kingluo commented on code in PR #9322: URL: https://github.com/apache/apisix/pull/9322#discussion_r1186610156
########## docs/en/latest/tutorials/client-to-apisix-mtls.md: ########## @@ -193,6 +193,127 @@ curl --resolve "test.com:9443:127.0.0.1" https://test.com:9443/anything -k --cer Since we configured the [proxy-rewrite](../plugins/proxy-rewrite.md) plugin in the example, we can see that the response body contains the request body received upstream, containing the correct data. +## MTLS bypass based on regular expression matching against URI + +APISIX allows configuring an URI whitelist to bypass MTLS. +If the URI of a request is in the whitelist, then the client certificate will not be checked. +Note that other URIs of the associated SNI will get HTTP 400 response +instead of alert error in the SSL handshake phase, if the client certificate is missing or invalid. + +### Timing diagram + +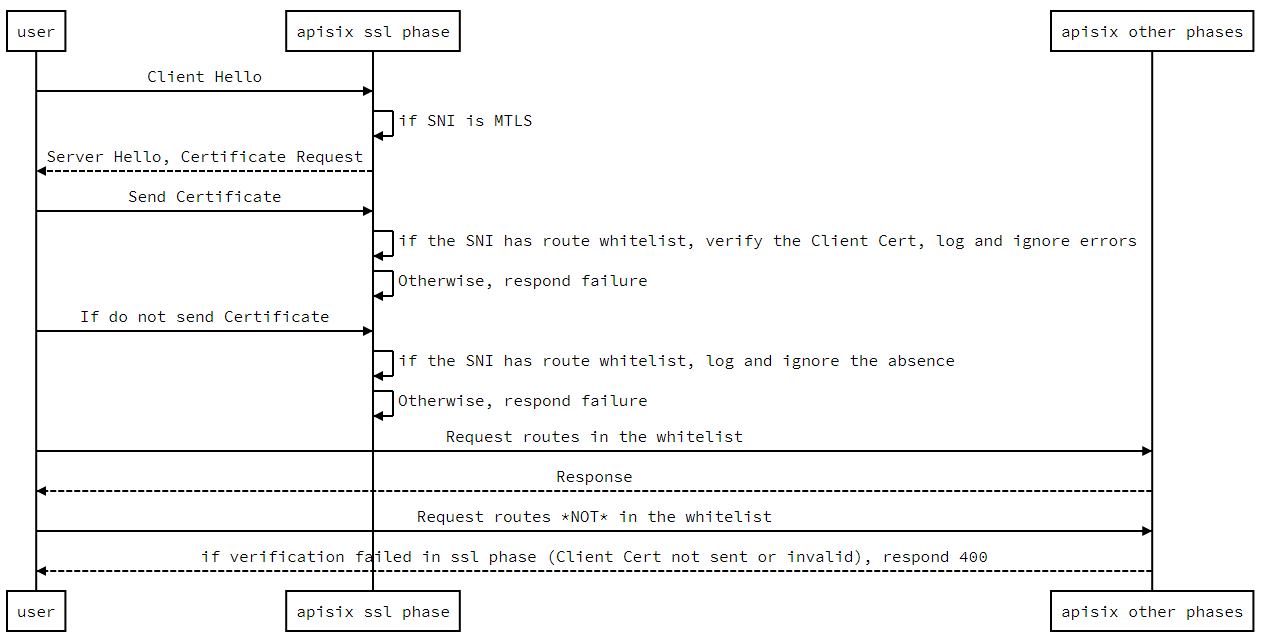 + +### Example + +```bash +curl http://127.0.0.1:9180/apisix/admin/routes/1 \ Review Comment: done ########## docs/zh/latest/tutorials/client-to-apisix-mtls.md: ########## @@ -193,6 +193,122 @@ curl --resolve "test.com:9443:127.0.0.1" https://test.com:9443/anything -k --cer 由于我们在示例中配置了 `proxy-rewrite` 插件,我们可以看到响应体中包含上游收到的请求体,包含了正确数据。 +## 基于对 URI 正则表达式匹配,绕过 MTLS + +APISIX 允许配置 URI 白名单以便绕过 MTLS。如果请求的 URI 在白名单内,客户端证书将不被检查。注意,如果针对白名单外的 URI 发请求,而该请求缺乏客户端证书或者提供了非法客户端证书,会得到 HTTP 400 响应,而不是在 SSL 握手阶段被拒绝。 + +### 时序图 + + + +### 例子 + +```bash Review Comment: done -- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. To unsubscribe, e-mail: [email protected] For queries about this service, please contact Infrastructure at: [email protected]
