Jennifer88huang commented on a change in pull request #5038: [doc] Improve Pulsar security-tls-authentication URL: https://github.com/apache/pulsar/pull/5038#discussion_r317902848
########## File path: site2/docs/security-tls-authentication.md ########## @@ -6,47 +6,48 @@ sidebar_label: Authentication using TLS ## TLS Authentication Overview -TLS authentication is an extension of [TLS transport encryption](security-tls-transport.md), but instead of only servers having keys and certs which the client uses to verify the server's identity, clients also have keys and certs which the server uses to verify the client's identity. You must have TLS transport encryption configured on your cluster before you can use TLS authentication. This guide assumes you already have TLS transport encryption configured. +TLS authentication is an extension of [TLS transport encryption](security-tls-transport.md). Not only servers have keys and certs that the client uses to verify the identity of servers, clients also have keys and certs that the server uses to verify the identity of clients . You must have TLS transport encryption configured on your cluster before you can use TLS authentication. This guide assumes you already have TLS transport encryption configured. -### Creating client certificates +### Create client certificates -Client certificates are generated using the same certificate authority as was used to generate the server certificates. +The server certificates use a certificate authority to generate the server certificates. You can use the same certificate authority as the server used to generate client certificates. The biggest difference between client certs and server certs is that the **common name** for the client certificate is the **role token** which that client will be authenticated as. -First generate the key. +First, you need to generate the key using the follwing command: + ```bash $ openssl genrsa -out admin.key.pem 2048 ``` -Similar to the broker, the client expects the key to be in [PKCS 8](https://en.wikipedia.org/wiki/PKCS_8) format, so convert it. +Similar to the broker, the client expects the key to be in [PKCS 8](https://en.wikipedia.org/wiki/PKCS_8) format, so you need to convert it by running the follwing command: Review comment: Do not use "run", you can use "enter/issue xxx command". For guidelines, see IBM Style guides. 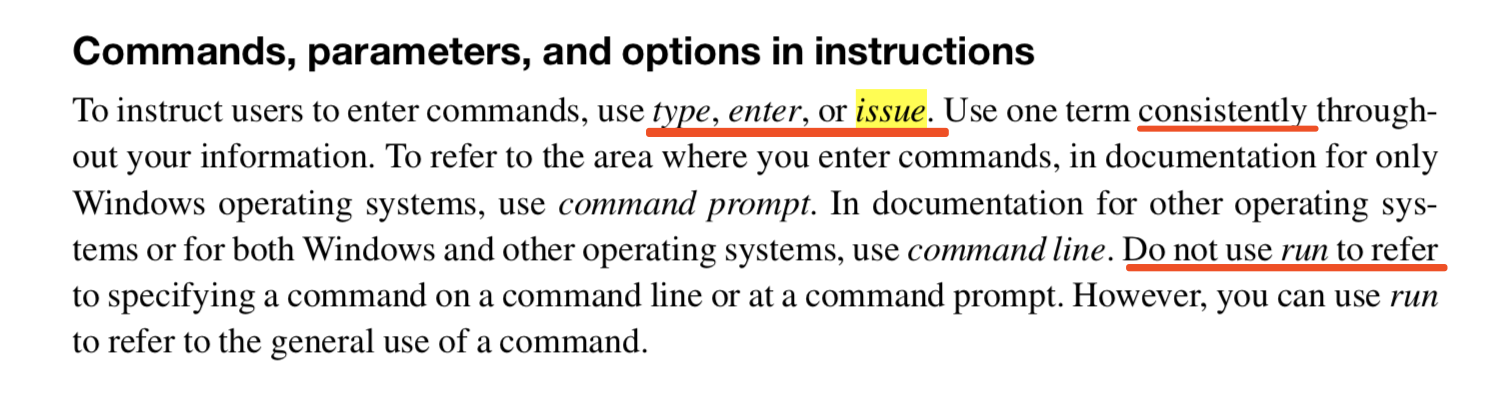 ---------------------------------------------------------------- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. For queries about this service, please contact Infrastructure at: [email protected] With regards, Apache Git Services
