limbonicat commented on issue #13734:
URL: https://github.com/apache/pulsar/issues/13734#issuecomment-1019767256
> Certificates signed with SHA-1 are not trusted in TLSv1.3 at all. It is
common that many clients reject certificates signed with SHA-1 also for older
TLS protocol versions.
>
> @limbonicat Can you check what certification signing algorithm do you
have? Is the certificate valid and trusted by the client?
>
> /cc @nodece @codelipenghui
@lhotari thanks for reply
1. I think my issue is not quite same as "line/armeria#2403"(his problem is
more complicated), the exception
**OPENSSL_internal:SSLV3_ALERT_CERTIFICATE_UNKNOWN** whick means client certs
auth failure or something related to TLSv1.3 (not been supported ), and this
problem is not my conern;
On the other hand ,my problem is "**OPENSSL_internal:NO_SHARED_CIPHER**"
which means client and server dont agree with cipher in handshake procedure if
im correct
> Hi! It means there are no common cipher suites between the client and the
server, which usually means one of them has an old or misconfigured SSL/TLS
setup. HTTP/2 requires both clients and servers support a minimum set of cipher
suites. Please make sure to enable those cipher suites.
2. If it's certs problem, why using same client on WIN10 done pretty well
with no exceptions?
By the way ,my self-signed certs is created by following Pulsar DOCs :
[create-tls-certificates](https://pulsar.apache.org/docs/en/security-tls-transport/#create-tls-certificates)
3. After @nodece fix(change TLS provider to JDK), the exception is gone and
i think that means the different TLS providers(Conscrypto and JDK) which
support different ciphers makes difference; and i grab traffic data shows
clearly in server hello:
- client and server finally agree with cipher "Cipher Suite:
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027)"
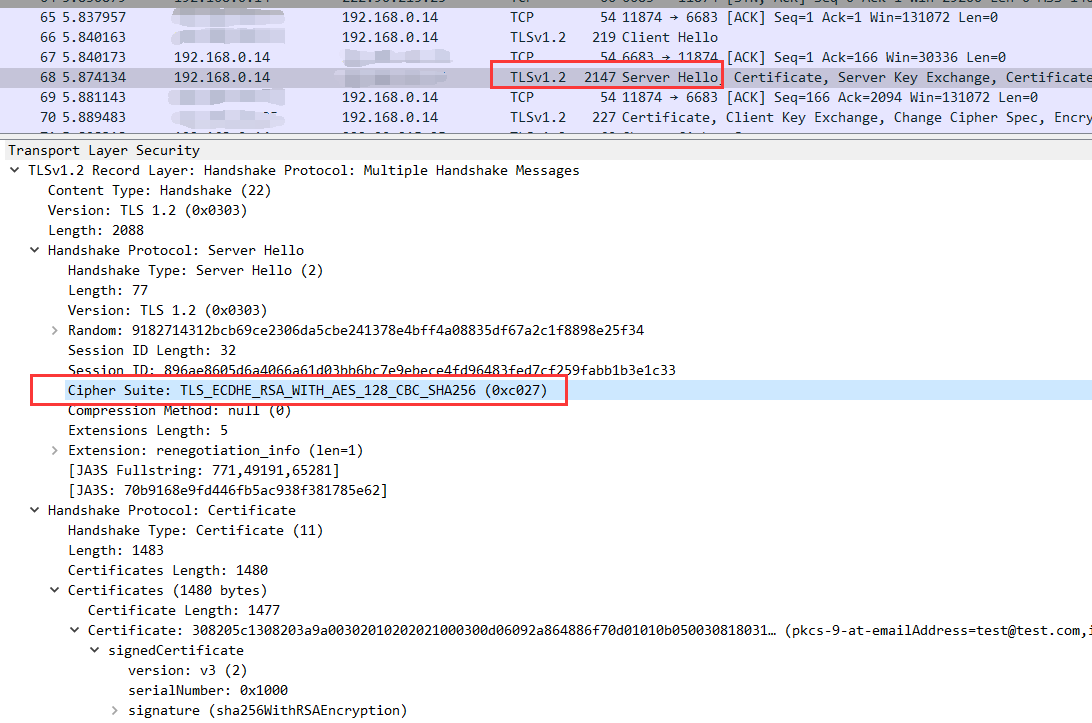
by the way **"TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 " is supported by JDK
but not supported by Conscrypto**
according to Conscrypto capabilities( and Conscrypto support
"TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA" why? i think CBC_SHA256 is more secure
than SHA-1)
--
This is an automated message from the Apache Git Service.
To respond to the message, please log on to GitHub and use the
URL above to go to the specific comment.
To unsubscribe, e-mail: [email protected]
For queries about this service, please contact Infrastructure at:
[email protected]
