Below is an update of the move to tails.net. "Tails Sysadmins" writes: > Hello, dear Tails contributors! > > Last year we acquired the "tails.net" domain and, since then, we started > taking incremental steps to implement it throughout the Tails OS and > infra[1][2]. > > We'd like to announce two big changes on this front: > > - Tails 5.14 (just released a few moments ago) is the first release to > use the new "tails.net" domain in its internals (except for the > included doc which is a copy of the current website). > > - In a couple of weeks we'll change the hardcoded links in the Tails > website source to start using the new domain. The updated > website/doc will be included in the next Tails release. This happened: https://gitlab.tails.boum.org/tails/tails/-/commit/49082bd5b077b182a77a7fdad3ba15c566b31e36 > For fellow translators: When we do the website source change, we'll try > to minimize the impact it'll have on the invalidation of current > translations. But, please, beware that you may find parts that will > need to be manually updated after the change is effective. This also happened, and I tried to avoid all invalidations, but please keep an eye and make sure to use the new tails.net domain from now on. :) These were the changes made to .po files: https://gitlab.tails.boum.org/tails/tails/-/commit/512e9ba37c009d6ffbbcfdd397ab0e94581e4376 https://gitlab.tails.boum.org/tails/tails/-/commit/c5518d57b505786ef3566d78d7a264dfbab58946 https://gitlab.tails.boum.org/tails/tails/-/commit/14de266b236b60ccff74fc1cbbdc15d577d195a6 > Thank you very much for all your support! Yes, thanks! The Tails Sysadmins -- signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.14
# [Tails 5.14](https://tails.boum.org/news/version_5.14/index.en.html) # New features ## Automatic migration to LUKS2 and Argon2id The cryptographic parameters of LUKS from Tails 5.12 or earlier are weak against a state-sponsored attacker with physical access to your device. To use stronger encryption parameters, Tails 5.14 automatically converts your Persistent Storage to use LUKS2 encryption with Argon2id. Still, we recommend you change the passphrase of your Persistent Storage and other LUKS encrypted volumes unless you use a long passphrase of 5 random words or more. [Read our security advisory and upgrade guide.](https://tails.boum.org/security/argon2id/index.en.html) ## Full backups from Tails Installer You can now do a backup of your Persistent Storage from _Tails Installer_ by cloning your Persistent Storage to your backup Tails entirely. 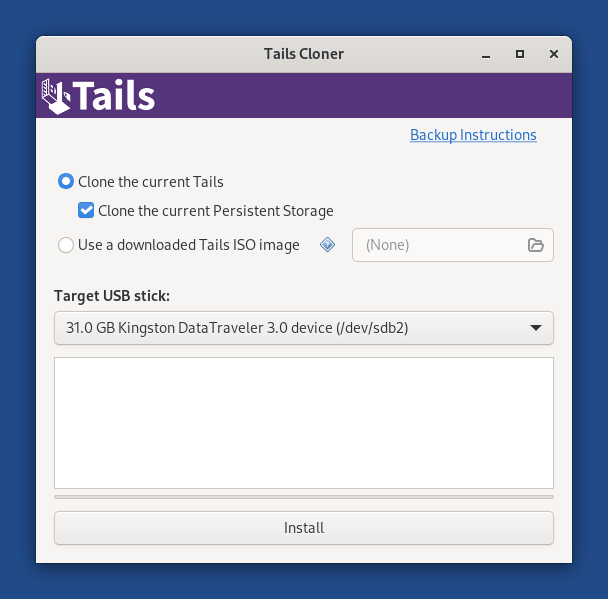 You can still use the backup utility to go faster while [updating your backup](https://tails.boum.org/doc/persistent_storage/backup/index.en.html#updating). ## Captive portal detection Tails now detects if you have to sign in to the network using a captive portal if you choose to connect to Tor automatically. The error screen appears more quickly and recommends you try to sign in to the network as the first option. ## Incentive to donate from _Electrum_ Many people use Tails to secure their Bitcoin wallet and donations in Bitcoin are key to the survival of our project, so we integrated a way to donate from _Electrum_ in Tails.  # Changes and updates ## Included software * Update _Tor Browser_ to [12.0.7](https://blog.torproject.org/new-release-tor-browser-1207). ## Usability improvements to the Persistent Storage * Change the button to create a Persistent Storage from the Welcome Screen to be a switch. ([#19673](https://gitlab.tails.boum.org/tails/tails/-/issues/19673))  * Add back the description of some of the Persistent Storage features and mention _Kleopatra_ in the _GnuPG_ feature. ([#19642](https://gitlab.tails.boum.org/tails/tails/-/issues/19642) and [#19675](https://gitlab.tails.boum.org/tails/tails/-/issues/19675))  * Hide the duplicated _Persistent_ bookmark in the _Files_ browser. ([#19646](https://gitlab.tails.boum.org/tails/tails/-/issues/19646)) # Fixed problems For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). * Avoid restarting the desktop environment when creating a Persistent Storage. ([#19667](https://gitlab.tails.boum.org/tails/tails/-/issues/19667)) # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.14 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.14. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.14 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) URL: <https://tails.boum.org/news/version_5.14/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Moving to a new domain: tails.net
Hello, dear Tails contributors! Last year we acquired the "tails.net" domain and, since then, we started taking incremental steps to implement it throughout the Tails OS and infra[1][2]. We'd like to announce two big changes on this front: - Tails 5.14 (just released a few moments ago) is the first release to use the new "tails.net" domain in its internals (except for the included doc which is a copy of the current website). - In a couple of weeks we'll change the hardcoded links in the Tails website source to start using the new domain. The updated website/doc will be included in the next Tails release. For fellow translators: When we do the website source change, we'll try to minimize the impact it'll have on the invalidation of current translations. But, please, beware that you may find parts that will need to be manually updated after the change is effective. Note that the full migration of the website will still take some time, as it involves several details and steps[3], and that the old domain will continue to be used in different parts of the infra until we eventually have the means to phase it out[4]. Thank you very much for all your support! The Tails Sysadmins -- [1] https://gitlab.tails.boum.org/tails/sysadmin/-/issues/17952 [2] https://gitlab.tails.boum.org/tails/tails/-/issues/18263 [3] https://gitlab.tails.boum.org/tails/sysadmin/-/issues/17985 [4] https://gitlab.tails.boum.org/tails/sysadmin/-/issues/17987 -- signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Improving Tails for human rights defenders in Latin America
# [Improving Tails for human rights defenders in Latin America](https://tails.boum.org/news/improving_in_latam/index.en.html) Between 2021 and 2023 Tails, [Tor](https://torproject.org/), and the [Guardian Project](https://guardianproject.info/) partnered to organize training and usability tests in Ecuador, Mexico, and Brazil. Our goals were to: * Promote our digital security tools and train human rights defenders in the Global South. * Learn from their experiences and needs to help us prioritize future work. * Improve the usability of our tools based on their feedback. # Usability tests and improvements We conducted 4 rounds of in-person moderated usability tests in Mexico, Brazil, and Ecuador to identify usability issues in the features of Tails that are most important to new users: * Installation * Tor Connection * Persistent Storage The DesignOps tools that we used to organize these usability tests are all [publicly available on our website](https://tails.boum.org/contribute/how/user_experience/). The detailed methodology for each of the usability tests is explained in the corresponding GitLab issues, linked below. ### Installation In December 2021 in Mexico, we learned that the tools for new users to install Tails worked well, but several people got lost while navigating the instructions on the website. Based on these findings, we restructured our installation pages and fixed 30 usability issues on the website. We tested these improvements in August 2022 in Brazil and confirmed that the new installation pages were much easier to follow. Only 1 out of 4 participants had trouble installing Tails on their own. All participants could start Tails and connect to the Tor network easily. Details: * Usability tests of first-time use in Mexico ([#18074](https://gitlab.tails.boum.org/tails/tails/-/issues/18074)) * [Summary of findings](https://gitlab.tails.boum.org/tails/tails/-/issues/18074#note_210738) * [Detailed findings](https://gitlab.tails.boum.org/tails/ux/-/raw/master/first-time/rainbow_table.fods?inline=false) * Usability tests of first-time use in Brazil ([#18784](https://gitlab.tails.boum.org/tails/tails/-/issues/18784)) * [Summary of findings](https://lists.autistici.org/message/20221012.181235.a673efeb.en.html) * [Detailed findings](https://gitlab.tails.boum.org/tails/ux/-/blob/master/first-time/rainbow_table_installation_2022_08_Sao_Paulo.fods?inline=false) ### Tor Connection In July 2021, we released the Tor Connection assistant to completely redesign how to connect Tails to the Tor network. The new assistant is most useful to people who are at high risk of physical surveillance, under heavy network censorship, or on a poor Internet connection. In August 2022 in Brazil, we tested the usability of Tor Connection when accessing the Tor network is blocked by censorship or by a captive portal. Despite the many usability issues that we fixed since the first release of Tor Connection, 3 test participants out of 4 failed to connect when access to the Tor network was blocked. Since then we fixed 14 usability issues affecting Tor Connection: to understand better why connecting to Tor fails, to make it easier to configure a Tor bridge, and to make it easier to sign in to a network using a captive portal. * Usability tests of Tor Connection ([#18762](https://gitlab.tails.boum.org/tails/tails/-/issues/18762)) * [Summary of findings](https://lists.autistici.org/message/20221012.140611.7e58f067.en.html) * [Detailed findings](https://gitlab.tails.boum.org/tails/ux/-/raw/master/network/rainbow_table_tor_connection_2022_08_Sao_Paulo.fods?inline=false) ### Persistent Storage In March 2023 in Ecuador, we tested the usability of the new Persistent Storage, which was released in Tails in December 2022. We didn't find any serious usability issues in the new Persistent Storage. The fact that people don't have to restart to create and enable the Persistent Storage and that their data (eg. Wi-Fi password) is stored on creation were huge improvements compared to the old Persistent Storage. * March 2023: Usability tests of the new Persistent Storage ([#18648](https://gitlab.tails.boum.org/tails/tails/-/issues/18648)) * [Summary of findings](https://lists.autistici.org/message/20230510.091842.23ed75ba.en.html) * [Detailed findings](https://gitlab.tails.boum.org/tails/ux/-/raw/master/persistent%20storage/rainbow_table_persistent_storage_2023_03_Ecuador.fods?inline=false) # Trainings Through our combined efforts we reached 47 organizations and trained 433 human rights defenders on our family of tools based on the Tor network. For Tails only, we conducted 8 workshops and trained 84 people on using Tails: journalists, activists, feminists, lawyers, and human rights defenders. The material used for these Tails workshops is available on our website in [English](https://tails.boum.org/contribute/how/promote/material/slides
[Tails-dev] [PATCH] Fix incorrect usage of "discrete"
This doesn't retroactively fix news posts. Via Wiktionary: discrete (comparative more discrete, superlative most discrete) 1. Separate; distinct; individual; non-continuous. a government with three discrete divisions 2. That can be perceived individually, not as connected to, or part of, something else. discreet (comparative more discreet or discreeter, superlative most discreet or discreetest) 1. Respectful of privacy or secrecy; exercising caution in order to avoid causing embarrassment; quiet; diplomatic. With a discreet gesture, she reminded him to mind his manners. John just doesn't understand that laughing at Mary all day is not very discreet. 2. Not drawing attention, anger or challenge; inconspicuous. Although cognate and identical in the Middle English period, the term has become distinct from discrete. --- config/chroot_local-includes/usr/share/tails/tca/main.ui.in | 2 +- po/tails.pot| 2 +- wiki/src/doc/anonymous_internet/tor.mdwn| 4 ++-- 3 files changed, 4 insertions(+), 4 deletions(-) diff --git a/config/chroot_local-includes/usr/share/tails/tca/main.ui.in b/config/chroot_local-includes/usr/share/tails/tca/main.ui.in index f77be556cd..59ca2b8e5b 100644 --- a/config/chroot_local-includes/usr/share/tails/tca/main.ui.in +++ b/config/chroot_local-includes/usr/share/tails/tca/main.ui.in @@ -1498,7 +1498,7 @@ Choose this option if you already know that you need a bridge. Otherwise, Tails 12 Tails will only connect to Tor after you configured a Tor bridge. Bridges are secret Tor relays that hide that you are connecting to Tor. -Our team is doing its best to help you connect to Tor using the most discrete types of Tor bridges. +Our team is doing its best to help you connect to Tor using the most discreet types of Tor bridges. You will have to do extra configuration if you don't know any Tor bridges yet, if you connect from a public Wi-Fi network, or if you are in the Eastern Hemisphere. True diff --git a/po/tails.pot b/po/tails.pot index 82f80aaa9f..29b9a2243a 100644 --- a/po/tails.pot +++ b/po/tails.pot @@ -3000,7 +3000,7 @@ msgid "" "are secret Tor relays that hide that you are connecting to Tor.\n" "\n" "Our team is doing its best to help you connect to Tor using the most " -"discrete types of Tor bridges.\n" +"discreet types of Tor bridges.\n" "\n" "You will have to do extra configuration if you don't know any Tor bridges " "yet, if you connect from a public Wi-Fi network, or if you are in the " diff --git a/wiki/src/doc/anonymous_internet/tor.mdwn b/wiki/src/doc/anonymous_internet/tor.mdwn index a8c2e4f16d..96741a60a6 100644 --- a/wiki/src/doc/anonymous_internet/tor.mdwn +++ b/wiki/src/doc/anonymous_internet/tor.mdwn @@ -156,7 +156,7 @@ of exit nodes of the Tor network is public. -Our team is doing its best to help you connect to Tor using the most discrete +Our team is doing its best to help you connect to Tor using the most discreet types of Tor bridges. That is why, when you decide to hide that you are connecting to Tor: @@ -185,7 +185,7 @@ types of Tor bridges. That is why, when you decide to hide that you are connecti Even someone who knows your bridge cannot know what you are doing online from Tails. -- You can only use the types of bridges that our team considers discrete enough. +- You can only use the types of bridges that our team considers discreet enough. Currently in Tails, only *obfs4* bridges hide that you are using Tor. -- 2.34.1 publickey - steve@asksteved.com - 0x38D29430.asc Description: application/pgp-keys ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.12 is out
# [Tails 5.12 is out](https://tails.boum.org/news/version_5.12/index.en.html) # New features ## Data deletion when deactivating a feature of the Persistent Storage After you turn off a feature of the Persistent Storage, you can now click the **Delete Data** button to delete the data stored for this feature. 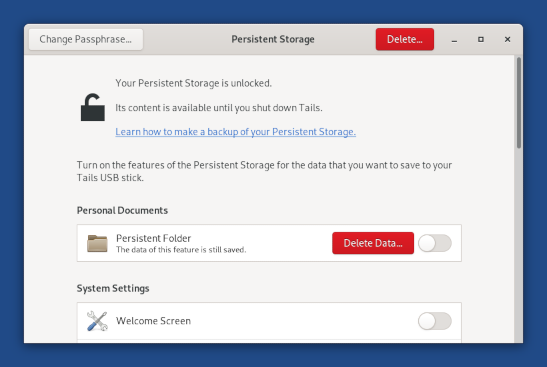 ## Passphrase suggestion when creating the Persistent Storage When creating the Persistent Storage, a random and very secure passphrase is now displayed as a suggestion:  This passphrase uses the diceware method to give very strong security guarantees while being possible to memorize. For example, a six-word passphrase like we suggest would take 3 505 years to crack at a trillion guesses a second. Learn more about the maths in [The Intercept: Passphrases That You Can Memorize -- But That Even the NSA Can't Guess](https://theintercept.com/2015/03/26/passphrases-can-memorize-attackers- cant-guess/). # Changes and updates * Update _Tor Browser_ to [12.0.5](https://blog.torproject.org/new-release-tor-browser-1205/). * Update the _Linux_ kernel to 6.1.20. This improves the support for newer hardware: graphics, Wi-Fi, and so on. * Use a new icon for the backup utility for the Persistent Storage.  # Fixed problems We fixed several reliability issues with the Persistent Storage: * We improved the error message when a feature of the Persistent Storage fails to activate from the Welcome Screen to clarify which feature is affected.  After starting Tails, the feature that failed to activate is marked as such in the Persistent Storage settings. You can try turning the feature off and on again or deleting its data to reset it entirely. 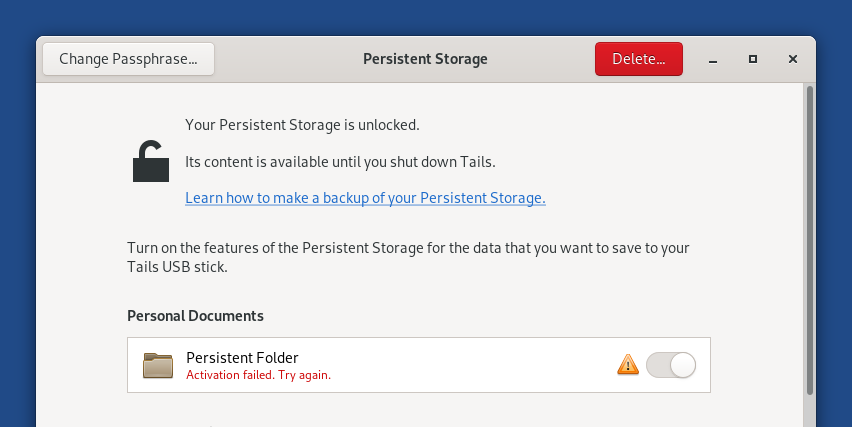 * We made the activation of the Persistent Storage more reliable in 2 error cases. ([#19376](https://gitlab.tails.boum.org/tails/tails/-/issues/19376) and [#19331](https://gitlab.tails.boum.org/tails/tails/-/issues/19331)) * We added a progress indicator while turning on a new feature to clarify that it can take some time. ([#19291](https://gitlab.tails.boum.org/tails/tails/-/issues/19291)) * We made sure that all data that is already available in Tails is really copied to the USB stick when turning on a feature. ([#19368](https://gitlab.tails.boum.org/tails/tails/-/issues/19368)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.12 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.12. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.12 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) URL: <https://tails.boum.org/news/version_5.12/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscrib
[Tails-dev] [Tails News] Tails 5.11 is out
# [Tails 5.11 is out](https://tails.boum.org/news/version_5.11/index.en.html) # New features * Tails now uses the [`zram` Linux kernel module](https://en.wikipedia.org/wiki/Zram) to extend the capacity of the computer's memory. You can run more applications or use your session for longer periods of time. Tails will handle more load before freezing and become slow more progressively. * You can record screencasts using the integrated feature of GNOME. We configured this feature to allow unlimited screencasts. See [screenshot and screencast](https://tails.boum.org/doc/sensitive_documents/screenshot_and_screencast/index.en.html). # Changes and updates * Update _Tor Browser_ to [12.0.4](https://blog.torproject.org/new-release-tor-browser-1204). * Update _Thunderbird_ to [102.9.0](https://www.thunderbird.net/en-US/thunderbird/102.9.0/releasenotes/). * Redesigned the unlocking section of the Welcome Screen.  For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.11 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.11. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.11 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.12 is [scheduled](https://tails.boum.org/contribute/calendar/) for April 18. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.11/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.10 is out
# [Tails 5.10 is out](https://tails.boum.org/news/version_5.10/index.en.html) # Changes and updates * Update _Tor Browser_ to [12.0.3](https://blog.torproject.org/new-release-tor-browser-1203). * Ask for confirmation when starting without unlocking the Persistent Storage. 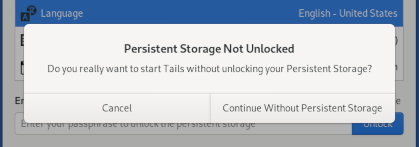 * Update our [documentation on the Persistent Storage](https://tails.boum.org/doc/persistent_storage/index.en.html). # Fixed problems * Avoid crashing when the download of an upgrade is stopped and resumed. ([#18435](https://gitlab.tails.boum.org/tails/tails/-/issues/18435)) * Solve a possible privilege escalation through a symlink attack. ([#19424](https://gitlab.tails.boum.org/tails/tails/-/issues/19424)) Dennis Brinkrolf discovered that an adversary who could already run arbitrary code as the amnesia user in Tails 5.9, could have escalated their privileges to reading arbitrary files on the system. It might have been possible to use this as part of an exploit chain to gain root privileges. ## Persistent Storage * Avoid opening the Persistent Storage settings each time after login. ([#19410](https://gitlab.tails.boum.org/tails/tails/-/issues/19410)) * Solve some cases of failure to activate the Persistent Storage by bumping the unlocking timeout to 120 seconds. ([#19432](https://gitlab.tails.boum.org/tails/tails/-/issues/19432)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.10 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.10. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.10 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.11 is [scheduled](https://tails.boum.org/contribute/calendar/) for March 14. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.10/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Question: Intel SGX disabled in BIOS
SGX is unsecure ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Little support question
Hi I’m new to tails and am having some trouble? A. It won’t connect to Wi-Fi with the right password I dk why? Connects to my phone hotspot fine though. B. I can’t find anything about the clip board icon that’s supposed to be on the top menu bar for pgp keys, I’ve searched for how to do it but can’t find anything online about it. Sent from Yahoo Mail for iPhone ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Critical Usability Issue due to which I Haven't Used Tails in Years
Hello, I've decided to forward my unanswered query to the public mailing list. Tails developers and Tails Foundations team, please check this. I welcome opinion from anyone though. Thank you in advance. (I sent this a few days ago, and saw new mail appear [here](https://lists.autistici.org/list/tails-dev.html) and [here](https://www.mail-archive.com/tails-dev@boum.org/) without this message listed, so now I created this email address and am resending this.) -- Original message - From: Date: Tue, Dec 19, 2022 at 10:42 PM UTC Subject: Fwd: Critical Usability Issue due to which I Haven't Used Tails in Years To: Hello, (I don't need PGP, please don't ignore this,) I sent the email message reproduced below and forwarding it to you since I didn't get any reply yet as of writing. I have issues that I request that you'll forward to the Tails developers. TL;DR: I wrote about three things, in this order: (1) Firstly, I wrote about the OOM-killing situation in Tails, which needs to be addressed directly by the Tails developers or the Tails Foundations team dealing with Debian/distribution work; (2) secondly, I mentioned my personal stance regarding VRAM wiping on shutdown; (3) finally, I asked whether I can do a manual upgrade of Tails from a very old version to the latest stable version. Please don't reply with instructions for debugging or troubleshooting, as they're unnecessary -- but you're free to express your disagreement with me on this, provided that you don't jump to hasty conclusions and have read my message. I'm sorry if this sounds rude, but after various email messages and WhisperBack reports over the past six or seven years or so, it feels like you're actively ignoring me. Thank you. -- Original message - From: Date: Mon, Dec 5, 2022 at 2:41 AM UTC Subject: Critical Usability Issue due to which I Haven't Used Tails in Years To: ta...@boum.org , Hello. First of all, do not dismiss this email please. I live in a free, democratic country where my human rights are respected; I don't use PGP but I don't require its use for this matter. If you're not an official member of the Tails developers team, then please forward this email to them! In the past, when I used to use Tails, I used both WhisperBack and the helpdesk mailing list to contact you regarding this matter; either you did nothing about the issue, or the helpdesk person dismissed my report as if I should do more troubleshooting or my hardware is faulty or whatever (don't remember, but it doesn't matter actually). The issue is this: Tails runs without any swap space (obviously, to maintain amnesia), the entire system may lock up at any moment due to heavy memory usage and opening of many Web browser tabs (which I usually do), the Magic Sysrq functionality of manually invoking the OOM killer in such emergency situations is disabled by default in Tails (and there's no way to enable without rebooting, and it's not recommended to enable it when connecting to the Internet as it's insecure), and Tails bundles no userspace early OOM daemon enabled out-of-the-box (such as systemd-oomd). The very least you can do is ship a new version of Tails with a slightly modified configuration value under /proc to enable the Magic Sysrq-F key combination. I request that you also consider shipping systemd-oomd enabled by default in the next major release of Tails (i.e. version 6.0). (I want to use this opportunity to express my stance regarding video RAM erasure during reboot: I don't think that the fact that something cannot be done perfectly is a good excuse to refrain from doing it at all, i.e. if something cannot be done 100% well, it's better to do even 20% of the job rather than 0%; at the same time, I don't ever expect you to ship spaghetti code, so I don't expect you to write a half-assed implementation that does 20% of the job, despite what I said earlier. I request that you research solutions that you can implement in the short term to at least try to erase the VRAM during reboot.) Related to this: I have a USB flash drive with Tails, installed using Tails installer, with an encrypted persistence, up-to-date as of around 2019-2020, with an early (stable) version of Tails 4.x if I remember right. My question is this: Can I do a manual upgrade to the latest stable version of Tails 5? (Could I do a manual upgrade to 6.x when it would be released?) When doing manual upgrades, what are the earliest versions supported? Is such an old version of Tails supported for manual upgrades using Tails installer in the latest stable Tails? Should I back up my encrypted persistence before doing anything, or do you not expect such a manual upgrade from Tails 4.x to the latest Tails 5 to cause data loss? Tails developers: please acknowledge that you received this email ASAP, at least so I would know that you got it, even if you have no answers yet. Thank you very much
[Tails-dev] Privacy
Hi there, If an adversary controls all three hops in a tor circuit. Will my traffic still be private? Thank you. Best regards Jakob Brannstrom___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tor
Dear sirs and ladies! Please, if I have questions about the tor hops and circuits, whom would you direct me to? Thank you. Best regards Jakob Brannstrom___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] obfs4 not work in Iran
Hi Tails thank you for your hard work for freedom it's been more then 4 years we use Tails and donated too. recently in Iran we faced heavy censorship because we the people of Iran fight for (woman) freedom life in Iran and the great Dictator decided to ban the internet so we can't use obfs4 bridges on Tails any more and tails default ports are banned. the only way is snowflake bridges that Tails not support it. snowflake works well on Tor browser so Please allow snowflake bridge on Tails. Again thank you for your great works ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.8 is out
# [Tails 5.8 is out](https://tails.boum.org/news/version_5.8/index.en.html) Tails 5.8 is the most important release of Tails in years. It includes both major redesign of existing features, important usability improvements, and hardened security. This work has been made possible by donations from users like you. If you like these changes and want more, donate now to fund our work in 2023. [**Donate now to fund our work in 2023.**](https://tails.boum.org/donate/index.en.html) # New features ## New Persistent Storage After 2 years of hard work, we are extremelly proud to present you a complete redesign of the Persistent Storage. The Persistent Storage hasn't changed much since its first release in 2012 because the code was hard to modify and improve. But, we learned from users that the Persistent Storage could do a lot more for you if it had more features and was easier to use. 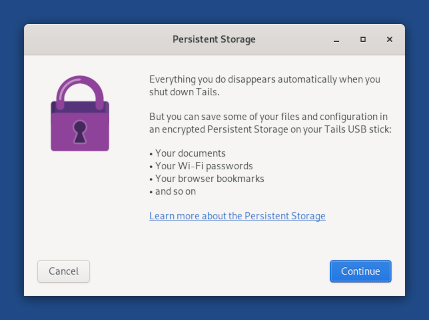 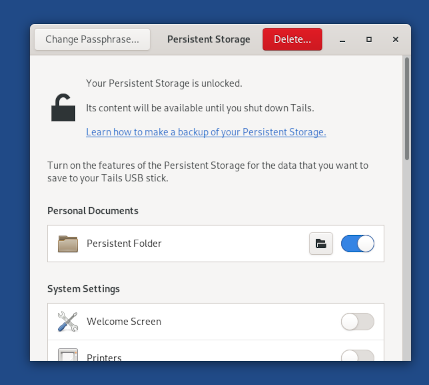 * You don't have to restart anymore after creating the Persistent Storage or each time you activate a new feature. * You can change the password of your Persistent Storage from this new application. * You can choose to create a Persistent Storage directly from the Welcome Screen, if you don't have one already. 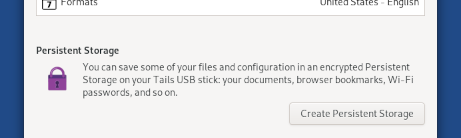 ## Wayland and better Unsafe Browser We replaced the deprecated X.Org display system with Wayland. Even if you won't notice any visual difference, Wayland brings more security in depth to Tails by making it harder for a compromised application in Tails to compromise or misuse another application. For example, since [Tails 4.8](https://tails.boum.org/news/version_4.8/index.en.html), the _Unsafe Browser_ was disabled by default because a security vulnerability in another application in Tails could start an invisible _Unsafe Browser_ , reveal your IP address, and [deanonymize you](https://tails.boum.org/doc/anonymous_internet/unsafe_browser/index.en.html#security). Wayland fixes this vulnerability and makes it safe to reenable the _Unsafe Browser_ by default. You can still disable the _Unsafe Browser_ in the Welcome Screen. Wayland also brings in other features that were not working yet in the _Unsafe Browser_ : * Sound * Uploads and downloads * Alternative input methods for Chinese and other non-Latin languages * Accessibility features like the screen reader and virtual keyboard ## QR code scanning of Tor bridges We made it easier to enter new Tor bridges in Tails by scanning a QR code. To get a QR code, you can either: * Send an empty email to [brid...@torproject.org](mailto:brid...@torproject.org) from a Gmail or Riseup email address. * Get bridges from <https://bridges.torproject.org/> and print the QR code on paper. We are aware that the QR codes that are currently provided are too big to be easy to scan. We are [working with Tor](https://gitlab.torproject.org/tpo/anti- censorship/bridgedb/-/issues/40052) to make them smaller and easier to scan. 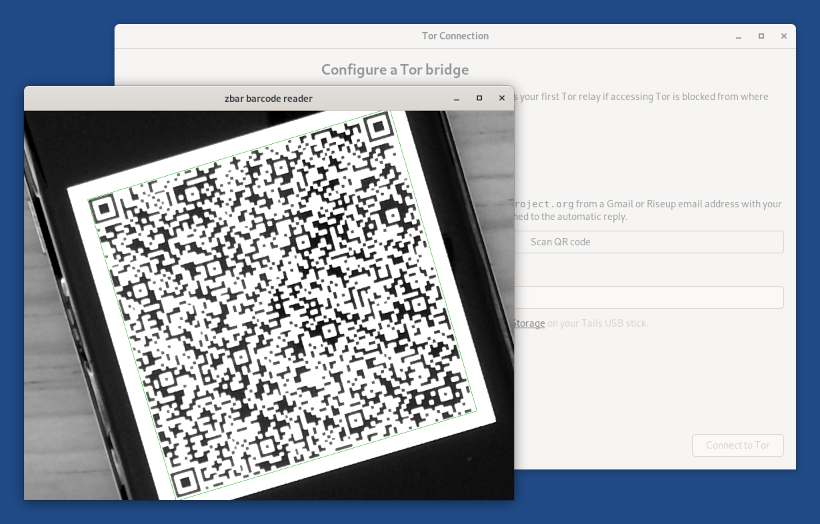 # Changes and updates * Update _Tor Browser_ to [12.0.1](https://blog.torproject.org/new-release-tor-browser-1201). * Update _Thunderbird_ to [102.6.0](https://www.thunderbird.net/en-US/thunderbird/102.6.0/releasenotes/). * Update _Tor_ to 0.4.7.12. # Fixed problems We fixed 3 usability issues in the _Tor Connection_ assistant: * Display a percentage on the connection progress bar. ([#19208](https://gitlab.tails.boum.org/tails/tails/-/issues/19208))  * Fix links to documentation. ([#19172](https://gitlab.tails.boum.org/tails/tails/-/issues/19172)) * Add a **Bridge** label in front of the line to enter a custom bridge. ([#19169](https://gitlab.tails.boum.org/tails/tails/-/issues/19169)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues * The switches that turn on and off the different features of the Persistent Storage are very slow to respond on some USB sticks. Please report on [#19291](https://gitlab.tails.boum.org/tails/tails/-/issues/19291) if this happens to you. * The top of the Welcome Screen is cut out on small displays (800×600), like virtual machines. ([#19324](https://gitlab.tails.boum.org/tails/tails/-/issues/19324)) You can press **Alt+S** to start Tails. * When using a custom Tor `obfs4` bridge, the progress bar of _Tor Connection_ sometimes gets stuck halfway through and becomes extremelly slow. ([#19173](https://gitlab.tails.boum.org/tails/tails/-/issues/19173)) To fix this, you can either: * Close and reopen _Tor Connection_ to speed up the initial connection. * Try a different `obfs4` bridge. This issue only affects outdated obfs4 bridges and does not happen with obfs4 bridges that run version
[Tails-dev] Add pass for more ways of password managment
By any change would y'all add [pass](https://www.passwordstore.org/)___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] KeepassXC
Dear Tails Boum. ## Request to update existing KeepassXC to a Later Version. Issue I'm having is the Version of KeepassXC included in the latest Releases is just one version too old (it's from *Oct 22, 2020*) I'd like to natively open Keepass 2 (.KDBX Databases.) This option is included as standard in all eight subsequent versions of [KeepassXC](https://keepassxc.org/blog/) Maybe you can suggest it and pop it in the pipeline for the next version of Tails? Many thanks for your time and consideration Kind Regards (This is a Temp email, no reply is expected or necessary) Sent with [Proton Mail](https://proton.me/) secure email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Test the new Persistent Storage and Wayland support
# [Test the new Persistent Storage and Wayland support](https://tails.boum.org/news/test_5.8-beta1/) We are extremelly proud to present you a beta of 2 new major features of Tails: a complete redesign of the Persistent Storage and the migration to Wayland, which brings a better _Unsafe Browser_. This beta also includes an easier way to enter Tor bridges in Tails by scanning a QR code. This work has been made possible by donations from users like you. If you like these changes and want more, [donate now to fund our work in 2023](https://tails.boum.org/donate/index.en.html). We will only release these features officially in Tails 5.8 (December 20), but you can try Tails 5.8~beta1 already! # New Persistent Storage Since January 2021, we have been working on a complete redesign of the Persistent Storage. The Persistent Storage hasn't changed much since its first release in 2012 because the code was hard to modify and improve. But, we learned from users that the Persistent Storage could do a lot more for you if it had more features and was easier to use. We've worked hard since 2021 to implement a [new design](https://gitlab.tails.boum.org/tails/blueprints/-/wikis/Persistent- Storage-redesign) and completely rewrite the code in Python. The new Persistent Storage doesn't require restarting after creating it or each time you activate a new feature. It will also make it easier for us to persist more settings in the future. And finally, it's looks so much better!   # Wayland and better Unsafe Browser Tails 5.8~beta1 replaces the deprecated X.Org display system with Wayland. Wayland brings more security in depth to Tails by making it harder for a compromised application in Tails to compromise or misuse another application. For example, since [Tails 4.8](https://tails.boum.org/news/version_4.8/index.en.html), the _Unsafe Browser_ is disabled by default because a security vulnerability in another application in Tails could start an invisible _Unsafe Browser_ , reveal your IP address, and [deanonymize you](https://tails.boum.org/doc/anonymous_internet/unsafe_browser/index.en.html#security). Wayland fixes this vulnerability and makes it safe to reenable the _Unsafe Browser_ by default. Wayland also brings in other features that were not working yet in the _Unsafe Browser_ : * Sound * Uploads and downloads * Alternative input methods for Chinese and other non-Latin languages * Accessibility features like the screen reader and virtual keyboard Enjoy! # QR code scanning for Tor bridges Tails 5.8~beta1 makes it easier to enter new Tor bridges in Tails by scanning a QR code. To get a QR code, you can either: * Send an empty email to [brid...@torproject.org](mailto:brid...@torproject.org) from a Gmail or Riseup email address. * Get bridges from <https://bridges.torproject.org/> and print the QR code on paper. We are aware that the QR codes that are currently provided are too big to be easy to scan. We are [working with Tor](https://gitlab.torproject.org/tpo/anti- censorship/bridgedb/-/issues/40052) to make them smaller and easier to scan.  # How to test Tails 5.8~beta1? You can either install Tails 5.8~beta1 on a new USB stick or upgrade your Tails USB stick with an existing Persistent Storage to Tails 5.8~beta1. Keep in mind that this is a test image. We tested that it is not broken in obvious ways, but it might still contain undiscovered issues. Please, report any new problem to [tails-test...@boum.org](mailto:tails- test...@boum.org) (public mailing list). # Get Tails 5.8~beta1 ## To download 5.8~beta1 ### Direct download * [For USB sticks (USB image)](http://dl.amnesia.boum.org/tails/alpha/tails-amd64-5.8~beta1/tails-amd64-5.8~beta1.img) ([OpenPGP signature](https://tails.boum.org/torrents/files/tails-amd64-5.8~beta1.img.sig)) * [For DVDs and virtual machines (ISO image)](http://dl.amnesia.boum.org/tails/alpha/tails-amd64-5.8~beta1/tails-amd64-5.8~beta1.iso) ([OpenPGP signature](https://tails.boum.org/torrents/files/tails-amd64-5.8~beta1.iso.sig)) ### BitTorrent download * [For USB sticks (USB image)](https://tails.boum.org/torrents/files/tails-amd64-5.8~beta1.img.torrent) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/torrents/files/tails-amd64-5.8~beta1.iso.torrent) ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost
[Tails-dev] Installing Tails as a Virtual Machine
I downloaded the Tails iso in order to run Tails as a virtual machine. What version of Debian Linux does Tails currently use? V/R, Race Jones 702-265-5826 Sent with [Proton Mail](https://proton.me/) secure email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.6 is out
# [Tails 5.6 is out](https://tails.boum.org/news/version_5.6/index.en.html) # Changes and updates * Update _Tor Browser_ to [11.5.5](https://blog.torproject.org/new-release-tor-browser-1155). * Update the _Linux_ kernel to 5.10.149. This should improve the support for newer hardware: graphics, Wi-Fi, and so on. # Fixed problems * When a manual upgrade is required, Tails now always points to the release notes of the latest version, instead of pointing sometimes to a deprecated version. ([#17069](https://gitlab.tails.boum.org/tails/tails/-/issues/17069)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.6 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.6. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.6 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.7 is scheduled for November 22. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.6/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.5 is out
# [Tails 5.5 is out](https://tails.boum.org/news/version_5.5/index.en.html) # Changes and updates This section will be updated soon. Sorry for the inconvenience! # Known issues Recently, a [serious kernel vulnerability](https://lwn.net/Articles/911062/) has been discovered in the Linux kernel. This is currently exploitable in Tails. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.5 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.5. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.5 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.6 is [scheduled](https://tails.boum.org/contribute/calendar/) for October 25. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.5/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] Consider adding -D_FORTIFY_SOURCE=3 to some applications (e.g., web browser)?
>> Has anyone looked into adding -D_FORTIFY_SOURCE=3 to some >> It's unclear how much the performance impact is; probably the only way to >> know is to try it. I'd argue that it's also unclear what security benefits it would bring to a web-browser :P But having it enabled in Debian by default would indeed by sweet. Do you have a link to the bug you opened intrigeri? o/ ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Javascript question
Hi, if I connect to VPN first then start Tor browser with javascript enabled to visit a clearnet website, can javascript see my true IP address? Thanks Sent with [Proton Mail](https://proton.me/) secure email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tails Safety
Hi there I am writing to find out if tails is a safe platiform to use for political activists or dissidents? I am not an expert on the Tails system itself but I did some research and came accross an article that said Tails was compromised by Facebook by exploiting a vulnerability in the video player in Tails which was used to expose users of the system. Has Tails patched that vulnerability/exploit and is the system safe to use now or can governments use the same or similar exploit to that of Facebook to find out the identity of Tails users? Best regards. Link: https://www.vice.com/en/article/dyz3jy/privacy-focused-os-tails-wants-to-know-how-facebook-and-the-fbi-hacked-it___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.4 is out
# [Tails 5.4 is out](https://tails.boum.org/news/version_5.4/index.en.html) # Changes and updates * Harden several aspects of our _Linux_ kernel. ([#18302](https://gitlab.tails.boum.org/tails/tails/-/issues/18302), [#18858](https://gitlab.tails.boum.org/tails/tails/-/issues/18858), and [#18886](https://gitlab.tails.boum.org/tails/tails/-/issues/18886)) * Disable HTTPS-only mode in the _Unsafe Browser_ to make it easier to sign in to Wi-Fi networks. * Update _Tor Browser_ to [11.5.2](https://blog.torproject.org/new-release-tor-browser-1152). * Update _tor_ to 0.4.7.10. * Update the _Linux_ kernel to 5.10.136. This should improve the support for newer hardware: graphics, Wi-Fi, and so on. It will also fix an important vulnerability ([19081](https://gitlab.tails.boum.org/tails/tails/-/blob/master/19081)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.4 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.4. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.4 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.5 is [scheduled](https://tails.boum.org/contribute/calendar/) for September 20. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.4/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Realtek™ RTL8812AU WiFi 5 (802.11ac) chipset
Is it possible to add drivers for the Alfa ac1200 wifi adapter, Realtek™ RTL8812AU WiFi 5 (802.11ac) chipset? Many of us with poor wifi reception need these long range adapters to aquire a strong signal. Failing that, is it possible to install the Realtek™ RTL8812AU WiFi 5 (802.11ac) chipset drivers during a Tails instance? Thanks very much, Cherrs! Grimm Sent with [Proton Mail](https://proton.me/) secure email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.3.1 is out
# [Tails 5.3.1 is out](https://tails.boum.org/news/version_5.3.1/index.en.html) This release is an emergency release to fix a security vulnerability in the _Linux_ kernel. # Changes and updates * Update the _Linux_ kernel to 5.10.127-2, which fixes [CVE-2022-34918](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-34918), a vulnerability that allows applications in Tails to gain administration privileges. For example, if an attacker was able to exploit other unknown security vulnerabilities in _Tor Browser_ , they might then use CVE-2022-34918 to take full control of your Tails and deanonymize you. This attack is very unlikely, but could be performed by a strong attacker, such as a government or a hacking firm. We are not aware of this attack being used in the wild. * Update _Thunderbird_ to [91.12.0](https://www.thunderbird.net/en-US/thunderbird/91.12.0/releasenotes/). # Fixed problems For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.3.1 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.3.1. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.3.1 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.4 is [scheduled](https://tails.boum.org/contribute/calendar/) for August 23. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.3.1/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.3 is out
# [Tails 5.3 is out](https://tails.boum.org/news/version_5.3/index.en.html) # Changes and updates ## Included software * Update _Tor Browser_ to 11.5.1] # Fixed problems This section will be updated soon. Sorry for the inconvenience! # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.3 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.3. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.3 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.4 is [scheduled](https://tails.boum.org/contribute/calendar/) for August 23. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.3/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.2 is out
# [Tails 5.2 is out](https://tails.boum.org/news/version_5.2/index.en.html) # Changes and updates ## Included software * Update _Tor Browser_ to [11.5](https://blog.torproject.org/new-release-tor-browser-115a13/). * Update _Thunderbird_ to [91.11.0](https://www.thunderbird.net/en-US/thunderbird/91.11.0/releasenotes/). # Fixed problems For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.2 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0 or later to 5.2. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.2 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.3 is [scheduled](https://tails.boum.org/contribute/calendar/) for July 26. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.2/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.1.1 is out
# [Tails 5.1.1 is out](https://tails.boum.org/news/version_5.1.1/index.en.html) This release fixes a [high severity security issue in tor](https://forum.torproject.net/t/stable-release-0-4-7-8/3679), that affects performance and possibly anonymity. # Changes and updates ## Included software * Update _tor_ to 0.4.7.8. * Update _Thunderbird_ to [91.10](https://www.thunderbird.net/en-US/thunderbird/91.10.0/releasenotes/). * Update the _Linux_ kernel to 5.10.120. This fixes important security issues. For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.1.1 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.x. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.1.1 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.2 is [tentatively scheduled](https://tails.boum.org/contribute/calendar/) for July 5, but it will likely be released later than that. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.1.1/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.1 is out
# [Tails 5.1 is out](https://tails.boum.org/news/version_5.1/index.en.html) This release fixes the security vulnerability in the JavaScript engine of _Firefox_ and _Tor Browser_ announced on [May 24](https://tails.boum.org/security/prototype_pollution/index.en.html). This release was delayed from May 31 to June 5 because of a delay in the release of _Tor Browser_ [11.0.14](https://blog.torproject.org/new-release- tor-browser-11014/). # Changes and updates ## Tor Connection assistant Tails 5.1 includes many improvements to the Tor Connection assistant: * The _Tor Connection_ assistant now automatically fixes the computer clock if you choose to connect to Tor automatically. This makes is much easier for people in Asia to circumvent censorship. Tails learns the current time by connecting to the captive portal detection service of [Fedora](https://getfedora.org/), which is used by most Linux distributions. This connection does not go through the Tor network and is an exception to our policy of only making Internet connections through the Tor network. You can learn more about our security assessment of this time synchronization in our [design documentation about non-Tor traffic](https://tails.boum.org/contribute/design/Tor_enforcement/#non-tor- traffic). * The time displayed in the top navigation uses the time zone selected when fixing the clock in the _Tor Connection_ assistant. In the future, we will make it possible to change the displayed time zone for everybody from the desktop ([#10819](https://gitlab.tails.boum.org/tails/tails/-/issues/10819)) and store it in the Persistent Storage ([#12094](https://gitlab.tails.boum.org/tails/tails/-/issues/12094)). * The last screen of the _Tor Connection_ assistant makes it clear whether you are connected using Tor bridges or not.  ## _Unsafe Browser_ and captive portals * We wrote a new homepage for the _Unsafe Browser_ when you are not connected to the Tor network yet. This new version makes it easier to understand how to sign in to the network using a captive portal.  * Tails now asks for confirmation before restarting when the _Unsafe Browser_ was not enabled in the Welcome Screen. This prevents losing work too easily.  ## Kleopatra * Associate OpenPGP files with _Kleopatra_ in the _Files_ browser. You can now double-click on `.gpg` files to decrypt them. * Add _Kleopatra_ to the Favorites applications.  ## Included software * Update _tor_ to 0.4.7.7. * Update _Tor Browser_ to [11.0.14](https://blog.torproject.org/new-release-tor-browser-11014/). * Update _Thunderbird_ to [91.9](https://www.thunderbird.net/en-US/thunderbird/91.9.0/releasenotes/). * Update the _Linux_ kernel to 5.10.113. This should improve the support for newer hardware: graphics, Wi-Fi, and so on. # Fixed problems * Remove the automatic selection of the option **Configure a bridge** when rolling back from the option to hide that you are connecting to Tor. ([#18546](https://gitlab.tails.boum.org/tails/tails/-/issues/18546)) * Give the same instructions on both screens where you have to configure a bridge. ([#18596](https://gitlab.tails.boum.org/tails/tails/-/issues/18596)) * Help rename the default _KeePassXC_ database to open it automatically in the future. ([#18966](https://gitlab.tails.boum.org/tails/tails/-/issues/18966)) * Fix sharing files using _OnionShare_ from the _Files_ browser. ([#18990](https://gitlab.tails.boum.org/tails/tails/-/issues/18990))  * Disable search providers in the Activities overview: files, calculator, and terminal. ([#18952](https://gitlab.tails.boum.org/tails/tails/-/issues/18952)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.1 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are available from Tails 5.0. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org
Re: [Tails-dev] Tails GitLab down since Fri May 13th 2022
> This is a short notice to let you know that Tails' GitLab is down > since Fri May 13th 2022. It's back! signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tails GitLab down since Fri May 13th 2022
This is a short notice to let you know that Tails' GitLab is down since Fri May 13th 2022. Sysadmins are aware since then and the problem is being worked on. Not much more info to provide right now. Sorry for the disruption! signature.asc Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 5.0 is out
# [Tails 5.0 is out](https://tails.boum.org/news/version_5.0/index.en.html) We are especially proud to present you Tails 5.0, the first version of Tails based on Debian 11 (Bullseye). It brings new versions of a lot of the software included in Tails and new OpenPGP tools. # New features ## Kleopatra We added [_Kleopatra_](https://tails.boum.org/doc/encryption_and_privacy/kleopatra/index.en.html) to replace the _OpenPGP Applet_ and the _Password and Keys_ utility, also known as _Seahorse_. The _OpenPGP Applet_ was not actively developped anymore and was complicated for us to keep in Tails. The _Password and Keys_ utility was also poorly maintained and Tails users suffered from too many of its issues until now, like [#17183](https://gitlab.tails.boum.org/tails/tails/-/issues/17183). _Kleopatra_ provides equivalent features in a single tool and is more actively developed.  # Changes and updates * The Additional Software feature of the Persistent Storage is enabled by default to make it faster and more robust to configure your first additional software package. * You can now use the Activities overview to access your windows and applications. To access the Activities overview, you can either: * Click on the **Activities** button. * Throw your mouse pointer to the top-left hot corner. * Press the **Super** () key on your keyboard. You can see your windows and applications in the overview. You can also start typing to search your applications, files, and folders.  ## Included software Most included software has been upgraded in Debian 11, for example: * Update _Tor Browser_ to [11.0.11](https://blog.torproject.org/new-release-tor-browser-11011). * Update _GNOME_ from 3.30 to 3.38, with lots of small improvements to the desktop, the core _GNOME_ utilities, and the locking screen. * Update _MAT_ from 0.8 to 0.12, which adds support to clean metadata from SVG, WAV, EPUB, PPM, and Microsoft Office files. * Update _Audacity_ from 2.2.2 to 2.4.2. * Update _Disk Utility_ from 3.30 to 3.38. * Update _GIMP_ from 2.10.8 to 2.10.22. * Update _Inkscape_ from 0.92 to 1.0. * Update _LibreOffice_ from 6.1 to 7.0. ## Hardware support * The new support for driverless printing and scanning in Linux makes it easier to make recent printers and scanners work in Tails. # Fixed problems * Fix unlocking _VeraCrypt_ volumes that have very long passphrases. ([#17474](https://gitlab.tails.boum.org/tails/tails/-/issues/17474)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues * _Additional Software_ sometimes doesn't work when restarting for the first time right after creating a Persistent Storage. ([#18839](https://gitlab.tails.boum.org/tails/tails/-/issues/18839)) To solve this, install the same additional software package again after restarting with the Persistent Storage for the first time. * _Thunderbird_ displays a popup to choose an application when opening links. ([#18913](https://gitlab.tails.boum.org/tails/tails/-/issues/18913)) * _Tails Installer_ sometimes fails to clone. ([#18844](https://gitlab.tails.boum.org/tails/tails/-/issues/18844)) See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 5.0 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are not available to 5.0. All users have to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 5.0 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 5.1 is [scheduled](https://tails.boum.org/contribute/calendar/) for May 31. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_5.0/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@bo
[Tails-dev] veracrypt issue
Hello Your current included version of Veracrypt supports 64 numbers and letters in the password field The new version of Veracrypt has upgraded to 128 numbers and letters So I cannot decrypt my files using your old version Could you update pls thanks very much rgds Sent with [ProtonMail](https://protonmail.com/) secure email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [PATCH] update vm-install instructions
Hi, see attached patch for a minor update to the documentation. Screenshot of what I meant: https://cloud.systemli.org/s/bWgo8qq6yZxzRzM https://cloud.systemli.org/s/EFyjRaggL5tCEL7 Warmly kwadronaut From 3ba86fc98daa043524f14298853c61dd943c7cde Mon Sep 17 00:00:00 2001 From: kwadronaut Date: Wed, 27 Apr 2022 11:52:00 +0200 Subject: [PATCH] update vm-install instructions To: tails-dev@boum.org --- .../advanced_topics/virtualization/virt-manager.mdwn | 12 1 file changed, 8 insertions(+), 4 deletions(-) diff --git a/wiki/src/doc/advanced_topics/virtualization/virt-manager.mdwn b/wiki/src/doc/advanced_topics/virtualization/virt-manager.mdwn index 2689c8bad2..7b301d5fd9 100644 --- a/wiki/src/doc/advanced_topics/virtualization/virt-manager.mdwn +++ b/wiki/src/doc/advanced_topics/virtualization/virt-manager.mdwn @@ -18,7 +18,7 @@ image|virt-manager#usb_image]]. -The following instructions have been tested on Debian 10 (Buster). +The following instructions have been tested on Debian 11 (Bullseye). Please, [[let us know|about/contact#tails-dev]] if they do not apply to Debian 11 (Bullseye). @@ -65,6 +65,8 @@ command: Running Tails from an ISO image === +1. [[Download an ISO image|install/dvd]] + 1. Start *virt-manager*. 1. Double-click on **localhost (QEMU)** to connect to the *QEMU* @@ -80,9 +82,11 @@ Running Tails from an ISO image 1. In *step 2*, choose: - **Use ISO image**, then **Browse...**, and **Browse Local** to - browse for the ISO image that you want to start from + browse for the ISO image that you want to start from. - **OS type**: **Linux** - - **Version**: **Debian Buster** + - **Version**: **Debian 10** + Note: in Debian stable (11 Bullseye), the osinfo-db doesn't contain Debian + 11. If it is more recent, you should choose Debian 11 (debian11) 1. In *step 3*, allocate at least 2048 MB of RAM. @@ -167,7 +171,7 @@ allows you to use a Persistent Storage in a virtual machine. - Expand the **Advanced options** and set **Disk bus** to **USB**. - Click **Apply**. - - Check the **Removable** check box which should appear in the same view. + - Click advanced, check the **Removable** check box which should appear in the same view. - Click **Apply** again. - Click **Begin Installation** in the top left corner to start the virtual machine. -- 2.30.2 OpenPGP_0xBD68C7AA997FA77F.asc Description: OpenPGP public key OpenPGP_signature Description: OpenPGP digital signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Tails 4.29 is out
# [Tails 4.29 is out](https://tails.boum.org/news/version_4.29/index.en.html) # New features # Changes and updates * Update _Tor Browser_ to [11.0.10](https://blog.torproject.org/new-release-tor-browser-11010). * Update _Thunderbird_ to [91.7.0](https://www.thunderbird.net/en-US/thunderbird/91.7.0/releasenotes/). * Update _obfs4_ to 0.0.12 to provide more discrete Tor bridges. ([#18800](https://gitlab.tails.boum.org/tails/tails/-/issues/18800)) * Update the _Linux_ kernel to 5.10.103. # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 4.29 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are broken from Tails 4.18 and earlier. Follow our instructions to do an [automatic upgrade from Tails 4.15, Tails 4.16, Tails 4.17, or Tails 4.18](https://tails.boum.org/doc/upgrade/error/check/index.en.html#4.18). * Automatic upgrades are available from Tails 4.19 or later to 4.29. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) * [Install from Debian or Ubuntu using the command line and GnuPG](https://tails.boum.org/install/expert/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 4.29 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 4.30 is [scheduled](https://tails.boum.org/contribute/calendar/) for May 3. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_4.29/index.en.html> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails News] Call for testing: 5.0~beta1
# [Call for testing: 5.0~beta1](https://tails.boum.org/news/test_5.0-beta1/) We plan to release Tails 5.0 on May 3 or May 31. It will be the first version of Tails based on Debian 11 (Bullseye). It brings new versions of most of the software included in Tails and some important usability improvements. You can help Tails by testing the beta for Tails 5.0 before the end of April. # Changes and upgrades * Update to Debian 11 (Bullseye) In particular this updates software included in Tails to: * GNOME 3.38 * Audacity 2.4.2 * GIMP 2.20.22 * Inkscape 1.0.2 * LibreOffice 7.0.4 * OnionCircuits 0.7 * Pidgin 2.14.1 * Thunderbird 91.7.0-2~deb11u1 * Upgrade Tor Browser to 11.0.10 * Enable driverless printing and scanning ([#18521](https://gitlab.tails.boum.org/tails/tails/-/issues/18521)) # Fixed problems * Fix locales translation in the Welcome Screen ([#18199](https://gitlab.tails.boum.org/tails/tails/-/issues/18199)) * Fix opening a Veracrypt volume with a long passphrase ([#17474](https://gitlab.tails.boum.org/tails/tails/-/issues/17474)) # Changelog For more details about what has changed in Tails 5.0~beta1, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/raw/5.0-beta1/debian/changelog). # Known issues * _WhisperBack_ fails to send error reports ([#18908](https://gitlab.tails.boum.org/tails/tails/-/issues/18908)). * _Tails Installer_ sometimes fails to install or upgrade Tails ([#18844](https://gitlab.tails.boum.org/tails/tails/-/issues/18844), [#18841](https://gitlab.tails.boum.org/tails/tails/-/issues/18841)). If this happens to you, please retry. * _Additional Software_ sometimes fails to install packages on first startup after configuring it ([#18839](https://gitlab.tails.boum.org/tails/tails/-/issues/18839)). To fix this problem, install your _Additional Software_ manually again, then restart Tails. * _OpenPGP Applet_ is not usable: its icon is not displayed ([#18845](https://gitlab.tails.boum.org/tails/tails/-/issues/18845)). * Tails 5.0~beta1 takes more time to start than previous versions ([#18906](https://gitlab.tails.boum.org/tails/tails/-/issues/18906)). * [Open issues for Tails 5.0](https://gitlab.tails.boum.org/tails/tails/-/boards/4?label_name%5B%5D=Core%20Work%3AFoundations%20Team_title=Tails_5.0) See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # How to test Tails 5.0~beta1? Keep in mind that this is a test image. We tested that it is not broken in obvious ways, but it might still contain undiscovered issues. Please, report any new problem to [tails-test...@boum.org](mailto:tails- test...@boum.org) (public mailing list) before the end of April. # Get Tails 5.0~beta1 ## To upgrade your Tails USB stick and keep your persistent storage No automatic upgrade is available, so do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To download 5.0~beta1 ### Direct download * [For USB sticks (USB image)](http://dl.amnesia.boum.org/tails/alpha/tails-amd64-5.0~beta1/tails-amd64-5.0~beta1.img) ([OpenPGP signature](https://tails.boum.org/torrents/files/tails-amd64-5.0~beta1.img.sig)) * [For DVDs and virtual machines (ISO image)](http://dl.amnesia.boum.org/tails/alpha/tails-amd64-5.0~beta1/tails-amd64-5.0~beta1.iso) ([OpenPGP signature](https://tails.boum.org/torrents/files/tails-amd64-5.0~beta1.iso.sig)) ### BitTorrent download * [For USB sticks (USB image)](https://tails.boum.org/torrents/files/tails-amd64-5.0~beta1.img.torrent) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/torrents/files/tails-amd64-5.0~beta1.iso.torrent) ## To install Tails on a new USB stick Follow our installation instructions: * [?](https://tails.boum.org/ikiwiki.cgi?do=create=news%2Ftest_5.0-beta1=install%2Fwin%2Fusb)Install from Windows * [?](https://tails.boum.org/ikiwiki.cgi?do=create=news%2Ftest_5.0-beta1=install%2Fmac%2Fusb)Install from macOS * [?](https://tails.boum.org/ikiwiki.cgi?do=create=news%2Ftest_5.0-beta1=install%2Flinux%2Fusb)Install from Linux All the data on this USB stick will be lost. # What's coming up? We will keep our [calendar](https://tails.boum.org/contribute/calendar/) updated regarding the planned release date of Tails 5.0. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. We need your help and there are many ways to [contribute to Tails](https://tails.boum.org/contribute/index.en.html) ([donating](https://tails.boum.org/donate/?r=5.0-beta1) is only one of them). Come [talk to us](https://tails.boum.org/about/contact/index.en.html#tails- dev)! URL: <https://tails.boum.org/news/test_5.0-beta1/> -- Tails News https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe, send an empty email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev m
Re: [Tails-dev] Tor on Tails issue
check if this is really a Tor connection issue, or if this is caused by mac randomization. On 3/24/22 01:31, gunsales--- via Tails-dev wrote: I've been having technical issues with using Tor on Tails. When I try to connect to Tor on Tails with obsf4 bridges on my university's wifi Tor gets blocked. This isn't an issue when I use Tor on windows with the university's wifi so I'm not sure why this occurs. I'm not sure if I need a specific bridge that can by pass the firewall or if its a problem with the OS itself or the usb I am using. If you could tell me what might being going on and what I could do about it I'd be very glad to know. -- Sent with Tutanota, the secure & ad-free mailbox. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tor on Tails issue
I've been having technical issues with using Tor on Tails. When I try to connect to Tor on Tails with obsf4 bridges on my university's wifi Tor gets blocked. This isn't an issue when I use Tor on windows with the university's wifi so I'm not sure why this occurs. I'm not sure if I need a specific bridge that can by pass the firewall or if its a problem with the OS itself or the usb I am using. If you could tell me what might being going on and what I could do about it I'd be very glad to know.-- Sent with Tutanota, the secure & ad-free mailbox. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] I lost all my data on my back SSD drive
-BEGIN PGP SIGNED MESSAGE- Hash: SHA512 I made a huge mistake uploaded the .img on my personal 500GB Samsung SSD with all my personal belonging. I'm freaking out. I didn't pay attention to what I was doing. There has to be a way to recover the lost data but my MAC isn't even reading my SSD. Please, I beg you to help me! Blue Sent with ProtonMail secure email. -BEGIN PGP SIGNATURE- Version: ProtonMail wnUEARYKAAYFAmI6oxAAIQkQGEpSDLOaD9QWIQQPErugIDwDzkQkFCUYSlIM s5oP1B3QAP42io5+ssBZuObx/qz4fZZGojRDcxMcQFUS9mV1wCczjwEAgAGX 7g4G8iok9+8OR2CY2+aN7LyIUcYHQQOP4CG3SwM= =2QOL -END PGP SIGNATURE- publickey - Imnotgivingyoumyinfo@protonmail.com - 0x0F12BBA0.asc Description: application/pgp-keys publickey - Imnotgivingyoumyinfo@protonmail.com - 0x0F12BBA0.asc.sig Description: PGP signature ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
Re: [Tails-dev] [Tails-news] Tails 4.28 is out
I successfully reproduced it: https://rebuilderd.dustri.org/api/v0/pkgs/list Congratz :) ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails-news] Tails 4.28 is out
# [Tails 4.28 is out](https://tails.boum.org/news/version_4.28/index.en.html) # Changes and updates This section will be updated soon. Sorry for the inconvenience! # Fixed problems This section will be updated soon. Sorry for the inconvenience! # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 4.28 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are broken from Tails 4.18 and earlier. Follow our instructions to do an [automatic upgrade from Tails 4.15, Tails 4.16, Tails 4.17, or Tails 4.18](https://tails.boum.org/doc/upgrade/error/check/index.en.html#4.18). * Automatic upgrades are available from Tails 4.19 or later to 4.28. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/windows/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 4.28 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 4.29 is [scheduled](https://tails.boum.org/contribute/calendar/) for April 5. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: <https://tails.boum.org/news/version_4.28/index.en.html> ___ amnesia-news mailing list amnesia-n...@boum.org https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe from this list, send an email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails-news] Ciclo de Autodefensa Digital no Brasil
Esse e um chamado aberto feito pelo Projeto Tor, Tails e Guardian Project para todos e todas as defensoras de direitos humanos, jornalistas, ativistas, feministas, defensoras de territorio, etc. Em meio a crescente ameaça a nossa segurança e liberdade digital no Brasil, sabemos que e cada vez mais importante compartilhar taticas contra a vigilancia, para a nossa autodefesa digital, escutar e empoderar as pessoas que lutam pela mudança social. **Inscreva-se at e 28 de fevereiro!** Por favor, compartilhe esse chamado com todas as pessoas que possam se interessar :)  # Se quiser aprender mais sobre autodefesa digital Estamos organizando algumas oficinas online em março e em abril: * **[Tor Browser](https://torproject.org/)** : Como navegar na Internet de maneira anonima e sem censura (para computadores). * **[Tor Browser Android](https://torproject.org/)** e **[Onion Browser](https://onionbrowser.com/)** : Como navegar na Internet de maneira anonima e sem censura (para celulares). * **[Orbot](https://guardianproject.info/apps/org.torproject.android/)** : Aumente a sua privacidade quando usa as aplicaçoes do seu celular. * **[Tails](https://tails.boum.org/)** : seu computador seguro em qualquer lugar. As oficinas sao gratuitas, mas as vagas sao limitadas. Para participar, preencha o seguinte formulario: <https://survey.tails.boum.org/index.php/146737?lang=pt-BR> Voce podera participar das oficinas de forma anonima e nao havera gravaçao. # Se quiser compartilhar a sua experiencia conosco para melhorar as nossas ferramentas Estamos interessadas em aprender como melhorar nossas ferramentas para que sejam mais uteis para o seu trabalho e suas lutas no Brasil. Organizaremos entrevistas, testes de usabilidade, questionarios e outras atividades para aprender sobre os problemas que encontram nossas usuarias no Brasil. Se quiser falar com a gente sobre o seu uso do Navegador Tor, Orbot, Onion Browser ou Tails, por favor preencha o formulario abaixo: <https://survey.tails.boum.org/index.php/146737?lang=pt-BR> URL: https://tails.boum.org/news/ciclo_de_autodefensa_digital_brasil/index.en.html ___ amnesia-news mailing list amnesia-n...@boum.org https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe from this list, send an email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails-news] Tails 4.27 is out
# Changes and updates * Update _Tor Browser_ to [11.0.6](https://blog.torproject.org/new-release-tor-browser-1106). * Update _Thunderbird_ to [91.5](https://www.thunderbird.net/en-US/thunderbird/91.5.0/releasenotes/). * Update the _Linux_ kernel to 5.10.92. This should improve the support for newer hardware: graphics, Wi-Fi, and so on. # Fixed problems * Fix connecting to a Wi-Fi network when choosing **Open Wi-Fi Settings** in the Tor Connection assistant. ([#18587](https://gitlab.tails.boum.org/tails/tails/-/issues/18587)) For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 4.27 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are broken from Tails 4.14 and earlier. Follow our instructions to do an [automatic upgrade from Tails 4.15, Tails 4.16, Tails 4.17, or Tails 4.18](https://tails.boum.org/doc/upgrade/error/check/index.en.html#4.18). * Automatic upgrades are available from Tails 4.19 or later to 4.27. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/win/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 4.27 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 4.28 is [scheduled](https://tails.boum.org/contribute/calendar/) for March 8. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: https://tails.boum.org/news/version_4.27/index.en.html ___ amnesia-news mailing list amnesia-n...@boum.org https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe from this list, send an email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Hello
Hello, I would like to participate in making Tails better. I passed LFCS (Linux Foundation Certified System Administrator) and LFCE (LF Certified System Engineer) exams last year. I also have decent knowledge of java script, node, react... Since for the moment I don't have a job I thought I put some of my time to a good cause and get some experience in the meantime :) I modified the java script code (toggle.js) in the [top starter issue](https://gitlab.tails.boum.org/tails/tails/-/issues/18469) so that one menu item hides the other... How can I submit the code proposal ? Thanks in advance Milos Sent with [ProtonMail](https://protonmail.com/) Secure Email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] Tor Browser Mystery
Sirs, I’ve noticed a problem that started right when your Tor Connection utility came out (~ 4.20), and I hope you can ease my fears about it. Because I use a cellular hotspot for internet access, I need to be careful about their monthly data limt. To that end, I have a habit of using your System Monitor/Resources/Network History to monitor my “sent” and “received” data. As you may know, the data sent when browsing is normally just a small fraction of data received, maybe 10%. MYSTERY: Ever since you launched the Tor Connection utility, every page I visit with Tor Browser adds that data count to both the “received” AND “sent” totals… as if a copy of all I view is being sent to a third party. For example, if I visit Amazon.com and browse 46.3 Mb worth of pages, then exactly 46.3 Mb of data is ALSO added to the outgoing data total. Why?? I am very concerned as to why my incoming data would need to be mirrored ANYWHERE, and am hoping you can tell me why I should not be worried about it. I’ve been using Tails for years and Tor Browser has never acted this way before, and fyi the Unsafe Browser is not affected by this, only Tor. As a work-around, I’ve been using Tails 4.19 to avoid the apparent “mirroring”. I thank you for your time, and look forward to your reply. Fred Sent with [ProtonMail](https://protonmail.com/) Secure Email.___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
[Tails-dev] [Tails-news] Tails 4.26 is out
# Changes and updates * Update _Tor Browser_ to [11.0.4](https://blog.torproject.org/new-release-tor-browser-1104). * Add a shortcut to open the _Tor Connection_ assistant when starting _Tor Browser_ if Tails is not connected to the Tor network yet.  For more details, read our [changelog](https://gitlab.tails.boum.org/tails/tails/-/blob/master/debian/changelog). # Known issues None specific to this release. See the list of [long-standing issues](https://tails.boum.org/support/known_issues/index.en.html). # Get Tails 4.26 ## To upgrade your Tails USB stick and keep your persistent storage * Automatic upgrades are broken from Tails 4.14 and earlier. Follow our instructions to do an [automatic upgrade from Tails 4.15, Tails 4.16, Tails 4.17, or Tails 4.18](https://tails.boum.org/doc/upgrade/error/check/index.en.html#4.18). * Automatic upgrades are available from Tails 4.19 or later to 4.26. You can [reduce the size of the download](https://tails.boum.org/doc/upgrade/index.en.html#reduce) of future automatic upgrades by doing a manual upgrade to the latest version. * If you cannot do an automatic upgrade or if Tails fails to start after an automatic upgrade, please try to do a [manual upgrade](https://tails.boum.org/doc/upgrade/index.en.html#manual). ## To install Tails on a new USB stick Follow our installation instructions: * [Install from Windows](https://tails.boum.org/install/win/index.en.html) * [Install from macOS](https://tails.boum.org/install/mac/index.en.html) * [Install from Linux](https://tails.boum.org/install/linux/index.en.html) The Persistent Storage on the USB stick will be lost if you install instead of upgrading. ## To download only If you don't need installation or upgrade instructions, you can download Tails 4.26 directly: * [For USB sticks (USB image)](https://tails.boum.org/install/download/index.en.html) * [For DVDs and virtual machines (ISO image)](https://tails.boum.org/install/download-iso/index.en.html) # What's coming up? Tails 4.27 is [scheduled](https://tails.boum.org/contribute/calendar/) for February 8. Have a look at our [roadmap](https://tails.boum.org/contribute/roadmap) to see where we are heading to. URL: https://tails.boum.org/news/version_4.26/index.en.html ___ amnesia-news mailing list amnesia-n...@boum.org https://www.autistici.org/mailman/listinfo/amnesia-news To unsubscribe from this list, send an email to amnesia-news-unsubscr...@boum.org. ___ Tails-dev mailing list Tails-dev@boum.org https://www.autistici.org/mailman/listinfo/tails-dev To unsubscribe from this list, send an empty email to tails-dev-unsubscr...@boum.org.
